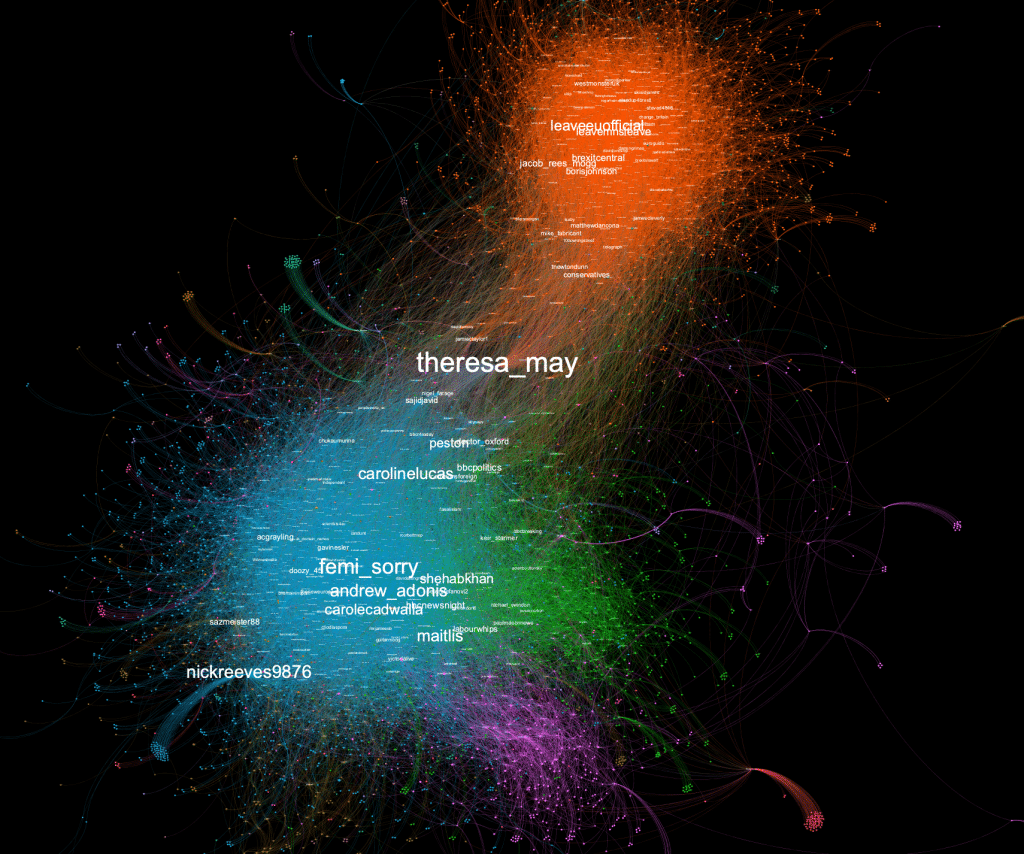
Suspicious activity on Twitter is trying to sway public opinion in favor of Brexit as the United Kingdom continues its struggle to reach a deal to withdraw from the European Union, according to a new report.
Tag: social engineering
Social Engineering Behind Syrian Hack Of NYT, Twitter?
How do you take some of the world’s largest online brands offline in a matter of minutes? If yesterday’s events are any guide, you do it by finding a gullible employee at vulnerable, downstream partner that those companies didn’t even know they had. That’s the lesson that appears to be emerging in the aftermath of yesterday’s chaotic tug of war between hackers who claim affiliation with The Syrian Electronic Army and some of the world’s leading online brands, including The New York Times, Twitter and Huffingtonpost.com. The attacks on Tuesday saw traffic to sites owned by those firms directed to web servers controlled by the attackers which displayed messages in support of the regime of embattled President Bashar al-Assad. According to a story in The New York Times, the attackers were able to compromise systems operated by Melbourne IT, an Australian domain registrar used by many prominent firms. With access to […]
Facebook Graph Search API Used To Brute Force Phone Numbers From Profiles
Facebook’s Graph Search feature hasn’t been released yet. But white hat hackers are already harnessing the powerful social search engine to gather sensitive information on Facebook users. A new module for Recon-ng an open source “web reconnaissance framework” allows anyone with a Facebook Developer account to use Graph Search and Recon-ng’s features to harvest phone numbers associated with Facebook user accounts. The tool, dubbed “Facebook Harvester” allows brute force searching by partial phone numbers, using brute-force techniques, according to a blog post by Rob Simon, a Canton, Ohio- based security professional. Simon, who counts penetration testing and reverse engineering among his skill set, wrote about his experiments using Graph Search on his blog, kc57.com. in April. In a phone interview with The Security Ledger, Simon said his work doing penetration testing drew him to the Graph Search API, which allows programmatic interaction with the Graph Search engine. He said the […]