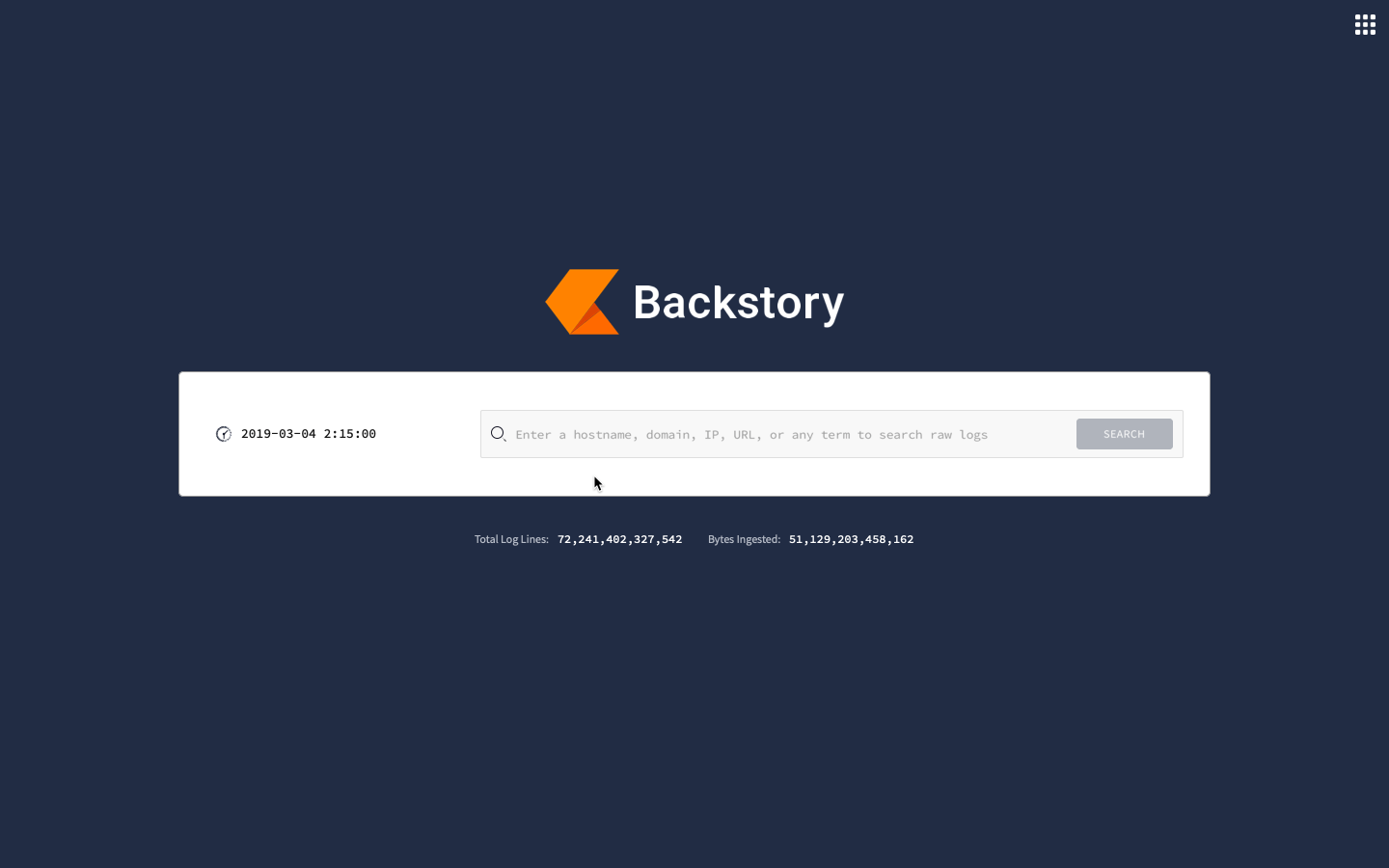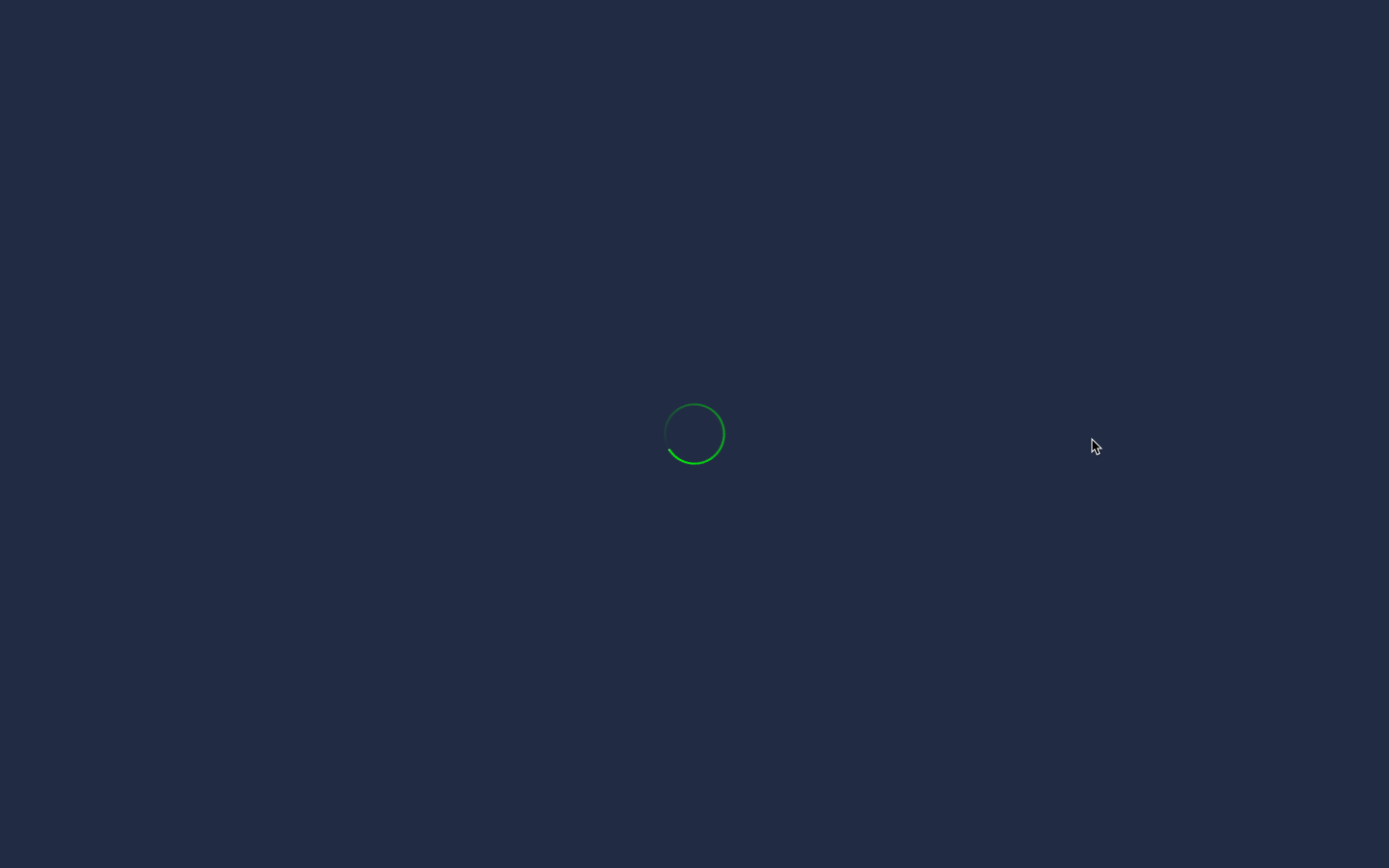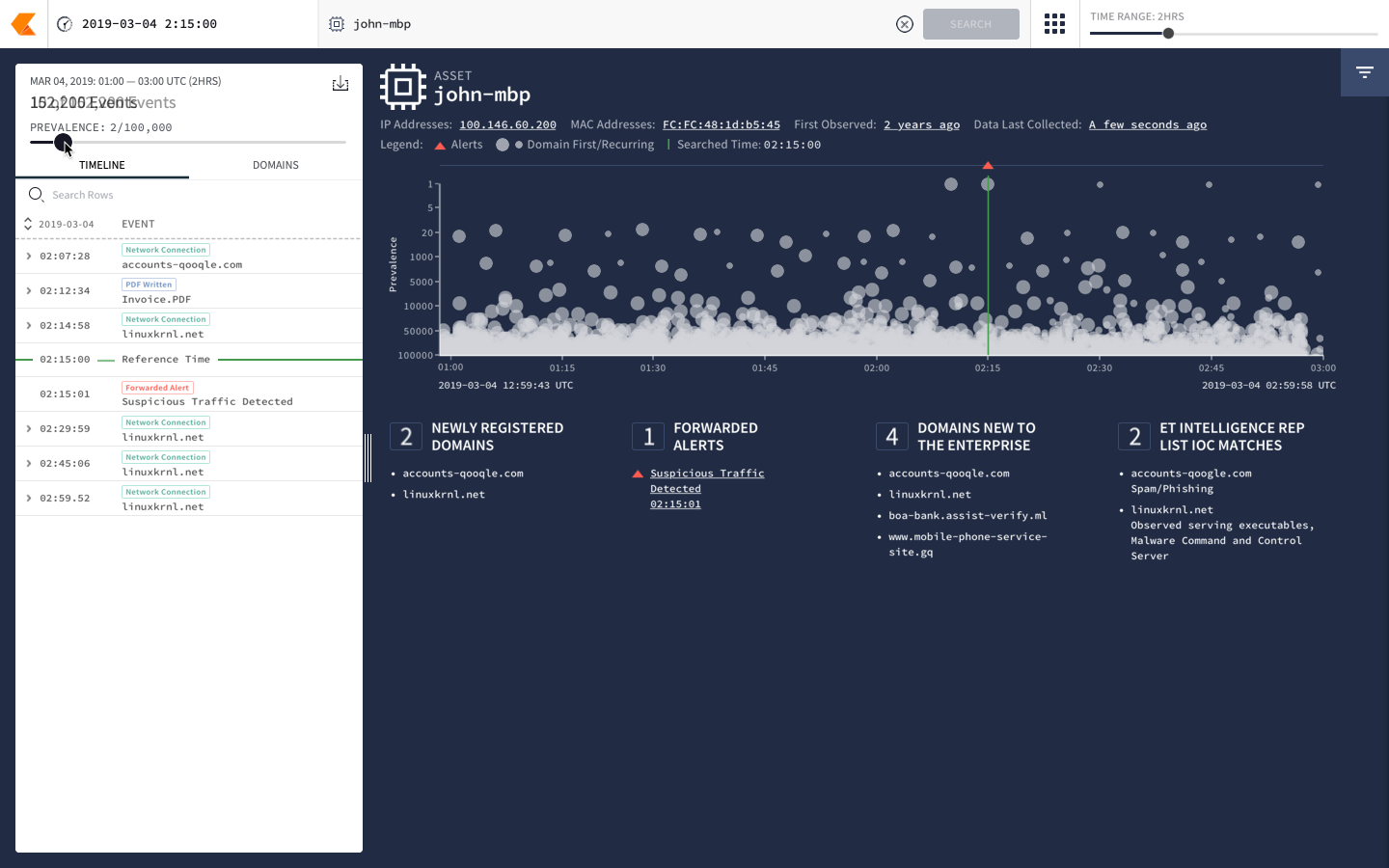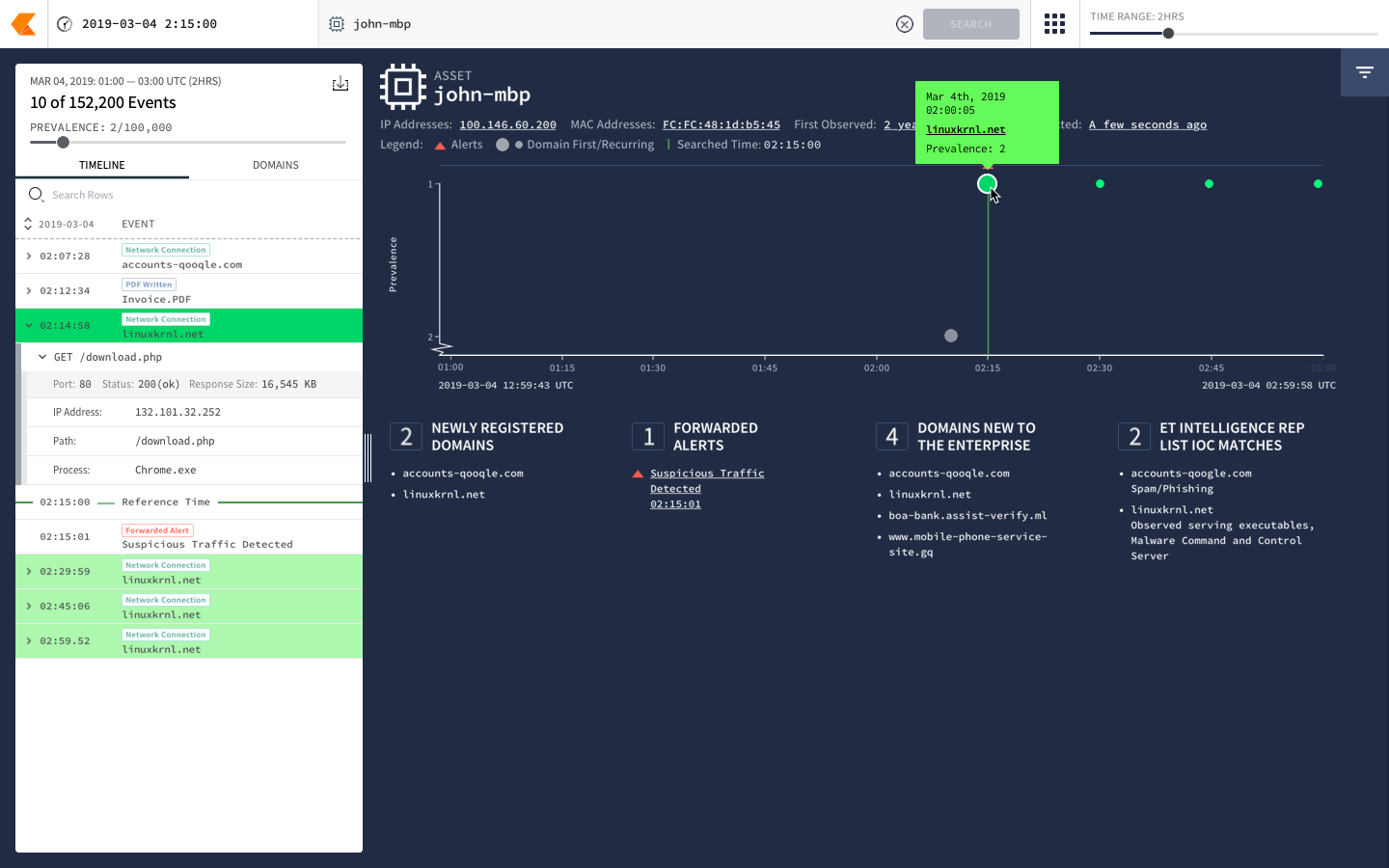
Alphabet spin-out Chronicle’s new security intelligence service, Backstory, appeals to companies drowning in operational data and desperate for security insights, according to the companies who are using the platform.
The announcement on Monday by Chronicle, an Alphabet company, that it was releasing Backstory, a security data analysis platform, was met with a grim kind of silence from most of its would-be competitors, who have gathered in San Francisco for the annual RSA Conference.
Backstory was the fulfillment of the first part of Chronicle’s mission, CEO Stephen Gillett told the audience in downtown San Francisco.
