With some of Hollywood’s biggest stars issuing statements on Monday condemning the leak of personal photographs online, attention has turned to identifying the source of the leaks. But more than 24 hours after the photos appeared, there are more questions than answers about its source.
Early attention has focused on an automated tool that exploited an apparent vulnerability in Apple’s FindMyiPhone feature. But by Monday, there were denials from the makers of that tool that it played any role in the massive privacy breach that saw photos of A-list celebrities like Jennifer Lawrence, Kate Upton and others leaked online.
Within hours of the photos’ appearance on the image sharing site 4chan, attention shifted to the cause of the leak and the coincidence of the leaked photos with the publication of iBrute, a simple tool available on GitHub in recent days. According to this published report by Owen Williams over at TheNextWeb, the app allows users to carry out brute force attacks against Apple iCloud accounts. The app reportedly worked by taking advantage in a flaw in Apple’s FindMyiPhone feature, which allowed unlimited login attempts.
[Read Security Ledger coverage of password insecurity here.]
Brute force attacks are one of the simplest forms of hacking, in which attackers repeatedly guess at a password, often with the help of scripts or automated tools. Eliminating them is as easy as setting a login attempt counter that suspends accounts after a pre-determined number of failed logins, or prevents additional login attempts for a set period. Apple has long had such protections for iCloud and other Apple services. However, the company apparently failed to extend the password retry limit to the FindMyiPhone feature. A patch issued by Apple on Monday has closed that loophole.
The publication of iBrute by HackApp followed a talk by security researcher Andrey Belenko of the firm ViaForensics at Chaos Constructions, a St. Petersburg, Russia, security conference. Belenko’s talk, “Internals and Safety in iCloud Keychain” focused on a range of security problems with iCloud, including the vulnerability allowing brute force password attacks, which would give an attacker access to a user’s iCloud applications and data, including photos.
Posts like this one at Detectify.com, theorized that iBrute, combined with the public availability of both e-mail addresses and passwords from prior data breaches (like RockYou.com) could be used to narrow password guesses against high value accounts, like those of the Hollywood celebrities.
However, those theories have holes in them. Among other inconsistencies: hackers claimed to have obtained videos of celebrities – content that would not have been stored on iCloud.
The link to iBrute and Belenko’s Chaos Constructions talk was quickly dismissed by conference organizers and iBrute’s authors. In a post Monday, HackApp’s authors denied categorically that their software played a role in the attacks.
“We only described the way HOW to hack AppleID,” the post reads. “Stealing private ‘hot’ data is outside of our scope of interests. We discuss such methods of hacks in our’s narrow range, just to identify all the ways how privacy can by abused.”
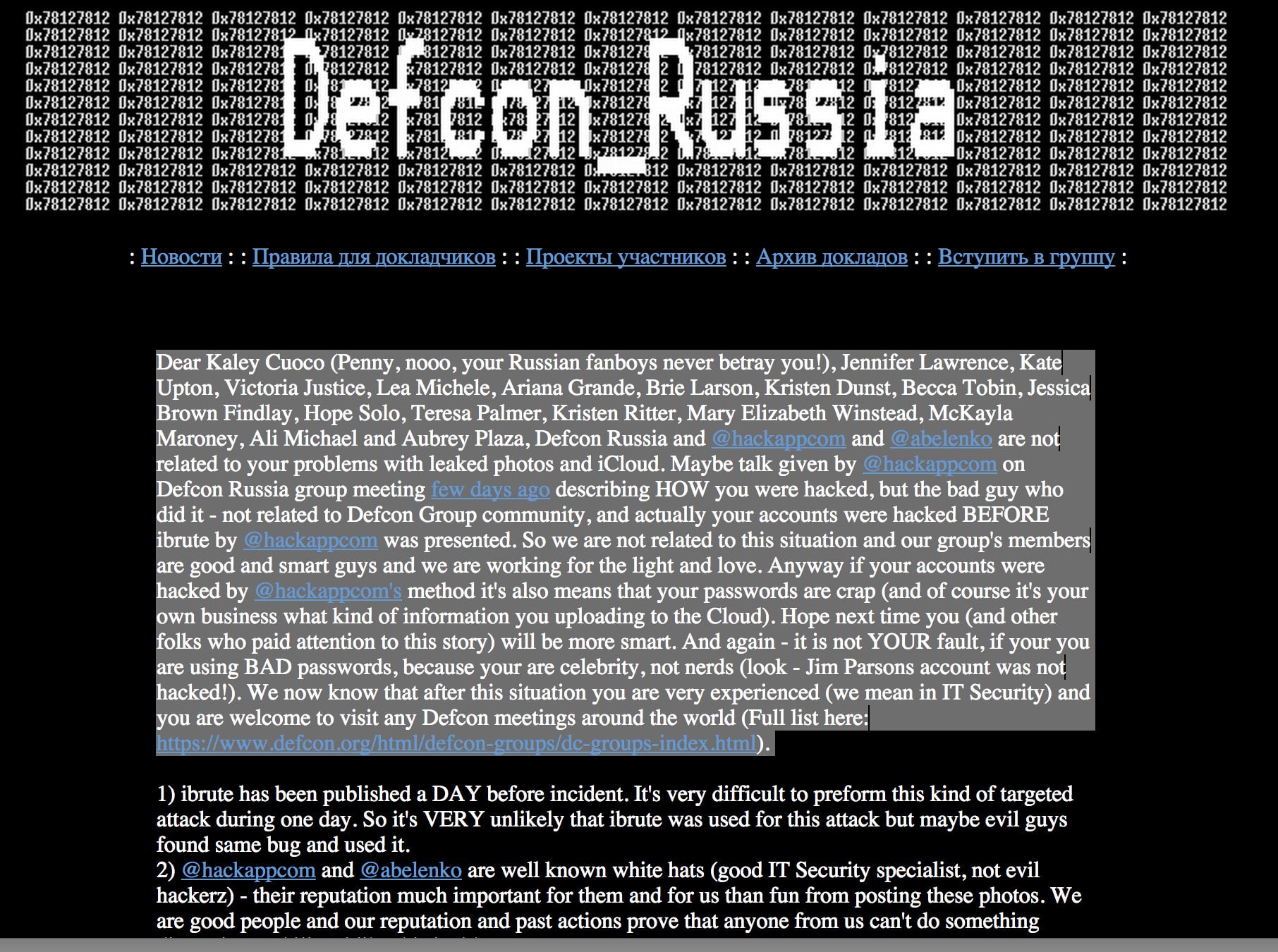
A message on the DEFCON.RU blog addressed to the victims of the attack claimed that Defcon Russia as well as HackApp and Belenko “are not related to your problems with leaked photos and iCloud.”
“Maybe talk (sp) given by @hackappcom on Defcon Russia group meeting few days ago describing (sp) HOW you were hacked, but the bad guy who did it – not related to Defcon Group community,” the message reads. “And actually your accounts were hacked BEFORE ibrute by @hackappcom was presented,” the message reads. “We are not related to this situation and our group’s members are good and smart guys and we are working for the light and love.”
While the hack is unlikely to become an international incident, the FBI issued a statement Monday suggesting that the agency was investigating the leaks. Recent incidents of theft of data from celebrities have resulted in stiff prison terms. Notably: in December, 2012, a Florida man who pleaded guilty to hacking into the e-mail accounts of celebrities, including actress Scarlett Johansen was sentenced to 10 years in prison.