Andrey Belenko had what you might call a ‘brush with infamy’ earlier this week after a presentation he took part in on the security of Apple’s iCloud became a set piece in the news media scramble to identify the source of a huge trove of leaked celebrity photos – many depicting Hollywood A-List stars in various states of undress. “It’s not the kind of attention you want to receive,” said Belenko, a security researcher with the firm ViaForensics. “It’s all really creepy stuff.” Belenko’s link to the celebrity hacking scandal was a matter of happenstance. He was scheduled to give a presentation at a small, St. Petersburg multi-media conference, Chaos Constructions, over the weekend. Belenko was presenting research he had conducted a year earlier on the security of Apple’s KeyChain technology and iCloud – a talk he had given twice before in the last year. Prior to his talk, Belenko […]
Via Forensics
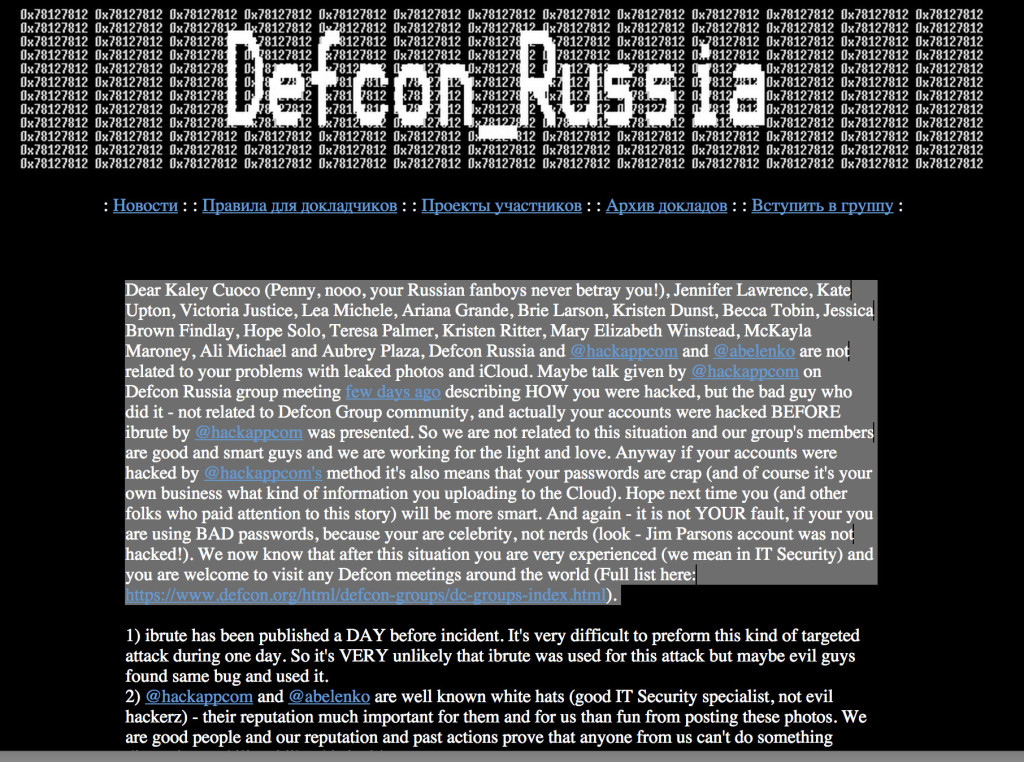
Hack Tool Authors Deny Link To Celeb Photo Leaks
With some of Hollywood’s biggest stars issuing statements on Monday condemning the leak of personal photographs online, attention has turned to identifying the source of the leaks. But more than 24 hours after the photos appeared, there are more questions than answers about its source. Early attention has focused on an automated tool that exploited an apparent vulnerability in Apple’s FindMyiPhone feature. But by Monday, there were denials from the makers of that tool that it played any role in the massive privacy breach that saw photos of A-list celebrities like Jennifer Lawrence, Kate Upton and others leaked online. Within hours of the photos’ appearance on the image sharing site 4chan, attention shifted to the cause of the leak and the coincidence of the leaked photos with the publication of iBrute, a simple tool available on GitHub in recent days. According to this published report by Owen Williams over at TheNextWeb, the […]
New Mobile Malware Taps Ad Networks To Spread
It was only a couple weeks back that we wrote about new research from the folks at WhiteHat Security that posited a way for mobile ad networks to be gamed and used to distribute malicious code. Now it looks as if the bad guys were one step ahead, as researchers at Palo Alto Networks reveal new type of malicious Android malware that uses mobile ad networks to infect vulnerable devices. Palo Alto described the new, malicious mobile software, dubbed “Dplug,” in a blog post on Monday. The company said the malware authors appear to be leveraging second tier mobile ad networks, mostly in Russia and the former Soviet Republics), to distribute their wares. The Dplug malware takes advantage of the deep integration between mobile applications and mobile advertising networks to gain a foothold on infected devices, then send out messages to premium SMS services to generate money for the fraudsters, according […]
Android Founder: Install Base Fragmentation No Big Deal
Android owners who were hoping that Google might be on the cusp of cleaning up its balkanized install base won’t be cheered by the latest word from on high: Android co-founder and Google Ventures Partner Rich Miner thinks it’s no big deal. Speaking on Tuesday at an event in Boston, Miner said that fragmentation of the install base was inevitable, given the number and variety of Android devices that are being adopted, according to a report by Xconomy.com.The statement comes as Google is dealing with the fallout from a newly disclosed vulnerability affecting almost all Android platforms that could allow attackers to fool Android into installing and running compromised applications. Miner was speaking at a Mobile Summit forum hosted by the Massachusetts Technology Leadership Council. He made his statements while being interviewed by renowned technology journalist and columnist Scott Kirsner (@ScottKirsner) of the Boston Globe on the (evergreen) topic “What’s […]
Updated: Exploit Code Released For Android Security Hole
A security researcher has published what he claims is a proof of concept program that exploits a security hole that affects hundreds of millions of Android mobile devices.* Pau Oliva Fora, a security researcher for the firm Via Forensics, published a small, proof of concept module that exploits the flaw in the way Android verifies the authenticity of signed mobile applications. The flaw was first disclosed last week by Jeff Forristal, the Chief Technology Officer at Bluebox Security, ahead of a presentation at the Black Hat Briefings in August. Oliva Fora posted his “quick and dirty” proof of concept on GitHub, a code sharing website, on Monday. The simple program leverages APKTool, a common, open source tool for reverse engineering Android applications – decompiling and then recompiling their contents. APKTool is widely used for analyzing and making modifications to closed binaries. His script allows a user to select an Android […]