A late-2017 state-sponsored cyber attacks by North Korea against South Korea not only targeted cryptocurrency users and exchanges, but also college students interested in foreign affairs, new research from Recorded Future has found.
North Korea shows no signs of letting up on its cyber war against South Korea with state-sponsored attacks against users of cryptocurrencies and exchanges that also are taking aim at new targets–college students, research released Tuesday by Recorded Future found. The attacks are continued attempts by North Korea to extract money from its southern neighbor to fund the regime of Kim Jong Un.
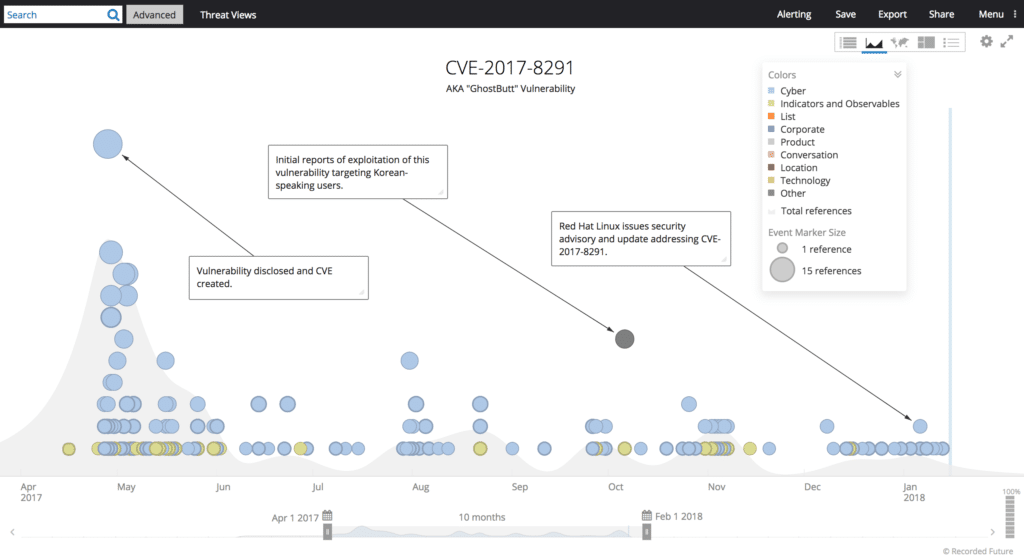
The government-sponsored Lazarus Group staged a late-2017 malware attack against South Korea in the form of a spear-phishing campaign tailored to target only users of a Korean-language word processor, Hancom’s Hangul Word Processor, the threat intelligence firm said in the new report.
North Korea aimed the attack at the usual suspects already barraged by previous cyber attacks by Kim Jong Un’s leadership—South Korean cryptocurrency users and exchanges. However, the campaign also found a new group to target in South Korean college students interested in foreign affairs, including those taking part in a group called “Friends of MOFA” or Ministry of Foreign Affairs, researchers found.
This latest action followed a series of high-profile attacks and successful thefts of South Korean cryptocurrency by North Korean actors in 2017, mainly in the form of spear-phishing campaigns against South Korean cryptocurrency exchanges, as well as Bitcoin and Monero mining. The attacks have been so prevalent that South Korea is considering a controversial ban on these xchanges.
North Korea also targeted cryptocurrency–namely, Bitcoin–for the global WannaCry ransomware attack in mid-May that infected hospitals in the United Kingdom and hundreds of thousands of other computers globally. The attack infected more than 150,000 systems–mostly in Russia, Ukraine, the European Union and Taiwan–forcing victims to pay ransom in Bitcoin.
Indeed, while North Korea bans its own citizens’ access to an unrestricted Internet, the country itself remains firmly dedicated to waging cyber warfare, with a large group of state-sponsored hackers put in place about 20 years ago to do the government’s dirty work.
[Read more Security Ledger coverage of North Korean hacking.]
The malware found in the latest attack actually shares code with previously used Destover malware, leveraged against the first-known victim of WannCry in February 2017, as well as in an attack against Sony Pictures Entertainment in 2014, according to Recorded Future.
Specifically, the late-2017 campaign—which exploited a known Ghostscript vulnerability, CVE-2017-8291—used four different lures to target Korean-speaking users of the Hangul Word Processor, a widely-used program in South Korea with the .hwp file extension, researchers said. In the past—including a phishing campaign in early 2017–North Korean hackers targeted the same program using Hangul exploits and malicious .hwp files.
Other targets of the campaign were users of the Coinlink cryptocurrency exchange and South Korean cryptocurrency exchanges at large that were hiring, researchers said. The exploit implementation included Chinese terms possibly signifying an attempted false flag or a Chinese exploit supplier, they said.
The attack shows that despite what may appear to be a warming of the chilly relations between North and South Korea–with Kim Jong Un recenty agreeing to meet his neighbors for diplomatic talks–cryptocurrencies in South Korea and elsewhere are still not safe from hackers from the North, Recorded Future researchers said.
“This late 2017 campaign is a continuation of North Korea’s interest in cryptocurrency, which we now know encompasses a broad range of activities including mining, ransomware, and outright theft,” researchers wrote in the report. “As South Korean exchanges harden their networks and the government imposes stricter regulatory controls on cryptocurrencies , exchanges and users in other countries should be aware of the increased threat level from North Korean actors.”
South Korea is, by far, the most common target of North Korean hackers. In past years, attacks believed to emanate from North Korea have targeted banks, media outlets, military contractors and civil society organizations in the South. (Check out this Security Ledger article from 2013.) However, the North has more recently begun to look outside South Korea. The Security Ledger reported in November that North Korean hackers were making forays onto the networks of U.S. defense contractors. Our report, which cited a senior executive at a prominent aerospace firm, said that the hackers appeared to be interested in finding information about weapons systems deployed on the Korean peninsula. That report was followed by a warning from the DHS and FBI about a campaign of hacks dubbed Hidden Cobra that was linked to the reclusive government of North Korea.

Pingback: Cryptocurrency Exchanges, Students Targets of North Korea Hackers | Blockchain Wiki
Pingback: James Crossan Journalism
Pingback: Lasers Eyed as Way Forward for Quantum Encryption of Data, Cryptocurrencies | The Security Ledger