In-brief: antivirus software running on a medical diagnostic computer caused the device to fail in the middle of a cardiac procedure, the FDA said.
anti malware
Report: Newly Discovered GlassRAT Lurked For Years, Undetected
In-brief: RSA Security said a newly discovered Trojan horse program may have been lurking for three years on corporate networks. Chinese nationals were the apparent target.
Pentagon looks to analog monitoring to secure IoT
In-brief: DARPA is directing $36m for the first stage of a program called LADS – Leveraging the Analog Domain for Security, which is looking into analog methods of cyber threat detection, including power consumption monitoring.
Plug and Pray? Virta Labs Using Power Analysis to Spot IoT Compromises
In-brief: A start-up, Virta Laboratories, says that its new PowerGuard technology can spot malicious software infections on any device by studying changes in how it consumes electricity. The technology has big implications for managing risk on the Internet of Things.
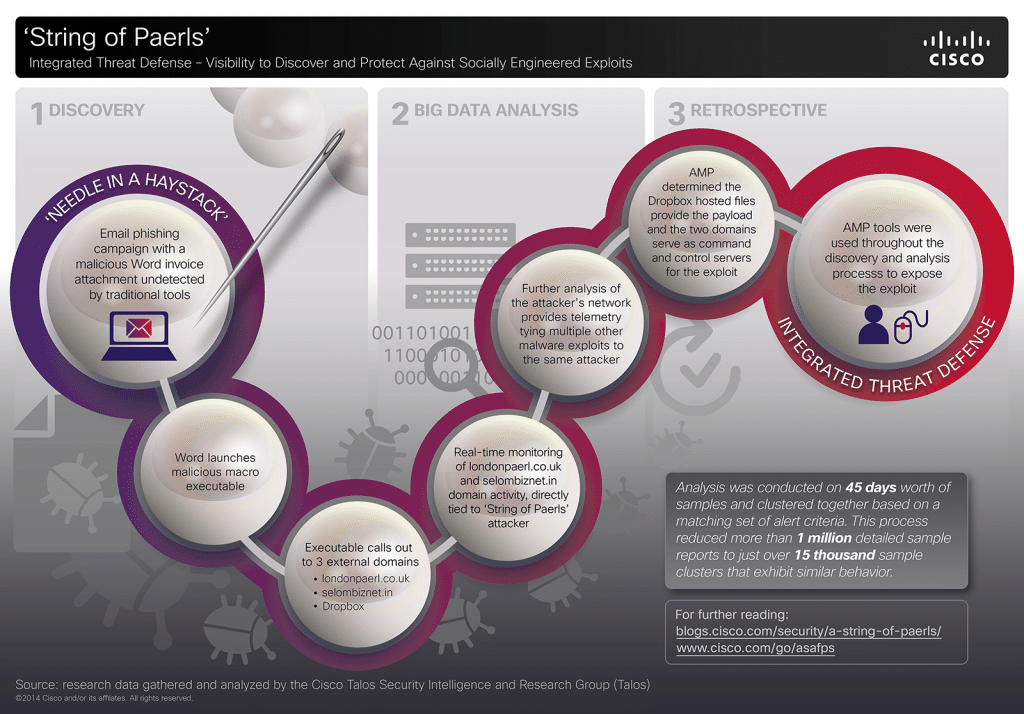
With Multi-Vector Attacks, Quality Threat Intelligence Matters
In the last year, the world’s attention has been riveted by a series of high-profile hacks of major corporations in retail, finance and the entertainment industry, among others. Each of these incidents is unique, involving different threat actors and motives. However, each of these attacks is also a sterling example of what we, at Cisco, term “multi-vector attack” that employs a range of technologies, deployed in numerous stages, to penetrate the defenses of the target organization. Here at Cisco, we have studied these attacks in-depth and have identified some commonalities among these multi-vector attack, and useful approaches to combat them. This blog post will discuss some of our findings. About Multi-Vector Attacks Any cyber attack, large or small is born from a weak link in the security chain. These weak links take many forms: poorly configured Web servers, gullible employees or vulnerable-but-common applications like Microsoft Office, Adobe Reader and Java are common examples. Multi-vector attacks […]