I’m here at the Black Hat Briefings in Las Vegas, the U.S.’s most prominent “hacker con.” I’ll be bringing you news and updates from the show and (a bit) from DEFCON for the remainder of the week. As for the Briefings – the long and short of things is that all the buzz right now is about General Keith Alexander’s keynote speech this morning. Of course, keynotes are always a big deal, but its not even 8:00 AM and there’s a bit of a crush in the press room, with TV crews from major media outlets setting up in the Augustus ballroom, where Alexander will speak. Why? This speech is big because its one of the first – if not the first – post-PRISM public address by Gen. Alexander, who is the Commander of U.S. Cyber Command (USCYBERCOM) since the leaks by former NSA contractor Edward Snowden burst into the […]
Cyber Warfare
Emergency Alert System: Vulnerable Systems Double, Despite Zombie Hoax
You’d think that the prospect of a zombie invasion would prompt our nation’s broadcasters and others who participate in the Emergency Alert System (EAS). Just the opposite is true. Months after a bogus EAS message warning about a zombie uprising startled residents in Michigan, Montana and New Mexico, the number of vulnerable EAS devices accessible from the Internet has increased, rather than decreased, according to data from the security firm IOActive. In a blog post Thursday, Mike Davis, principal research scientist at IOActive said that a scan of the public Internet for systems running versions of the Monroe Electronics software found almost double the number of vulnerable systems in July – 412 – as were found in April, when an IOActive scan of the public Internet using the Shodan search engine found only 222 vulnerable systems. IOActive first notified Monroe Electronics about vulnerabilities in its DASDECS product in January of […]
NSA’s PRISM Puts Privacy Startup Silent Circle Into Orbit
Government surveillance has been getting a lot of attention in recent weeks, with the leak of classified information about spying by the National Security Agency using information provided by U.S. telecommunications and Internet firms including Verizon, Facebook, Google and Apple. The stories have revealed the very different legal standards that govern electronic communications and more traditional communications such as phone and postal mail. They have also put many otherwise lawful Internet users in search of technology that will keep their private conversations and thoughts well…private. That, in turn, has sparked concern in the government that civilian use of encryption will hamper lawful interception of communications. Wired.com reported last week that, for the first time, encryption thwarted government surveillance under court-approved wiretaps. That report, from the U.S. Administrative Office of the Courts (AO), said encryption was reported for 15 wiretaps in 2012, compared with just 7 wiretaps conducted during previous years. […]
Homeland Security: Hack Attempts On Energy, Manufacturing Way Up in 2013
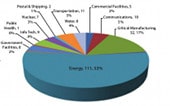
Attempted cyber attacks on critical infrastructure in the U.S., including energy and critical manufacturing jumped sharply in the first half of 2013, according to a just-released report from the Department of Homeland Security’s Industrial Control System Cyber Emergency Response Team (ICS-CERT). ICS-CERT said that cyber incidents across all critical infrastructure in the U.S. are on pace to double in 2013. The agency has responded to 200 such incidents so far in fiscal year 2013 (October of 2012 to May of 2013), compared to 198 incidents for all of fiscal year 2012. A majority of those incidents – 53% – were against organizations in the energy sector, ICS-CERT reported. The report is just the latest from DHS about threats to the energy sector. The agency warned energy firms after seeing a sharp jump in attacks during 2012, when attacks on energy firms accounted for around 40% of the malicious activity directed […]
Richard Clarke: Car Hacking Possible In Crash That Killed Michael Hastings
OK – let me start by saying that The Security Ledger isn’t a web site that’s going peddle in rumor or unfounded conspiracy theories. Period. AND let me note that Richard Clarke, the former Cyber Security Czar and U.S. National Coordinator for Security, Infrastructure Protection and Counter-terrorism just told the Huffingtonpost.com that he thinks a car hack may have played a role in the suspicious, single car accident that killed investigative reporter Michael Hastings last week. Whoa! If you don’t know, Hastings was a Polk Award winning correspondent for the web site Buzzfeed.com, where he covered national security. He died, at age 33, in a fiery, single car crash in Los Angeles last week after the Mercedes he was driving hit a tree and burst into flames. The car was almost totally destroyed. The Los Angeles County Coroner confirmed Hastings identity but said it would likely take weeks to determine the cause of […]