Ralph Langner, the renowned expert on the security of industrial control- and SCADA systems, warns that the latest draft of the U.S. Government’s Cyber Security Framework (CSF) will do little to make critical infrastructure more resistant to devastating cyber attacks. Writing on his blog, Langner said that a draft of the National Institute of Standards and Technology’s (NIST’s) Preliminary Cybersecurity Framework does little to compel critical infrastructure owners to improve the security of their systems, or guarantee uniform (and robust) cyber security standards in the critical infrastructure space. NIST released the latest draft of the CSF late last month (PDF). But Langner, writing on Wednesday, likened the framework to a recipe that, if used by three different chefs, produces three totally different dishes…or just a messy kitchen. “A less metaphorical words, a fundamental problem of the CSF is that it is not a method that, if applied properly, would lead to predictable results,” […]
Tag: SCADA
NIST Cyber Security Draft Framework Puts Execs In Driver’s Seat
The U.S. government’s federal technology agency has published a draft version of a voluntary framework it hopes will guide the private sector in reducing the risk of cyber attacks on critical infrastructure. The National Institute of Standards and Technology (NIST) published a draft of its Preliminary Framework to Reduce Cyber Risks to Critical Infrastructure on Monday. The document provides a guide for critical infrastructure owners of different maturity levels to begin documenting and understanding their risk of cyber attack, and – eventually – to measure their performance in areas such as asset management, threat detection and incident response. The framework was called for by Executive Order 13636, signed by President Obama in February. In that order, NIST was charged with creating a framework for sharing cyber security threat information and information on successful approaches to reduce risks to critical infrastructure. The Framework is comprised of five major cybersecurity functions: Know […]
FDA: Medical Device Makers, Hospitals Need To Boost Cyber Security
The U.S. Food and Drug Administration (FDA) has issued guidance to medical device makers and hospitals that use their products to pay more attention to cyber security and the potential for cyber attacks on vulnerable medical instruments. The FDA released its “Safety Communication for Cybersecurity for Medical Devices and Hospital Networks” on Thursday – the same day that the Department of Homeland Security’s ICS (Industrial Control System) CERT issued a warning about the discovery of hard coded “back door” passwords in some 300 medical devices from 40 separate vendors, including drug infusion pumps, ventilators and patient monitoring systems. The FDA said it expects device makers to “review their cybersecurity practices and policies to assure that appropriate safeguards are in place to prevent unauthorized access or modification to their medical devices or compromise of the security of the hospital network that may be connected to the device. Hospitals were instructed to harden […]
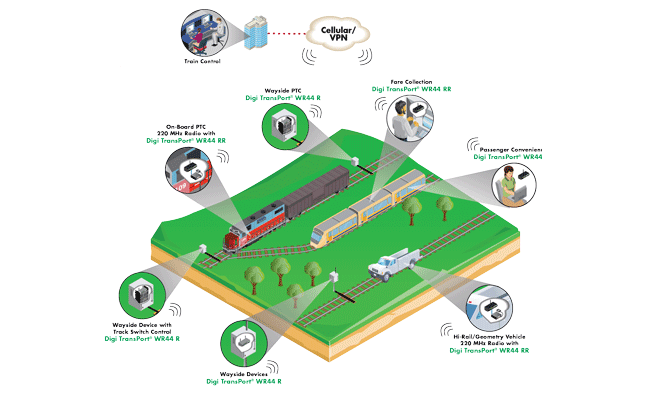
Update: Serial Server Flaws Expose Critical Infrastructure
A survey conducted by the firm Rapid 7 has found evidence that widespread vulnerabilities and insecure configuration of ubiquitous networking components known as serial port (or “terminal”) servers, may expose a wide range of companies and critical assets – including point of sale terminals, ATMs and industrial control systems – to remote cyber attacks.(*) The vulnerable devices connected hardware like retail point-of-sale systems at a national chain of dry cleaners, providing direct access to employee terminals from which customer payment information could be accessed. Other exposed systems were used to monitor the location of cargo containers, train cargo as well as HVAC and industrial control systems, Rapid7 said. In the Rapid7 survey, over 114,000 unique IPs were identified in a scan using the Simple Network Management Protocol (SNMP), the vast majority manufactured by one company: Digi International. If left unaddressed, the vulnerable devices give remote attackers direct, administrative access to hardware devices […]
UPDATE: Vulnerability In EAS To Blame For Fake Zombie Apocalypse Warning?
Editor’s Note: Updated to include information on the brand of EAS device that was compromised. – PFR 2/14/2013 OK – the good news is that the dead aren’t rising from their graves and the Zombie Apocalypse hasn’t begun (yet…). The bad news: a phony EAS (Emergency Alerting System) warning about just such a cataclysm earlier this week may have been the result of a hack of what one security researcher says are known vulnerabilities in the hardware and software that is used to distribute emergency broadcasts to the public in the U.S. The warning from Mike Davis, a Principal Research Scientist at the firm IOActive, comes just days after unknown hackers compromised EAS systems at television stations in the U.S. and broadcast a bogus emergency alert claiming that the “dead were rising from their graves” and attacking people. Published reports say that at least four television stations were the victims […]