In brief: the Gundremmingen nuclear power plant in Germany disclosed a malicious software infection including the Conficker and Ramnit malware. The infection occurred on systems used to help move nuclear fuel rods, Reuters reported.
USB
NetUSB, IoT and Supply Chain Risk
If you want an object lesson in the dangers that await us on the Internet of Things, check out SEC Consult’s write up on NetUSB, a widely used technology developed by an obscure Taiwanese company that just happens to contain a nasty, remotely exploitable vulnerability. According to this alert, published on Tuesday, NetUSB “suffers from a remotely exploitable kernel stack buffer overflow” that could be used to run malicious code on affected devices. Even worse: the NetUSB component is ubiquitous – found in a long list of devices, from low-end wireless access points and broadband routers for small office and home office deployments to what SEC Consult called “high end devices…released very recently.” Networking devices from 26 vendors, including TP-Link, NetGear and others were found to use the NetUSB technology in their products. The vulnerability discovered by SEC Consult is straight-forward enough. According to their advisory, the NetUSB code does an inadequate […]
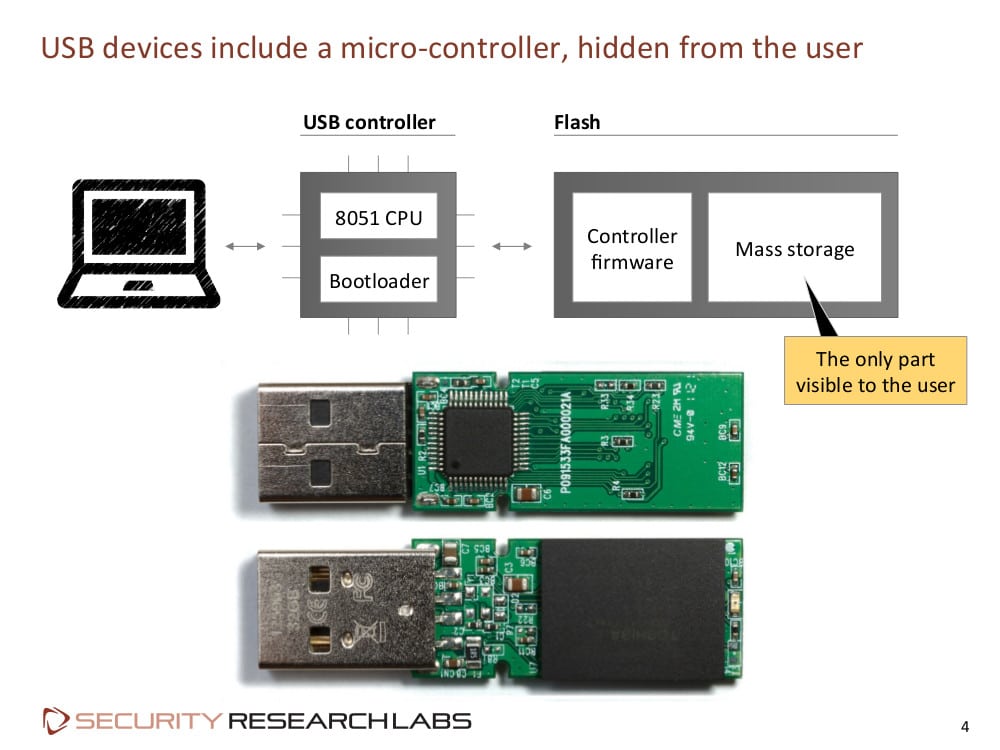
Unpatchable USB Malware Now Open Source | WIRED
Andy Greenberg over at Wired has an interesting piece of news coming out of last week’s Derbycon hacker conference in Louisville, Kentucky. According to Greenberg and Wired, researchers Adam Caudill and Brandon Wilson showed off their own version of Karsten Nohl and Jakob Lell’s BadUSB malware, and that they’d released the code on Github. Their presentation raises the stakes for USB manufacturers to fix the BadUSB problem or leave hundreds of millions of users vulnerable, Greenberg writes. At a presentation at the Black Hat Briefings in August, Nohl and Lell, both of Security Research Labs (SRLabs), showed how the controller chips inside common USB devices can be reprogrammed, allowing USB peripherals to impersonate other kinds of devices. Among other things, Nohl demonstrated how a BadUSB infected device could emulate a USB keyboard, issuing commands to a connected machine using the permissions of the logged-in user. Alternatively, an infected USB could spoof a […]