In this Expert Insight, Harshil Parikh, the co-founder of Tromzo, an application security management firm, reveals findings from the company’s recent State of Modern Application Security Report, which surveyed 400 application security pros about their experiences with cyber attacks, addressing software vulnerabilities and the closer integration of security and development teams.
At Tromzo, we spend much of our time thinking about the challenges security professionals face as they strive to keep modern apps secure. To identify and better understand the roadblocks encountered by AppSec teams, we commissioned a survey of over 400 of these professionals. We published the results of this survey in our first annual State of Modern Application Security Report.
In our survey, we asked questions about the challenges faced today, including the relationship between security and developers. We probed for information about what would make AppSec programs more effective.

Our goal with publishing the results of this report is to help CISOs and security leaders better understand what’s preventing their application security programs from scaling. We believe that, armed with this information, they can keep up with the fast pace of modern software development.
Here’s a quick summary of six of our top discoveries for those who haven’t had a chance to read the full report.
Security Incidents are the norm
If you ask nearly anyone who works in cybersecurity, they will concur, at least anecdotally, that it’s not a question of if your organization will be the target of a cyberattack, only a question of when it will happen.
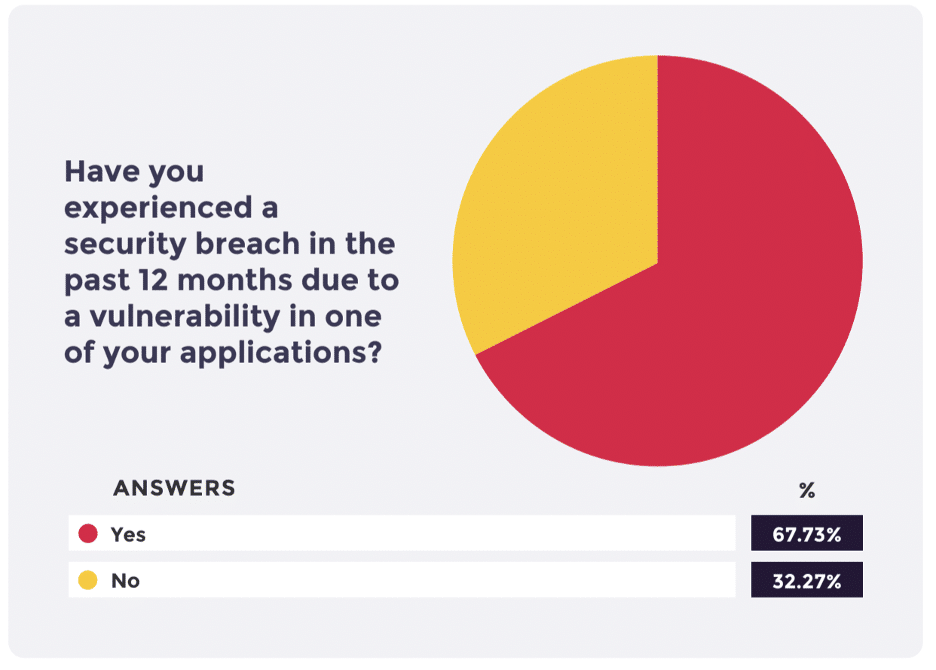
Even though over two-thirds of our respondents reported a security incident in the last year, it is widely understood that companies are hesitant to report attacks, making it challenging to measure the pace at which cyber incidents occur. By any measure, the rate at which bad cyber actors are attacking organizations is increasing.
The accelerating pace of cybersecurity incidents creates a stressful work environment for cyber defenders. Security teams and developers want to deliver fantastic secure software, but knowing they are increasingly vulnerable causes friction between the teams and delays delivering secure applications.
