In this Spotlight edition of the podcast, we’re joined by Curtis Simpson, the Chief Information Security Officer at Armis. Curtis and I discuss the growing cyber risks posed by Internet of Things devices within enterprise networks. IoT and OT (operation technology) deployments are growing and pose challenges to organizations that are still focused on conventional IT systems and threats, and that struggle to detect such devices in their environments.
RTOS
Critical Flaws in VxWorks affect 200 Million Connected Things
Serious and exploitable security flaws in VxWorks, a commonly used operating system for embedded devices, span 13 years and could leave hundreds of millions* of connected devices vulnerable to remote cyber attacks and hacks. The security firm Armis on Monday published a warning about 11 critical, zero day vulnerabilities in the VxWorks operating system, which is owned and managed by the firm Wind River. The vulnerabilities expose more than 200 million devices and could allow attackers to remotely take control of everything from networked printers and security appliances to industrial and medical devices, according to Ben Seri, the Vice President of Research at Armis. Move over, EternalBlue! At least a couple of the flaws were described as “more serious” than EternalBlue, the Microsoft Windows flaw that powered both the WannaCry and NotPetya malware outbreaks. SCADA and industrial control system devices, healthcare devices like patient monitors and MRI machines, as well […]
Google’s Android Things IoT Platform Promises Secure Update
In-brief: Google on Tuesday unveiled Android Things, a new Internet of Things platform based on its Android mobile operating system and earlier forays into the Internet of Things operating space.
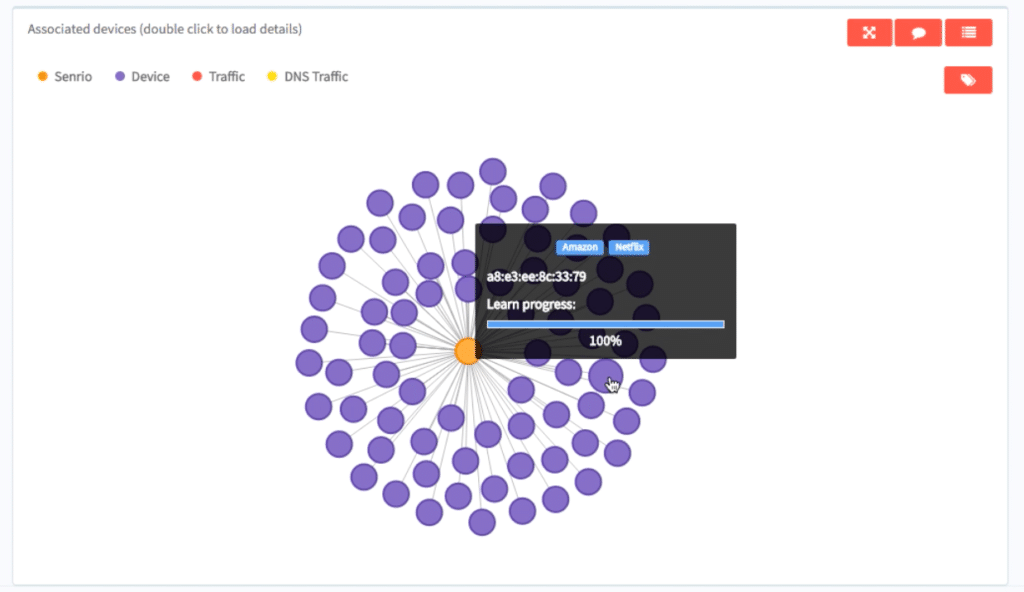
Startup Senrio Sniffs Out Stealth IoT Devices on your Network
In-brief: A new start-up, Senrio, unveiled its Sensor this week: a new security monitoring tool that can identify and monitor embedded devices connected to your network and spot anomalous or malicious behavior.