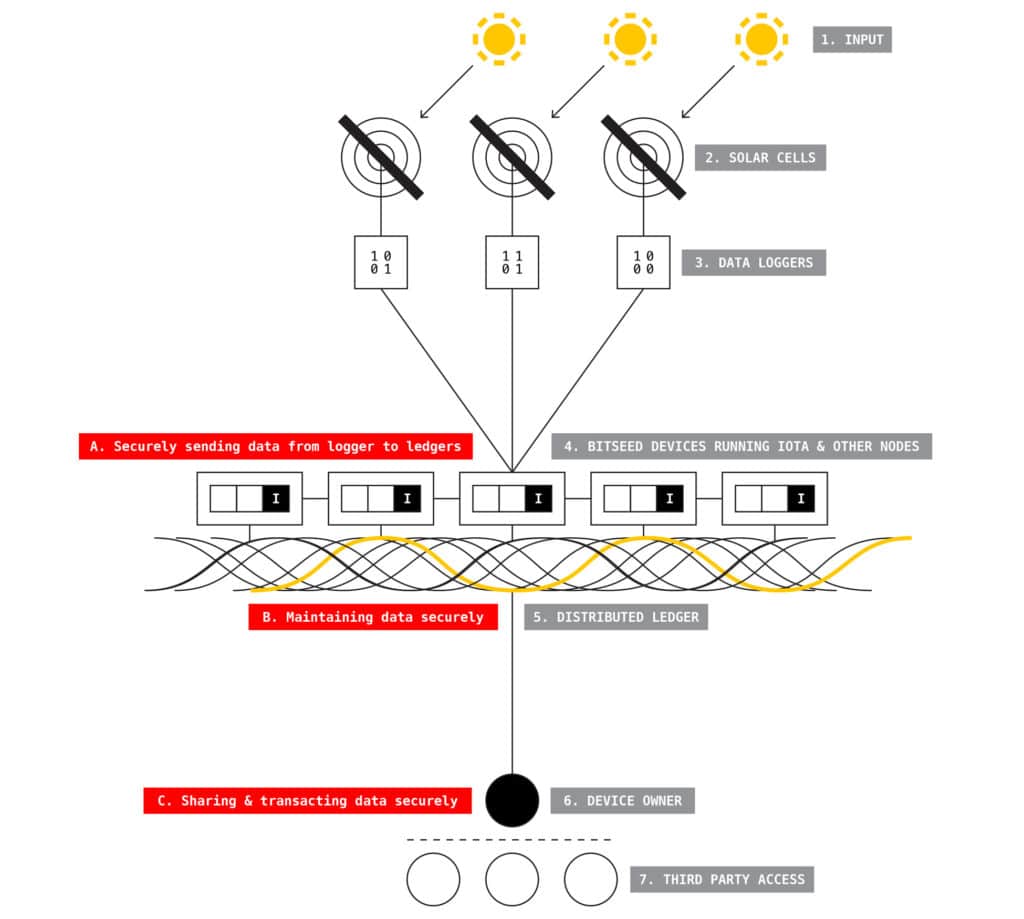
In-brief: In this Security Ledger podcast, we speak with the guys from Chain of Things, a new consortium that is investigating applications of Block Chain and related technologies to solving identity and security problems for IoT deployments.
man in the middle attack
Gee Whiz! Connected Hotel Room Controls Vulnerable to Hacking
In-brief: security researcher Matthew Garrett of the firm COREOS found that software-based lighting controls in his London hotel room, which had replaced mechanical light switches, could be easily hacked, giving him the ability to control lighting in any room in the facility.
IEEE: Security Design Flaws Woven into Wearable Tech
In-brief: The design of wearable technology risks repeating the mistakes of the past, including poor security and privacy features that could pose a risk to consumers, according to a new report by IEEE, an information technology professional organization.
Update: Hello Barbie Fails Another Security Test
In-brief: The security firm Bluebox says the mobile applications used with Hello Barbie contain security flaws that could lead to the theft of passwords and other information. Update: this story was updated to include comment from Bluebox and ToyTalk. PFR 12/4/2015
Better Web Application Security in 14 Steps
In-brief:In-brief: In this, the last in a three-part series on REST API, Neeraj Khandelwal of Barracuda Networks examines how web application security design can help secure REST APIs and provides tips for securing web applications. You can read Neeraj’s previous posts (here and here).