Lots of un-addressed vulnerabilities
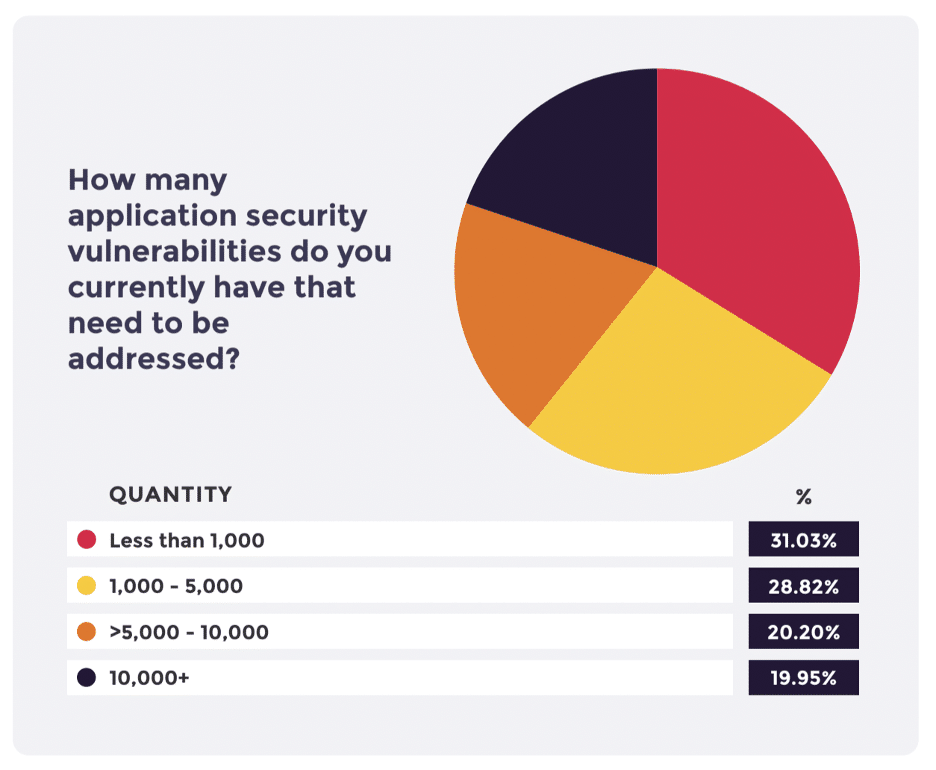
Five thousand unaddressed security vulnerabilities is a large number no matter how big the organization. Half of that 40% actually had more than ten thousand vulnerabilities they needed to respond to when they took our survey. If this were a static number, teams could chip away at it over time, but it’s not. The number of unresolved vulnerabilities continues to grow.
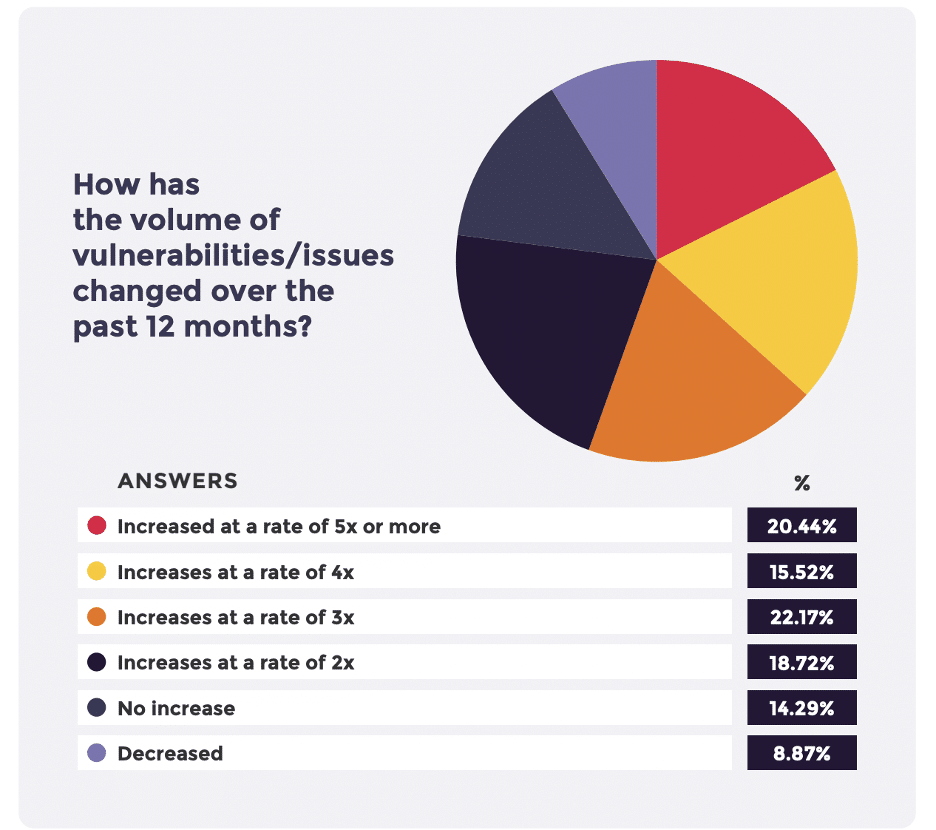
While the sheer number of vulnerabilities that security teams have not yet been able to address is alarming, the growth rate is even more concerning. Over 20% of our respondents reported that the volume of vulnerabilities has increased threefold in the last year.
Silos continue to hamper communication.
