Venturebeat has a nice, contributed blog post by Michael Daly, of Raytheon on the lurking problem of device insecurity within the consumer Internet of Things. As Daly sees it, mass adoption of Internet of Things technologies seems destined to leave us with environments populated by low-cost and vulnerable devices whose makers don’t consider their wares valuable enough to maintain. From the article: “Offering a constant stream of security patches and updates to keep low-cost devices safe and functional for the long-term requires money. If vulnerabilities are discovered, patches or updates might be issued, but only in the first year or two. The vendor expectation is that users will need to buy a full replacement or live with the risks — not to mention that users are not very likely to manage patches and updates for non-critical devices.” In contrast to the kinds of managed networks we’re used to – with vendors […]
Products
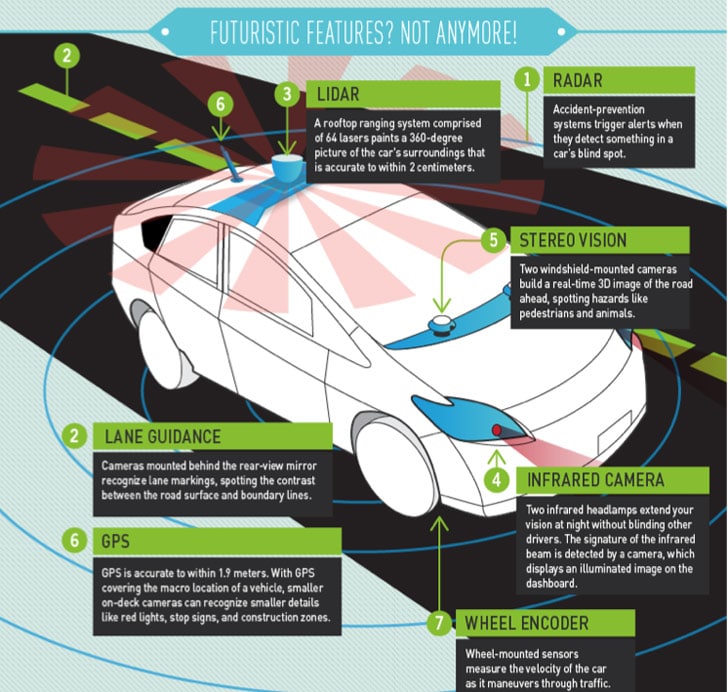
Security Ledger Talks Car Hacking on NPR’s AirTalk
Just a note to our readers that you can listen to a great conversation on hacking automobiles on Airtalk, a National Public Radio call-in talk show that airs on WPCC, Pasadena, California. Interestingly: the other expert guest on the show was none other than Chris Valasek of IOActive, one of the most recognized researchers on security vulnerabilities in modern automobiles. [Read more Security Ledger coverage of Chris Valasek’s research here.] Chris and I spoke with host Larry Mantle about the current state of affairs with regard to car hacking: what is possible (theoretically), what is practical and what are car makers doing about it. Check out our conversation via KPCC’s web site: The next frontier for computer hackers: Your car | AirTalk | 89.3 KPCC.
Big Data, Security Drive Dell In Post-PC Future
If you consider how the Internet of Things is transforming the technology industry, one of the most interesting and thought-provoking areas to pay attention to is what we might consider technology “majors” – firms like HP and IBM and Cisco that made their mark (and their hundreds of billions) serving the needs of an earlier generation of technology consumers. How these established technology firms are pivoting to address the myriad challenges posed by the “Internet of Things” tells us a lot about how the IoT market is likely to shake out for consumers and – more pressingly- the enterprise.
A BlackBerry of Smart Glasses? Lenovo Courts Enterprise Wearables Market
The blog TechBitzz has an interesting write-up from Wednesday on electronics giant Lenovo’s partnership with a 35 person New York City based start-up, Vuzix to create an enterprise-ready equivalent to Google Glass. Vuzix was known as a maker of mounted video eyewear and launched its own smart glasses in December 2013. Earlier in 2014, the two companies struck a deal to have Lenovo sell Vuzix’s M100 as a co-brand. The glasses will run Google’s Android operating system – nothing new there. But what is different is Lenovo and Vuzix’ plans for marketing the device. Rather than target the (small) fan boy and early adopter consumer market, the two companies are focusing on business customers as a natural home for connected wearables like ‘smart’ glasses. Read more Security Ledger coverage of wearables here. Lenovo, it seems, is taking a decidedly less utopian view of wearables – seeing them as a natural replacement for its bulky laptops, […]
Dusting For Malware’s Bloody Prints
Malicious software is nothing new. Computer viruses and worms have been around for decades, as have most other families of malware like remote access tools (RATs) and key loggers. But all our experience with malware hasn’t made the job of knowing when our organization has been hit by it any easier. In fact, recent news stories about breaches at Home Depot, Target, Staples and other organizations makes it clear that even sophisticated and wealthy corporations can easily overlook both the initial compromise and endemic malware infections – and at great cost. That may be why phrases like “dwell time” or “time to discovery” seem to pop up again and again in discussions of breach response. There’s no longer any shame in getting “popped.” The shame is in not knowing that it happened. Greg Hoglund says he has a fix for that latter problem. His new company, Outlier Security, isn’t “next generation […]