In this episode of the podcast (#117), we go deep on one of the hottest sectors around: cyber insurance. In the first segment, we talk with Thomas Harvey of the firm RMS about the problem of “silent cyber” risk to insurers and how better modeling of cyber incidents is helping to address that threat. In part II, we invite Chip Block of the firm Evolver back into the studio to talk about the challenge that “converged” cyber physical systems pose to insurance carriers as they try to wrap their arms around their exposure to cyber risk. Editor’s note: as an experiment this week, we’re posting each interview as a separate download, to see if that makes it easier for listeners to jump to the content they’re most interested in. Use the comments section or Twitter (@securityledger) to let us know what you think or whether you prefer the single download!
Tag: patching
Podcast Episode 116: Cryptojacking and MikroTik’s Bad-Feeling Feel Good Patch Story
MikroTik is part of a bigger problem: the failure of infrastructure owners to take appropriate action to address serious security holes in products.
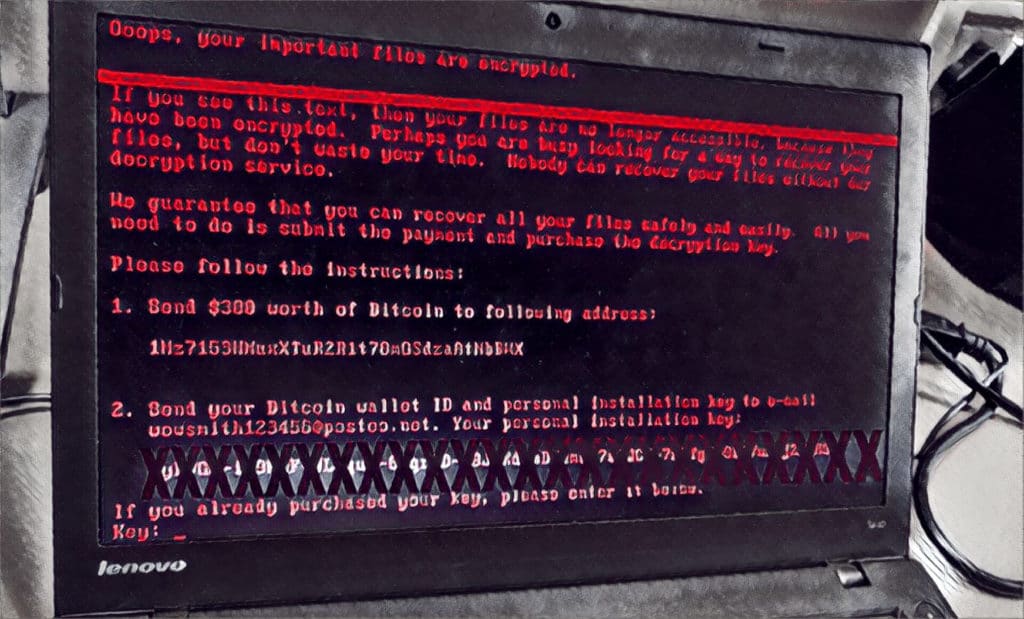
NotPetya Horror Story Highlights Need for Holistic Security
The NotPetya malware’s ability to cripple even sophisticated, global firms is a cautionary tale about the need for businesses to understand their risk and take a holistic view of security says Fadi Albatal, Chief Strategy Officer at Hitachi Systems Security.*
Podcast Episode 112: what it takes to be a top bug hunter
In this week’s episode (#112): top bug hunters can earn more than $1 million a year from “bounties” paid for information on exploitable software holes in common platforms and applications. What does it take to be among the best? We talk with Jason Haddix of the firm Bug Crowd to find out. Also: The Internet Society’s Jeff Wilbur talks about the new #GetIoTSmart campaign to educate device makers and the public about Internet of Things security.
Collection Management: a Crash-Course
Effective collection management is integral to the success of an intelligence operation. What is it and how does it work? Thomas Hofmann, the Vice President of Intelligence at Flashpoint offers a crash-course in creating an effective collection management program.