Firms looking to respond to increasingly sophisticated cyber attacks face immense hurdles. Among them: a dire shortage of skilled cybersecurity workers, as well as expensive and hard-to-operate investigative tools, according to a report released Tuesday by the cybersecurity firm Command Zero.
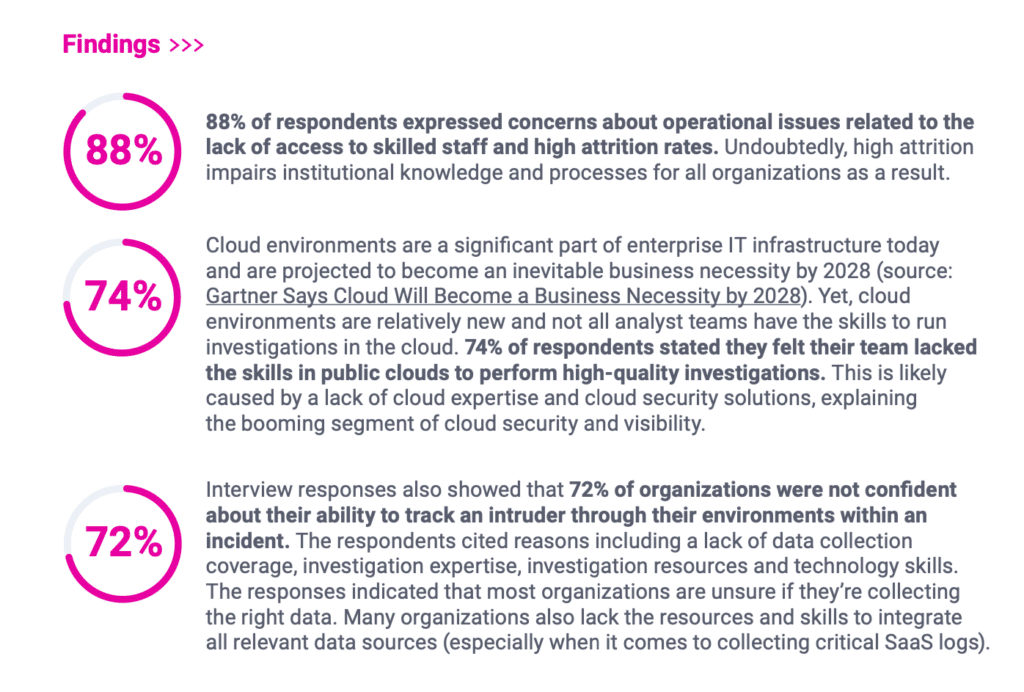
Almost 9 out of 10 security operations leaders (88%) asked by the cybersecurity firm Command Zero in a recent survey expressed concerns about their ability to carry out investigations into cyber incidents, citing a dire shortage of skilled staff as well as high attrition rates. The shortage is particularly acute when it comes to staff with expertise in managing the security of cloud platforms, the report said.
Adding to the challenges facing organizations, security operations (SecOps) tools used to conduct investigations such as SIEM, SOAR, and EDR were described as costly and hard to operate, and shared blind spots when it came to monitoring critical SaaS applications and integrating non-security data sources.
The survey was conducted by Command Zero, a cybersecurity startup that offers a cyber investigation platform that supports SOC tier-2 and tier-3 analysts, incident responders, and threat hunters. The report is based on insights gathered from interviews with 352 cybersecurity professionals working across 15 industries. Survey respondents include CISOs, security VIPs, directors, managers, incident handlers and respondents, risk leaders, and legal counselors, Command Zero said.
Recent years have brought changes and improvements to many areas of security operations, cyber investigations remain “ad-hoc processes” that lack “consistency and auditability,” said Dov Yoran, the CEO and co-founder of Command Zero.
“Clearly, we need to address increasing challenges with infrastructure complexity, the universal talent gap, higher regulatory and compliance requirements.
