In-brief: anti-virus software may go out with neither a bang nor a whimper – but utter silence. That’s if the trend towards cyber criminal actors using file-less malware continues, according to a new report.
Antivirus software may go out with neither a bang nor a whimper, but utter silence, according to a new report by the firm SentinelOne, which finds that file-less attacks are on the rise.
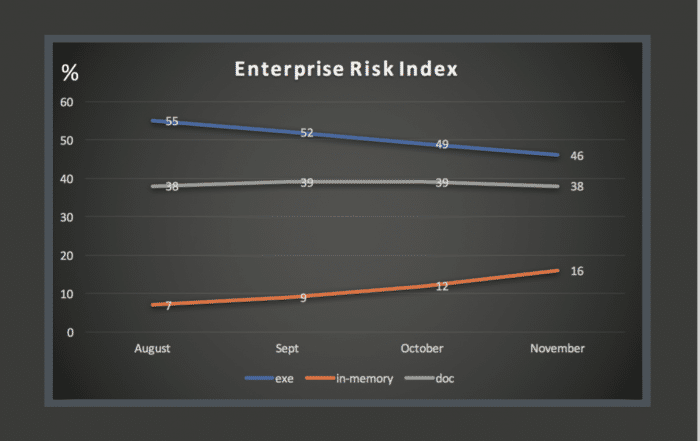
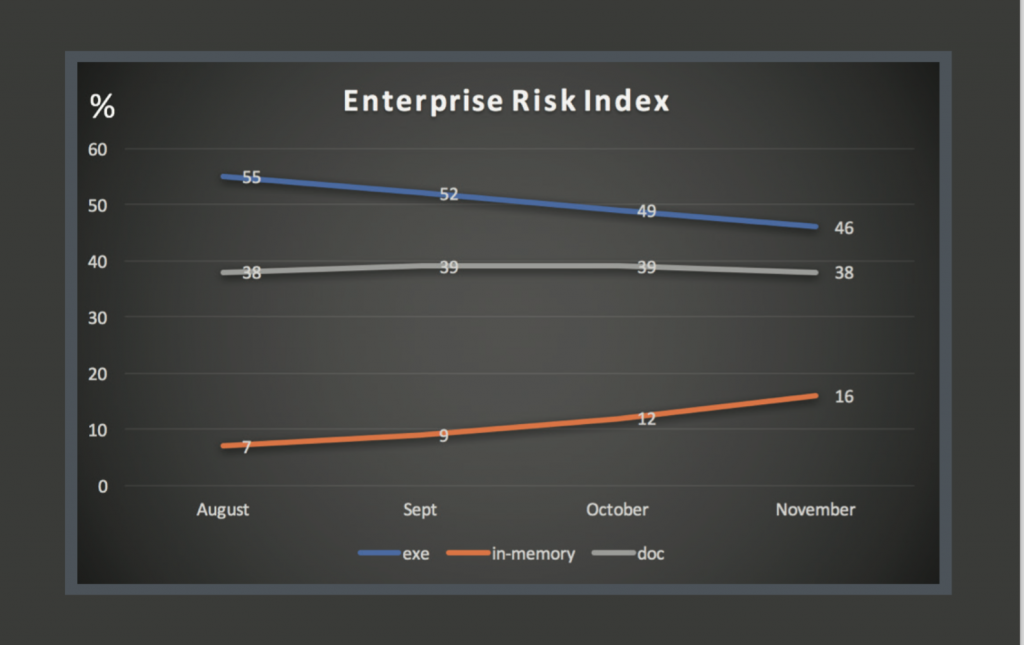
Successful attacks on endpoints that resulted from malicious executable files declined between November and August 2016 by 9% (55% to 46%) while so-called “in memory” attacks that do not place files on the infected system more than doubled, from 7% of attacks to 16%, SentinelOne reported in the company’s Enterprise Risk Index report. The data represent a trend towards more ephemeral attacks that are also harder to detect, the company said.
File-based attacks including malicious executables and document based attacks that use containers like Microsoft Word or Adobe PDF to plant malware are still the most common type of incident, SentinelOne said. Document-based attacks, for example, represented around 38% of all incidents in which attackers were able to penetrate an organization’s defenses and attack an endpoint. However, cyber criminals are finding new and more effective means to get the job done. Chief among those is the use of memory resident attacks as opposed to malicious payloads (that is: files) on the target computer. Rather than planting malware, attackers simply co-opt legitimate operating system resources like cmd.exe or Powershell, which might be invoked by a malicious document, email attachment or web link and then used to exploit the host system.
Windows Management Instrumentation – a common component of all Windows systems since the days of Windows NT and Windows 95 – is also popular, as researchers have shown in recent years how it can be subverted and used to perform system reconnaissance, execute malicious code and move laterally within a compromised organization. The use of WMI to establish “persistence” on targeted networks was famously used by those who created the Stuxnet malware and it has since been copied by other sophisticated actors, including “Cozy Bear,” a Russia-linked advanced threat group.
The shift in tactics is likely grow, as lower-skill hacking crews mimic the (successful) strategy of sophisticated groups. Already, the Angler Exploit Kit, as well as malware like Kovter, Phasebot and LatentBot have all added file-less options, SentinelOne notes. While file-less malware is less durable (rebooting a system will remove the infection) malicious actors prefer to risk having to re-infect the victim to having a malicious file detected and “disseminated to the broader security community,” SentinelOne said.
Going forward, the growing preference for file-less attacks will challenge a wide range of existing security and detection tools, from antivirus agents to network intrusion detection systems, which often rely on detecting the signature of malicious files. SentinelOne found that only half of the files it detected compromising systems were submitted to online clearing houses like VirusTotal for identification. Of those, just 20% were detected by antivirus engines. That suggests that the effectiveness of legacy tools like antivirus is low – even for the kinds of threats such tools are tailored to address.
With more than 300,000 new, unique malware samples created every day, there’s no shortage of work for traditional, signature based detection tools. But as the effectiveness of those approaches declines, the movement towards file-less options may accelerate. That may result in a not-distant future dominated by file-less malware and quiet antivirus products, keeping watch over a party that has moved elsewhere.