In-brief: 2lemetry, a Denver, Colorado-based startup that manages data from Internet connected devices said last week that it had been acquired by cloud giant Amazon.com.
Cloud hosting
Update: White House Drone Debacle Raises IoT Governance Questions
In-brief: Unmanned aerial vehicles manufactured by the Chinese firm DJI will be blocked from flying over the U.S. Capitol according to a statement by the company. The move raises important questions about the role that connected device makers will play in determining how, when and where customers use their products. (Update adds commentary from Justin Davis of Dronecamps.com – PFR Jan 29, 2015 17:30)
Research Exposes Attacks on Military, Diplomats, Executives
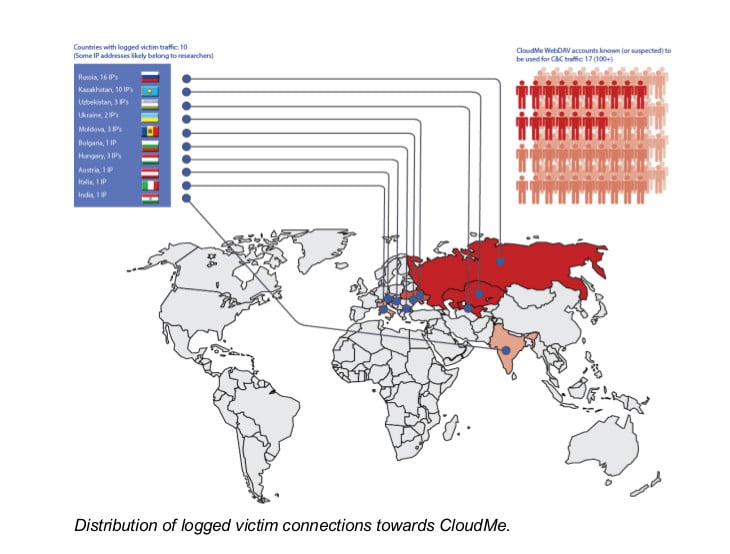
Researchers from Blue Coat Systems said on Wednesday that they have identified an online attack framework that is being used in highly targeted attacks on executives in industries like oil, finance and engineering as well as military officers, diplomats and government officials. The attacks are designed to steal sensitive information and Blue Coat, in a report, said that the attackers went to extreme lengths to cover their tracks: routing all communications between the hackers and the compromised systems they controlled through a “convoluted network of router proxies and rented hosts” in countries like South Korea. The framework, dubbed “Inception” is global in scope, but appears to have started out targeting individuals in Russia. Attacks spread via phishing e-mail messages that contained malicious attachments, including key logging tools and remote access Trojan horse programs, BlueCoat said. The company has released a full report on the incident, which can be found here. (PDF) [Read more Security Ledger coverage […]
Supply Chain Risk Escapes Notice At Many Firms
Online attacks that come by way of suppliers and other third party business partners are one of the biggest threats that modern organizations face. But too few firms are giving supply chain security the attention it deserves, a panel of legal and information security experts told attendees at a cyber security forum in Boston on Wednesday. Companies need to protect their exposure through third parties better, according to the panel: beefing up auditing of internal- and partner assets and including contractual protections that will indemnify them in the event that a breach at a supplier or business partner exposes data that materially affects their firm. The panel, “Fortifying the Supply Chain,” was part of a day long event at The Federal Reserve in Boston and sponsored by the Advanced Cyber Security Center, a technology industry consortium. It brought together top legal and information security experts, including FireEye researcher Alex Lanstein and Jim Halpert, the […]
Is IoT Innovation Outpacing Our Ability To Keep It Safe?
GigaOm has an interesting, high-level piece that looks at the issue of law, liability and the Internet of Things. The article takes off from a discussion at the Download event in New York City earlier this month, wondering whether adoption of Internet of Things technologies like wearables is starting to run far ahead of society’s ability to manage them. Specifically: is the pace of technology innovation outstripping the ability of our legal system to reign in excess and protect public safety and civil liberties? On the list of ‘what-if’s’ are some familiar questions: How to assign liability. (“If one of Google’s automated cars crashes, is it the fault of the driver or Google?”) Read more Security Ledger coverage of Internet of Things here. What responsibility to users have to take advantage of safety features in connected products? (Does a parent’s failure to password-protect a baby monitor change the manufacturer’s liability when and […]