“It’s about how we use assets and infrastructure. Its about using the best artificial intelligence, machine learning and economic model to allow organizations to make sense of data,” he said.
The impact of the news was clear enough. Stock in Splunk, Backstory’s erstwhile rival and a leader in the SIEM space, dropped 12% on Monday from its high on Friday. Nir Polak, CEO of Exabeam, a security data intelligence and management firm said that Backstory simply does what his company has been doing for three years – from scale to pricing.

“It’s not enough to simply throw large amounts of storage and compute at the problem,” he said, touting Exabeam’s “sophisticated analytics” and work with major corporations in industries like banking, retail, insurance and technology.
But a conversation with one Backstory customer suggests that the threat to established security firms posed by Chronicle is real and – perhaps – a sign of larger, tectonic shifts taking place in the information security marketplace.
Elephants in the Room
First off is the inescapable fact of Backstory’s provenance. The Backstory product was born of Alphabet’s “X” moonshot project factory and the founders of Google’s own Threat Analysis Group (TAG) including Chronicle co-founder Mike Wiacek who built the TAG team.
Google’s name may not be on the product, but its talent and infrastructure stand behind it. Notably, this is just the latest evidence that major players in the cloud services space are taking an acute interest in selling into the security space, which has long been dominated by smaller, pure-play information security firms.
Microsoft, for example, said last week that it was announcing two new security services: Microsoft Azure Sentinel, a cloud based threat intelligence and analysis platform and Microsoft Threat Experts, a managed cyber threat hunting service.
The Backstory announcement sounds similar: making an appeal to companies desperate for tools to manage massive quantities of security data and for the trained professionals to help them do that.
The value proposition for companies like Google and Microsoft is threefold, then. First: as providers of cloud services that are the foundation of millions of businesses they have unprecedented visibility into Internet activity of all types – beneficent, malicious and everything in between.