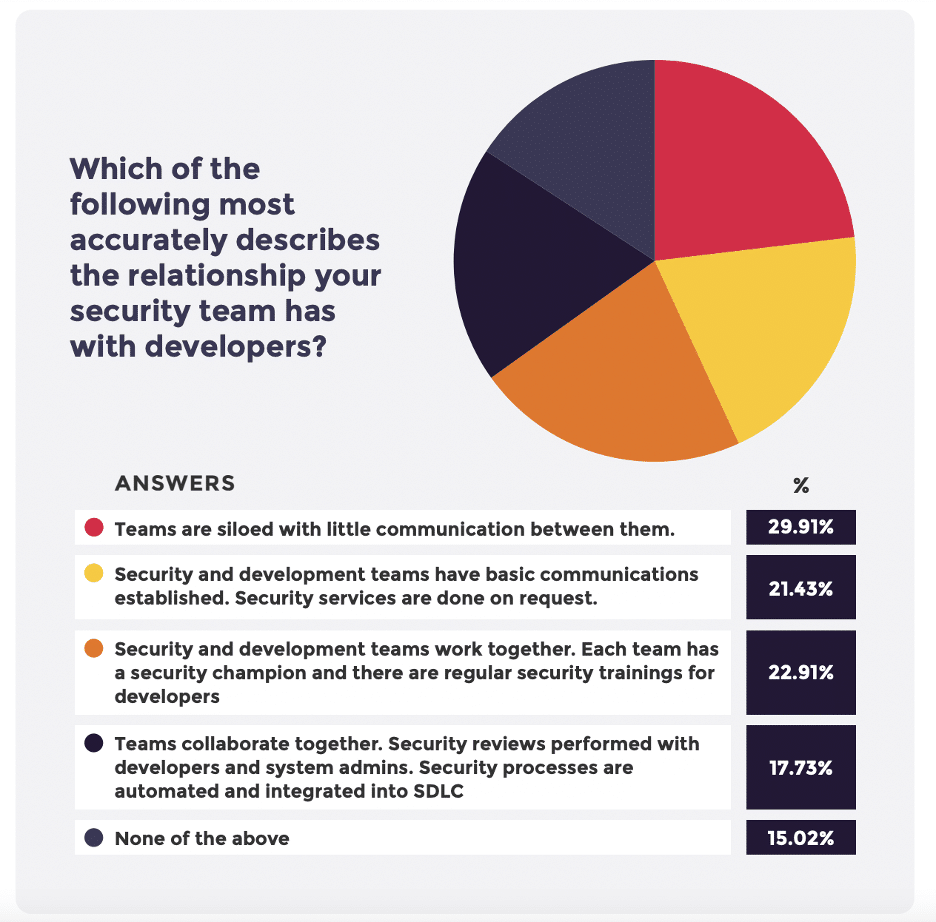
Our research shows that a lack of timely communication is among the top contributors to conflict between security practitioners and developers. When these two teams work in independent silos, communication breaks down, and they see each other as an obstacle to be overcome, not an ally to whom they can turn for solutions.
Because the success of an organization’s application security program depends on a high level of communication and collaboration between developers and security teams, leaders should focus on integrating these teams. Where friction exists, security concerns can go unchecked.
Stronger ties between security, development
The news is not all bad, thankfully. Over half of security teams feel that their relationship with developers in their organization is improving. Stronger relationships are more likely to be found as security and developer teams work closely with each other and build relationships of trust. If developers see the AppSec program as always coming “late to the party” and always with bad news, productive relationships are nearly impossible to cultivate.
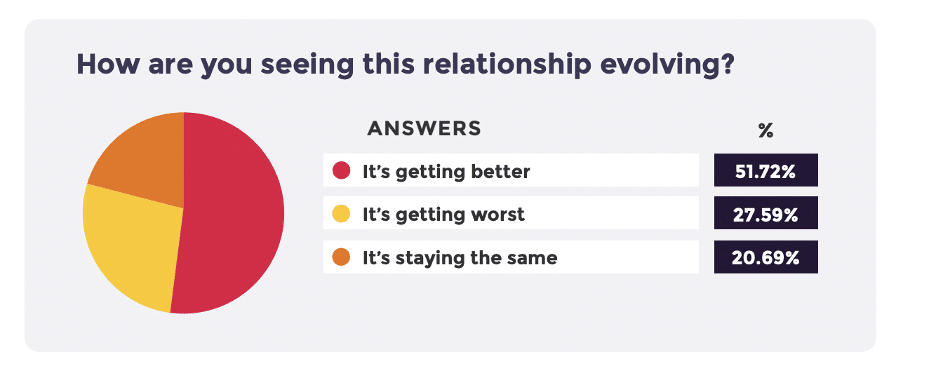
Wanted: tighter integration
Organizations with a more mature application security program employ an end-to-end approach that integrates AppSec functions throughout the software development life cycle. This strategy delivers superior results to the traditional method because it provides developers with feedback on their security earlier in the process (shifting security left). It allows them to leverage integration and automation throughout the software development process. Over 20% of our respondents saw this end-to-end approach as the most significant thing that leaders could do to improve the relationship between security and developers.
