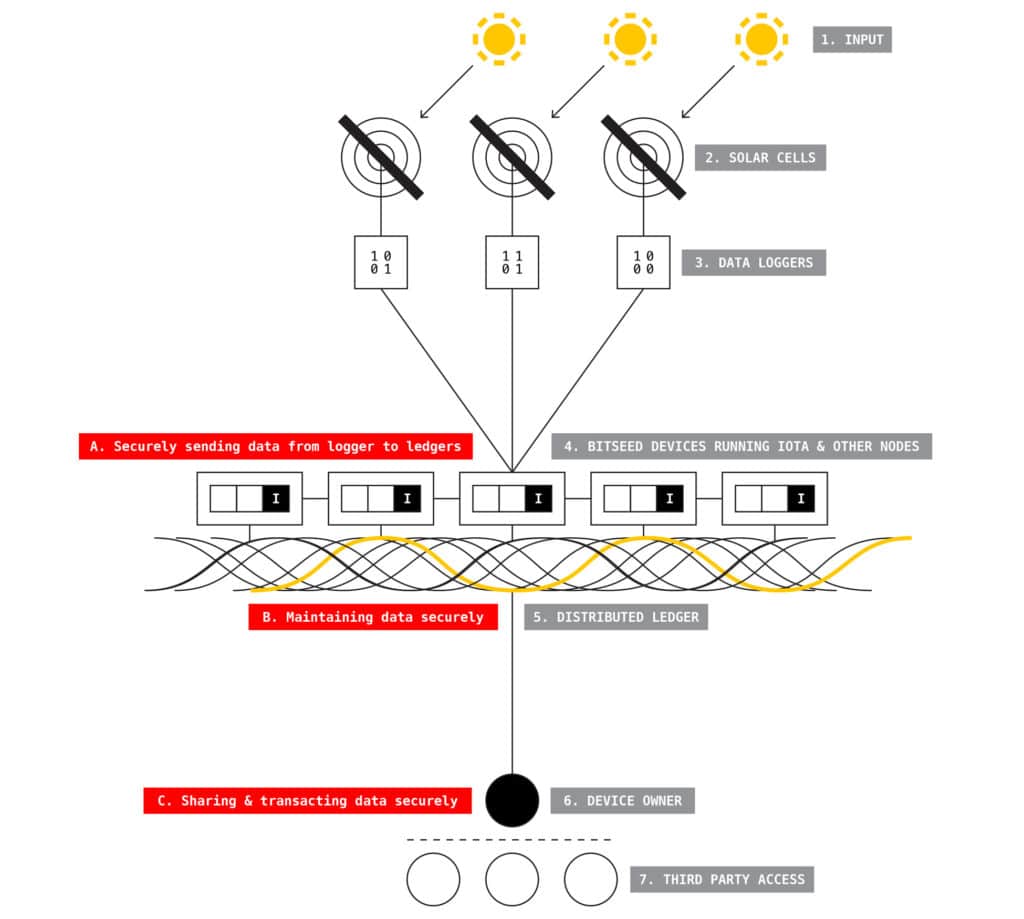
In-brief: In this Security Ledger podcast, we speak with the guys from Chain of Things, a new consortium that is investigating applications of Block Chain and related technologies to solving identity and security problems for IoT deployments.
Spoofing
Everything Tastes Better with Bluetooth: Understanding IoT Risk
In-brief: Marc Blackmer of Cisco says that, with so much promise, it can be hard to anticipate how individual or company-wide decisions to embrace the IoT might bear on cyber risk.
Android SDK Flaw Could Enable Dropbox Data Theft
In-brief: IBM researchers say they discovered a flaw in an SDK from the cloud storage firm Dropbox that could result in Android users accidentally sending their data to a Dropbox account controlled by a malicious actor.
Building an Unhackable Autonomous Vehicle – CityLab
The folks over at The Atlantic have an intriguing take on the subject of “connected vehicles” and autonomous driving. Now this is a vision that we’ve been chasing for more than 50 years (consider all the technicolor “highway of tomorrow” films from the 50s and 60s). And we’re on the cusp of realizing it. Google’s self-driving car is racking up the miles and automated features like hands free cruise control and collision avoidance are making their way into production vehicles. As Alexis Madrigal at The Atlantic’s (cool) CityLab writes, however, there’s one major fly in the ointment when you consider the super efficient, algorithmically driven road of the future: humans. Specifically: Madrigal, in the course of writing an article on how to build an ‘unhackable’ car poses a scenario that I think is very likely: humans who subvert or otherwise game vehicle automation features to suit their own needs. Imagining the orderly procession […]
Intel Promotes ‘Trustlets’ To Secure Embedded Devices
The integrity of data stored on- and transmitted between Internet-connected embedded devices is one of the biggest technical hurdles standing in the way of widespread adoption of Internet of Things technology. For one thing: embedded devices like wearable technology and “smart” infrastructure are often deployed on simple, inexpensive and resource constrained hardware. Unlike laptops or even smart phones, these are purpose-built devices that, by design, run for long periods in remote deployments, with extremely constrained features and low power consumption that is the result of limited processing power and memory. [Read Security Ledger’s coverage of connected vehicles.] Now Intel is promoting a platform that it says can bridge the gap and provide robust security features even for resource-constrained Internet of Things devices like wearables and connected vehicles. Back in April, the Intel Labs unveiled the results of joint research with Technische Universität Darmstadt in Germany. The researchers have developed a platform, dubbed TrustLite […]