In this Spotlight edition of the Security Ledger Podcast, sponsored by Trusted Computing Group*: we’re joined by Rob Spiger, a principal security strategist at Microsoft and co-chair of the cyber resilient technologies working group at Trusted Computing Group. Rob talks to us about efforts to make more resilient connected devices and how the advent of the Internet of Things is changing TCG’s approach to building cyber resilient systems.
resilience
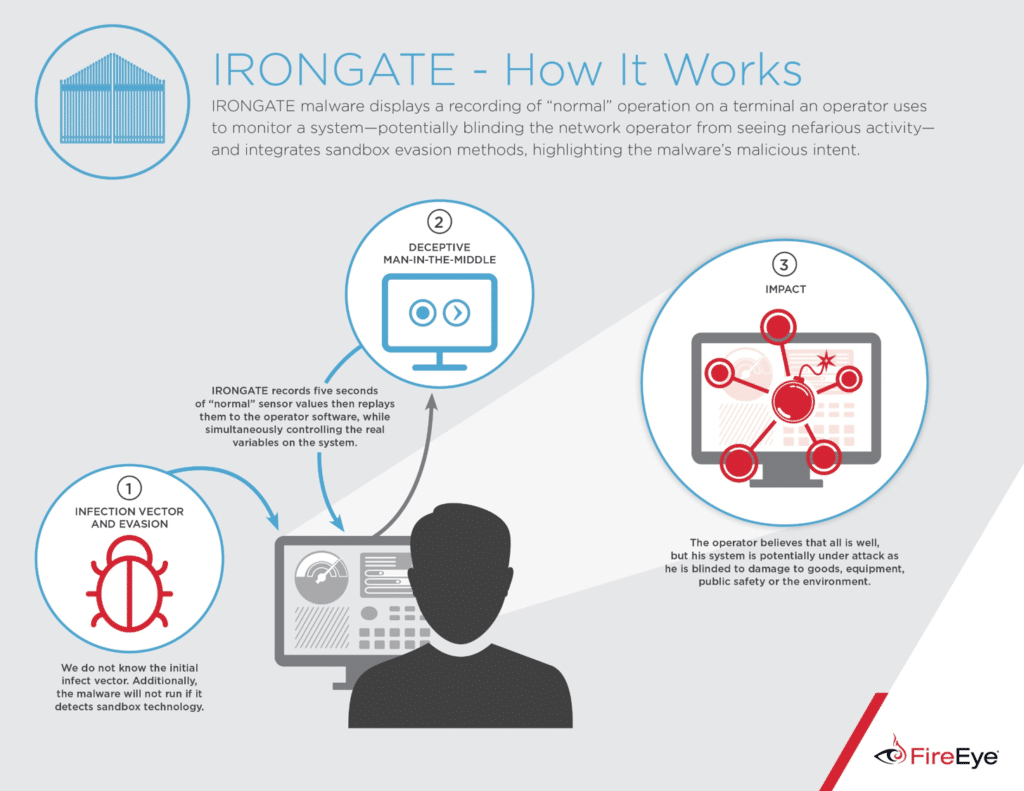
New Stuxnet-Like Industrial Control System Malware Ups The Ante
In-brief: Security firm FireEye is claiming to have discovered proof-of-concept malicious software that targets industrial control systems software that is used to operate critical infrastructure worldwide.
Cyber Insurance: Triumph of the Accountants?
In-brief: Rapid advancement in the market for cyber insurance is poised to transform a cyber security market based on FUD (fear, uncertainty and doubt) to one based on hard numbers and risk. Consider yourself warned!
To Secure Modern Networks: Close The Visibility Gap
In-brief: In a world where billions of devices, users and applications can come and go freely, how do you make sure that the threat protection defenses you have in place are working properly to protect your environment?
At Summit, in search of Leadership on Cyber Security
In-brief: President Obama will address technology leaders at a Summit at Stanford University on Friday. But technology industry leaders say that much hinges on Washington’s ability to pass needed legal reforms.