Second, they have the development talent to create and deploy tools to analyze those massive volumes of data at scale and find the “needle in the haystack,” or as Eric Doerr of Microsoft Security Response suggested: the needle in the pile of needles.
Finally, these firms increasingly operate like massive stars (I don’t want to say black holes) whose size and gravity (OK…money) pull in talent and expertise that other firms just can’t afford – or afford to keep. Historically, that talent has worked mostly behind the scenes keeping firms like Google and Microsoft secure. Today, its becoming a resource that these firms are willing to share (or at least rent) to others.
But a conversation I had on the sidelines of RSA with Leo Simonovich, the VP & Global Head of Industrial Cyber and Digital Security at Siemens, helped me to see that there are actually bigger transformations that make offerings like Backstory and Sentinel especially timely.
We’ll always have Kiev
According to Simonovich, the roots of Backstory’s appeal to companies like Siemens can be found in places like Kiev, Ukraine, where cyber attacks on the Pivnichna remote power transmission facility in the capitol city knocked power out briefly in December, 2016. The attacks are believed to be thehttps://securityledger.com/2017/01/second-ukraine-power-outage-linked-to-russian-hackers/ work of hackers working on behalf of the Russian government.
The attacks combined elements of both traditional IT network attacks and hacks of specialized OT (or operational technology) assets according to analysis by Information Systems Security Partners (ISSP), a Ukraine firm. To the operators as the Pivnichna facility, however, the attack initially looked like a failure of their OT equipment, Simonovich said. Simply put: the utility did not have the ability to correlate activity on its traditional IT network with what was happening in its OT environment.
“Looking back, if you were to correlate control data with network data you could begin to see some weird things,” he said.
That’s where Siemens sees Chronicle’s Backstory – leveraging Google’s infrastructure – playing a role. “What company in the world is best positioned to apply AI and machine learning to ingest these different data streams, tag them, mix them, and begin to identify patterns,” he asked.
In a press conference organized by Chronicle on Monday, Simonovich said his company is monitoring emerging threats around industrial security. “Thirty percent of all attacks we see are targeting or originating in (operational technology),” he said. Most of those asset owners, however, are blind to what’s going on in that environment.
For executives like Simonovich, this is where Chronicle comes in. Siemens said it is just at the beginning of its collaboration with Chronicle: ingesting data and building use cases and prototypes using the system.
Chronicle isn’t the only company to offer these capabilities. Dave Weinstein of the firm Claroty, a startup that provides visibility and security for OT environments, said he didn’t see traditional IT tools as any obstacle to integrating OT data into security analysis. His company’s technology works well alongside SIEMS and other traditional IT security management tools by firms like CheckPoint, Cisco and others, Weinstein said.
OT? OK!
But Simonovich said that the Backstory “story” is really about its ability to process many different types of data at scale and then present it to customers in a lightweight fashion that is easy for them to consume – as easy as, say, Google. “They’re able to bring together different data streams – and not just network data, but data associated with geology, vibration monitors, line loss data,” he said. “There are only a couple of companies in the world that can do that.”
“Siemens view of world is that we need to come together with asset owners and companies like Google,” he said. “Our first challenge is how to integrate in a cohesive way.”
The other piece, Simonovich said, is the Chronicle’s business model. “The way our customers buy is not based on the amount of data that needs to be consumed,” he said. In fact, pricing models based on the volume of data – made common by vendors like Splunk – break in the OT context.
“If you look at a single turbine, it produces massive amounts of data on a per second basis,” Simonovich said. “So if your pricing model is based on an hourly or even a by-the-minute basis, that economic model is broken.”
Those comments were echoed by firms that are early users of Backstory. Chuck Markarrian of the commercial vehicle maker PACCAR said that IT pricing models based on the amount of data ingested by tools didn’t scale to meet the needs of industrial firm. “Margins count. Economics count,” he said. “The pricing model is broken in security. Its too expensive. I want to capture all this data, but I’m getting charged the more events I capture. (Backstory) breaks that mold.”
To lean on a cliché: the devil is in the details. While Chronicle has clearly demonstrated the potential power of its platform, its utility will depend on the analytic tools that are built on top of it, experts agree.
Also, there is skepticism about sharing so much proprietary data with a giant like Google. Chronicle CEO Stephen Gillett took pains to say that Chronicle was its own company and that customers would be able to strike data sharing and privacy agreements with Chronicle that met their needs. Google employees, he said, weren’t even able to “badge in” to Chronicle’s offices.
“We solve customer problems. They influence us more than any competitor,” Gillett said.