The official “numbers guys” (and gals) of the technology business over at IDC have just come out with a new report on The Internet of Things and it has some eye-popping numbers. Top among them: an (estimated) 30 billion autonomous “connected things” deployed by the end of this decade. The report, “Worldwide Internet of Things (IoT) 2013-2020 Forecast: Billions of Things, Trillions of Dollars” is a market outlook for the IoT ecosystem, which IDC says comprises “intelligent systems, connectivity services, platforms, analytics, and vertical applications” it also includes professional services and security for IoT infrastructures. While IP-enabled things aren’t exactly “new,” the IoT is being driven by factors that haven’t been common previously, namely: ubiquitous, wireless Internet connectivity, regardless of location, notes IDC analyst Carrie MacGillivray. IDC says the trend lines are pointing up in a serious way, with IoT related economic activity to grow at a 7.9% compound annual […]
Infrastructure
U.S. Cyber Security Framework Is Good News-For Hackers
Ralph Langner, the renowned expert on the security of industrial control- and SCADA systems, warns that the latest draft of the U.S. Government’s Cyber Security Framework (CSF) will do little to make critical infrastructure more resistant to devastating cyber attacks. Writing on his blog, Langner said that a draft of the National Institute of Standards and Technology’s (NIST’s) Preliminary Cybersecurity Framework does little to compel critical infrastructure owners to improve the security of their systems, or guarantee uniform (and robust) cyber security standards in the critical infrastructure space. NIST released the latest draft of the CSF late last month (PDF). But Langner, writing on Wednesday, likened the framework to a recipe that, if used by three different chefs, produces three totally different dishes…or just a messy kitchen. “A less metaphorical words, a fundamental problem of the CSF is that it is not a method that, if applied properly, would lead to predictable results,” […]
That ARM-Sensinode Buy: What Does It Mean For Security And IoT?
We wrote last week about the decision of chip-maker ARM to buy the small(ish) Finnish software maker Sensinode Oy, which has become a big player in the market for software that runs low power devices like embedded sensors. The deal makes sense at the 100,000 foot level – ARM makes chips that power embedded devices, Sensinode makes the software that is powered by them. Perfect. But the deal actually works at a bunch of different levels, as I learned from a conversation with Michael Koster, the co-founder and lead architect at the group The Open Source Internet of Things (OSIOT). Koster is an authority on The Internet of Things and has helped create open-source toolkits and APIs that promote interaction among intelligent devices. Koster said that ARM’s purchase of Sensinode is as much about both firms’ investment in emerging IoT standards for low-powered, intelligent devices like Constrained Application Protocol (CoAP) […]
Podcast: Made In China, Secured In The U.S.
We’ve written a lot about the threat posed by nation-state sponsored hackers to U.S. corporations and the economy. So-called “advanced persistent threat” (or APT) style attacks against corporate and government networks have been linked to the theft of sensitive data and intellectual property. Difficult as it is to stop APT attacks against networks, it’s even more challenging to identify threats one-step removed from direct attacks. Lately, attention has shifted to vulnerabilities in the supply chain of companies selling networking gear, servers and other critical IT components. Concerns about corrupted products from foreign suppliers were enough to prompt the U.S. Congress to hold hearings focused on the threat posed to government agencies by Chinese networking equipment makers like Huawei and ZTE. In this week’s podcast, The Security Ledger talks with Jerry Caponera, of Cyberpoint International. Cyberpoint is a Baltimore, Maryland firm that sells Prescient, a service that verifies where true vulnerabilities exist […]
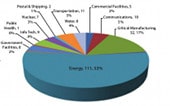
Homeland Security: Hack Attempts On Energy, Manufacturing Way Up in 2013
Attempted cyber attacks on critical infrastructure in the U.S., including energy and critical manufacturing jumped sharply in the first half of 2013, according to a just-released report from the Department of Homeland Security’s Industrial Control System Cyber Emergency Response Team (ICS-CERT). ICS-CERT said that cyber incidents across all critical infrastructure in the U.S. are on pace to double in 2013. The agency has responded to 200 such incidents so far in fiscal year 2013 (October of 2012 to May of 2013), compared to 198 incidents for all of fiscal year 2012. A majority of those incidents – 53% – were against organizations in the energy sector, ICS-CERT reported. The report is just the latest from DHS about threats to the energy sector. The agency warned energy firms after seeing a sharp jump in attacks during 2012, when attacks on energy firms accounted for around 40% of the malicious activity directed […]