The security firm TrustedSec said in a blog post on Tuesday that a recent hack of the healthcare network Community Health Services was the result of an attack on the so-called “Heartbleed” vulnerability in OpenSSL. According to TrustedSec, attackers targeted vulnerable VPN (virtual private network) software from Juniper networks in a breach that affected an estimated 4.5 million patients. TrustedSec cited a “trusted and anonymous source close to the CHS investigation” in its blog post. It said attackers were able to glean user credentials from memory on a CHS Juniper device by exploiting the Heartbleed vulnerability. Those credentials were used to login via the VPN to CHS’s network, then move laterally to the servers containing the patient data. [Read more Security Ledger coverage of the Heartbleed vulnerability here.] A separate report by Bloomberg attributed the attack to hackers in China, though it did not provide any evidence linking the attackers to a specific Chinese […]
Secunia
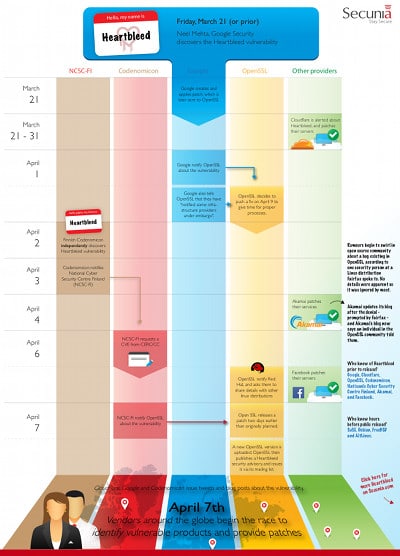
Infographic: A Heartbleed Disclosure Timeline (Secunia)
The dangerous security hole in OpenSSL known as “Heartbleed” has (mostly) faded from the headlines, but that doesn’t mean it isn’t still dangerous. As this blog has noted, the Heartbleed vulnerability was patched quickly on major platforms like Apache and nginx and by high profile service providers like Google and Facebook. But it still has a long tail of web applications that aren’t high risk (i.e. directly reachable via the Internet) and embedded devices that use OpenSSL or its various components. As the folks over at Acunetix note in a blog post today, hundreds of other services, application software and operating systems make use of OpenSSL for purposes that might be entirely unrelated to delivering pages over HTTPS. This includes all the email servers (using SMTP, POP and IMAP protocols), FTP servers, chat servers (XMPP protocol), virtual private networks (SSL VPNs), and network appliances that use OpenSSL or its components. The number of systems vulnerable to […]