Worsening Conditions on the Ground
The cybersecurity situation for both private and public sector organizations is dire. Recent incidents affecting both cash-strapped municipalities and wealthy private sector firms underscore the sophistication of modern malicious campaigns and the challenges that organizations face in identifying, tracking down, and ejecting malicious actors from their environments. In the latest example, the payment processing firm Slim CD said this week that hackers breached its network in August 2023, making off with the sensitive financial and personal information of close to 1.7 million people. The breach was not detected until June 2024, almost a year after the initial compromise.
In its analysis of the work of Chinese APT Volt Typhoon, Microsoft earlier this year noted that the group was difficult to detect because of its use of “live off the land” techniques within compromised environments, and its ability to leverage compromised civilian infrastructure such as “end of life” broadband routers deployed in homes and small businesses.
Cyber Skill Gap a Major Challenge in Cyber Investigations
Cyber Security skill gaps have persisted for years. According to Statistica, in 2024, the share of organizations experiencing a shortfall of skilled IT security employees stood at 85.8%. This research indicates that this gap is even more acute for cyber investigations that demand advanced skill sets, like incident response (IR) and investigators.
Organizational investigations capable of detecting such breaches rely on organizations’ ability to keep and develop individual talent. However, the survey respondents revealed that many of them are unable to maintain security operations talent. Specifically, 74% of cybersecurity professionals who were surveyed felt their teams lacked the skills in public clouds to perform high-quality investigations. In addition, 72% of organizations admitted they were not confident about their ability to track an intruder through their environment.
How SecOps Tools Help, and Hinder Cyber Investigations
Cyber investigations are the biggest bottleneck for security operations, the survey found. Security operation teams rely upon technologies like EDR/XDR, SIEM, and SOAR. Among the people who participated, 85% regarded EDR as the most heavily relied upon tool, while 76% of them reported ingesting security-relevant data to an SIEM for investigations and GRC purposes.
But the cost and complexity of those tools often hamper investigations. Respondents cited concerns about the high costs of using SIEM, SOAR, and EDR. The report found that 75% of individuals polled said they needed more resources and skills to integrate data sources into SIEM and SOAR, including specialized resources to script and automate playbooks for SOAR platforms, for example.
Wanted: Standards for Cyber Investigations
Finally, respondents almost universally cited a lack of standard, agreed-upon processes, tools and procedures for conducting cyber investigations as a major obstacle. An overwhelming 92% of those questioned cited the lack of standardized collaboration tools as a key challenge during a cyber investigation. Relying on inadequate solutions results in inefficiencies, miscommunications, and data loss.
Couple that with the external pressure surrounding high profile incidents from the press, law enforcement agencies, or other regulators and the environment is rife for cyber investigators to make errors during their investigations. In fact, 80% of CISOs surveyed by Command Zero said they find tracking and complying with regulatory reporting immensely complex. In comparison, 79% of survey interviewees cited time-consuming reporting requirements and updating management as a significant challenge.
The Solution: Better Tools and Processes
There is no “silver bullet” to fix such complex problems. However, security operations leaders can take steps to improve the ability of their organization to respond to malicious campaigns and conduct effective cyber investigations. Among Command Zero’s recommendations are the adoption of a unified platform for conducting cyber investigations that gives security team members the ability to interrogate both legacy, on-premises and cloud platforms.
Cyber investigators also need to extend their investigations beyond the “usual suspects,” accessing and analyzing data from a much wider spectrum of both traditional and non-traditional IT systems. To accomplish that, organizations should embrace automation to enhance data collection from security and non-security tools and other data sources. Doing so will improve the overall efficiency and the gaps in capabilities of tools like EDR/XDR, SIEM, and SOAR.
Finally, security teams need to nurture and promote critical cybersecurity talent, and foster a culture of effective collaboration and communication for investigation. Doing so will minimize inefficiencies and keep the team focused on the incident.
“Using expert platforms, AI and automation will help overcome the challenges identified by the research,” said Yoran of Command Zero. “We hope the findings and recommendations in this report help guide improvements in security operations.”