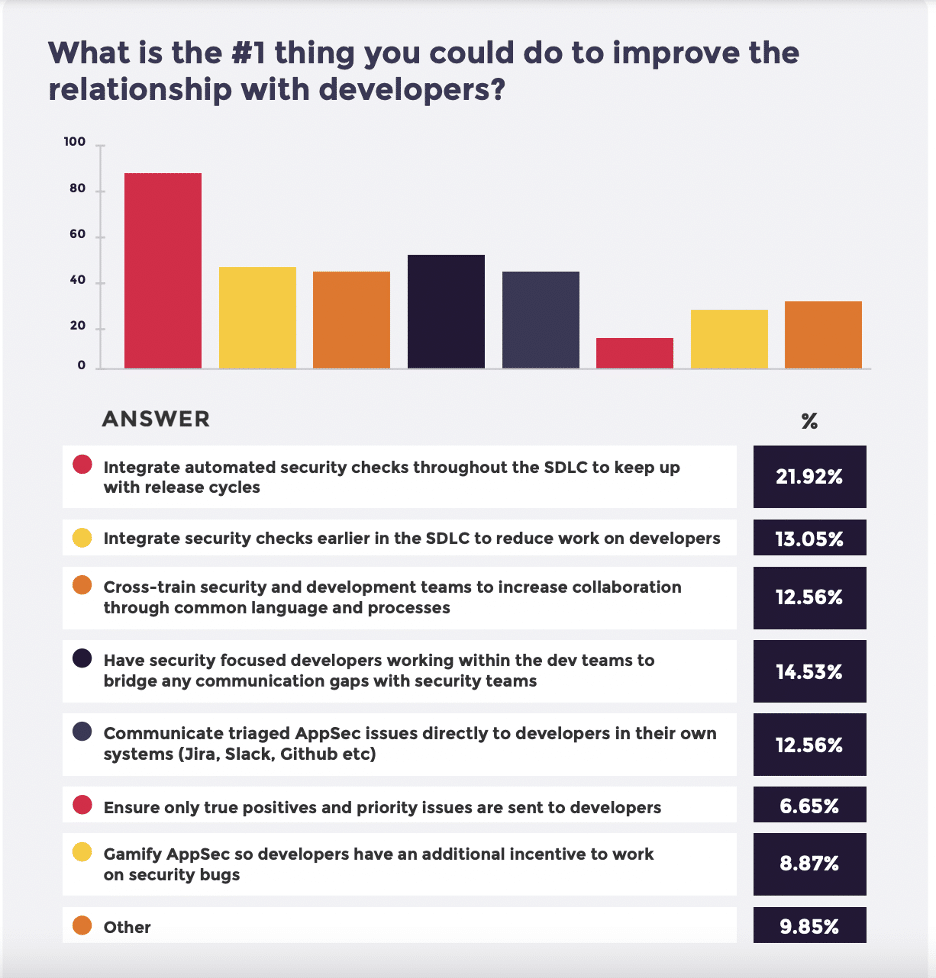
One could say that not having others do what they say is a challenge for everyone. But, in this case, what AppSec teams are asking developers to do is what is needed to keep their code secure and protect the organization from a potentially catastrophic attack. Security professionals are helpless to achieve their purpose if developers don’t implement the fixes they identify.
The key to resolving this challenge, like with any interpersonal conflict, is to have both parties involved in the decision-making. To avoid the perception that security is continually coming to them with a list of “asks,” developers should be involved in the process. If developers are held accountable for producing secure code, the AppSec team becomes a valuable resource for them.
Conclusion
Our State of Modern Application Security Report clearly indicates that one of the most effective measures organizations can take is to adopt a developer-first approach to security.
Developers need to own more security testing and remediation aspects while AppSec teams transform themselves to take a supporting role and provide security oversight. A developer-first paradigm enables security teams to apply their time and expertise toward solving complex security problems.
CISOs must eliminate the friction between developers and scale their security programs. Achieving security at scale requires a developer-first approach that ensures security processes are easy for developers so they can focus on writing great code. Only then can AppSec teams focus on higher-value strategic work.
Developer teams own tactical security tasks, and the AppSec team will continue to be the experts in making risk-based decisions and driving security accountability across the development teams.
Application security is evolving toward becoming incorporated into developer workflows. As organizations strive to create a security program that assists developers in building secure software, they allow businesses to make their digital transformation journey safer and faster.
(*) Disclosure: This article was sponsored by Tromzo. For more information on how Security Ledger works with its sponsors and sponsored content on Security Ledger, check out our About Security Ledger page on sponsorships and sponsor relations.

