In this interview with The Security Ledger, Amy Blackshaw of RSA talks about how the company’s RSA Netwitness SIEM product is evolving to keep pace with a fast -evolving security market. Job 1: use machine learning and automation to allow customers to make the best use of their human resources.
Tag: encryption
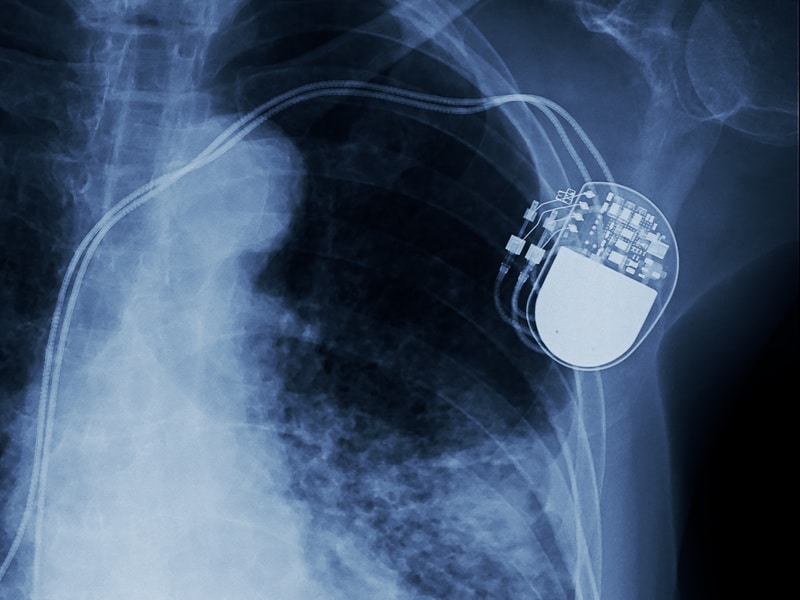
Spotlight Podcast: Synopsys’ Dan Lyon on the Challenge of Securing Connected Medical Devices
In this Spotlight Podcast, sponsored by Synopsys: In the wake of a presentation at Black Hat about security flaws in implantable pace maker devices, Synopsys Principal Consultant Dan Lyon joins us to talk about why medical device makers struggle to make their connected medical devices more secure. Dan and I discuss some of the flaws in the approach that medical device makers take to security, and how manufacturers can take a page out of their own book: applying the same standards to cyber security as they do to – say- device safety.
Spotlight Podcast: CSS on why Crypto Agility is the Key to Securing Internet of Things Identities
In this Spotlight Edition of the Security Ledger Podcast: identity is at the root of many of the security problems facing the Internet of Things, from vulnerable and “chatty” endpoints to a lack of robust update and lifecycle management features. To figure out how we might start to build a more secure IoT ecosystem, we invited Judah Aspler, the Vice President of IoT Strategy at Certified Security Solutions, or CSS Security in to talk about how more agile PKI infrastructure is one element in scaling the Internet of Things without creating a giant security mess.
Secure Access as a Business Accelerator: a Conversation with Pulse Secure
In this Security Ledger Conversations Video, we speak with Sudhakar Ramakrishna, the CEO of the firm Pulse Secure on that company’s journey from Juniper Networks’ remote access business unit to a thriving, independent company selling secure access technology to firms with on premises, cloud and mobile deployments. Technology has utterly transformed how companies operate and managed information , changing the conversation about ‘remote access’ to one about ‘secure access,’ he says. We’ll talk about how Pulse Secure has leveraged those changes to find market success.
Quantum Principles Eyed to Solve Current Limitations in Encryption, Data Protection
Quantum principles are set to transform the next generation of Internet security, with new quantum-based technologies on tap to improve encryption and data communication which researchers believe could solve some of the limitations with current technology.