Cyber criminals are notoriously crafty and persistent, especially when it comes to defeating security measures created to thwart them. But a group behind a recent version of the Ramnit banking malware has raised their game to a new level: hacking the customer FAQ (frequently asked questions) document to make their malicious activity look like it was business-as-usual.
A report on Tuesday by the security firm Trusteer finds that new variants of Ramnit targeting a UK bank have added features to game a one-time-password (OTP) feature at the bank. Among other tricks, the Ramnit variant uses an HTML injection attack to alter the wording of the bank’s customer FAQ, making it seem as if prompts created by the malware were standard security features at the bank.
The report, published on the Trusteer blog, described a complex ruse in which Ramnit lies dormant on infected machines, then springs to action once a the user logs into the target bank’s website.
One time passwords are designed to protect customers from unauthorized account access or bank transfers. Customers enter a unique combination of digits, often after the bank has transmitted them to a registered cell phone.
Ramnit circumvented the OTP feature at the target bank using a s0-called ‘Man in the Browser’ attack to inject bogus HTML pages into a customer’s online banking session. The phony pages lured the customer into establishing a “OTP service phone number” for their account as an “additional security measure.” Customers are prompted to enter a “temporary number” to act as the “service phone number” and a one time password to confirm the change.
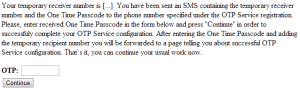
Behind the scenes, the malware selects a money mule account to transfer funds to. Leveraging its access to the account holder’s online banking session, it then initiates a money transfer to that account. The money mule account number is provided to the victim as the “service phone number.” When the customer is prompted with an out-of-band text message listing the transfer account number and the one time password to confirm the transfer, Ramnit instructs them to enter the OTP into the bank’s web site, unwittingly OK’ing the transfer to the money mule.
Clever. But – as Trusteer points out – the Ramnit authors went a step further. Wary that regular online banking customers might become suspicious of the new workflow around One Time Passwords, they included a copy of the customer FAQ on their HTML injection page, changing the wording around one time passwords as being specifically for the approval of “transactions” to being used for “operations.”
Online scammers have become increasingly sophisticated in attacks, often focusing their efforts on a single institution, lying dormant until a user accesses their account at a target institution, and then using strategies to focus attacks on small numbers of victims and keep others from noticing the ruse. First identified in 2010, Ramnit began life as a traditional Internet worm, before morphing into financial malware in 2011, Trusteer said.
Trusteer, which sells technology to protect online banking sessions, says that spotting man in the browser attacks is the best way to prevent the fraud.


