The huge security breach at software maker Adobe is even bigger than first reported, with more than 150 million credentials stolen, including records on up to 38 million active customers, according to a report by Brian Krebs at the web site Krebsonsecurity.com. Krebs said in a story posted Tuesday that Adobe’s initial estimates that user names and passwords for around three million customers was well short of the actual number taken by hackers who breached the company’s network. Citing a file posted by the website Anonnews.org, Krebs said the actual number of affected Adobe accounts stolen is much larger: 150 million username and hashed password pairs including credentials for 38 million “active” accounts, according to Adobe spokesperson Heather Edell. Edell told Krebs that Adobe has just completed a campaign to contact active users whose user IDs and encrypted passwords were stolen (including this author). Those customers are being encouraged to change […]
Tag: database
Gartner: Traditional IT Security Dead By End of Decade?
The analyst firm Gartner Inc. prides itself on its ability to identify emerging technology trends and talking up what’s next before it has even happened. The firm’s Hype Cycle maps the familiar path from promising new technology to ‘hot technology buzz word du jour,’ and (maybe) on to useful, less buzzy technology that’s actually being used. More important: the Gartner Magic Quadrant rates technology companies (and their products) according to a set of criteria that includes how forward-looking (or “visionary”) the company is. Given the sway Gartner’s ratings have in companies’ willingness to invest in products, it’s a foregone conclusion that companies Gartner picks to ‘do well’ end up…umm…doing well. Gartner has an interest in finding the next big thing in every market – but also of preserving as much of the status quo as possible. (All those quadrants generate some serious cash!!) So I was interested to read about […]
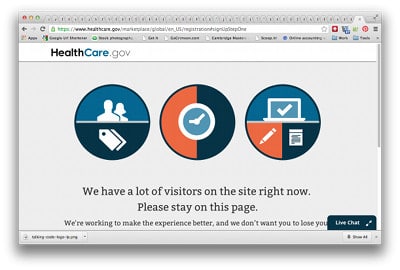
Health Exchanges Need A Fail Whale
In a blog post on Veracode’s blog today, I write about the problems encountered at government-run online health exchanges that were intended to connect millions to private insurance plans under the Affordable Care Act. The exchanges opened to the public on Tuesday, and they got off to a rocky start, with reports of web sites paralyzed as millions of uninsured Americans logged on to sign up for subsidized health insurance. In some cases, the problems appear to have been caused by “external factors.” New York State’s online health exchange was felled by the weight of more than 10 million requests of dubious origin, The New York Post reported. But other exchanges, including Healthcare.gov the federal government’s main health insurance storefront, which is used by residents or more than half of the states, were victims of their own success: overwhelmed when the doors swung open and millions of eager customers poured […]
More Questions For Facebook On Extent Of Ghost Profiles
The security firm that disclosed a security hole in a Facebook feature that allows users to download their own data file says the social network giant still has questions to answer about the extent of the data breach. Writing on their blog, researchers at Packet Storm Security said that Facebook has underestimated the extent of the breach, which affected around six million users of the social networking site and an unknown number of non-Facebook users. Packet Storm says that Facebook’s analysis of the breach failed to account for ways in which it could be exploited, in an iterative fashion, to glean information on Facebook users beyond the individual pieces of data that may have been viewed by users who used the Download Your Information (DYI) feature. The firm also called Facebook to task for failing to notify non-users whose information was exposed in the incident. On Monday, Security Ledger wrote […]
Podcast: The Big Truth – Responding To Sophisticated Attacks
If you work at a rank and file corporation in the U.S. or Europe, stories like those about the breach at the defense contractor Qinetiq are terrifying. Here’s a company that’s on the bleeding edge of technology, making autonomous vehicles and other high-tech gadgetry for the U.S. Military. Despite that, it finds itself the hapless victim of a devastating cyber breach that lasts – by all accounts – for months, or years. In the end, the attackers (likely linked to China’s People’s Liberation Army) make off with the company’s intellectual property (likely all of it) and, soon, defense contractors in Mainland China start turning out devices that look eerily similar to the ones Qinetiq makes. Ouch! If a company like Qinetiq can’t stop an attack by advanced persistent threats (APT) – or whatever name you want to use – what hope do overworked IT admins at rank and file enterprises […]