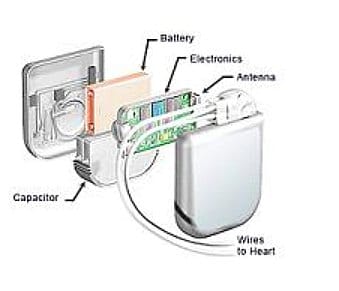
In this Spotlight Podcast, sponsored by Synopsys: In the wake of a presentation at Black Hat about security flaws in implantable pace maker devices, Synopsys Principal Consultant Dan Lyon joins us to talk about why medical device makers struggle to make their connected medical devices more secure. Dan and I discuss some of the flaws in the approach that medical device makers take to security, and how manufacturers can take a page out of their own book: applying the same standards to cyber security as they do to – say- device safety.
defibrillator
A Year Later: FDA approves Software Fix for Security Flaws in Pacemakers
In-brief: The FDA as approved a software update to software security holes in pacemakers made by Abbott. But doctors and patients will have to weigh the risks of apply the patch.
Code Blue: 8k Vulnerabilities in Software to manage Cardiac Devices
Software used to remotely program implantable cardiac devices by a number of vendors is rife with exploitable software vulnerabilities that leave the devices vulnerable to attacks and compromise, according to a report by the firm Whitescope Inc.
Update: FDA says St. Jude Medical knew about Device Flaws 2 Years Before Muddy Waters Report
In-brief: In a damning report, the FDA said that St. Jude Medical* knew about serious security flaws in its implantable medical devices as early as 2014, but failed to address them with software updates or other mitigations, or by replacing those devices. (Editor’s note: updated to include a statement from Abbott and comment from Dr. Kevin Fu. – PFR April 14, 2017)