In this Security Ledger Conversations Video, we speak with Sudhakar Ramakrishna, the CEO of the firm Pulse Secure on that company’s journey from Juniper Networks’ remote access business unit to a thriving, independent company selling secure access technology to firms with on premises, cloud and mobile deployments. Technology has utterly transformed how companies operate and managed information , changing the conversation about ‘remote access’ to one about ‘secure access,’ he says. We’ll talk about how Pulse Secure has leveraged those changes to find market success.
Video
RSA Labs: cloud, microservices, mobility shift terrain for security providers
In this exclusive interview from April, the head of RSA Labs* says that keeping up with bad guys is only half the job. Security firms also need to work hard to stay relevant as trends like cloud adoption, containerization, microservices and mobility shift the ground under information security providers.
RSAs CTO is Bullish on Security. Blockchain? Not so much.
The success of blockchain technology in securing cryptocurrencies doesn’t make the technology a good fit for securing the Internet of Things, RSA Security Chief Technology Officer Zulfikar Ramzan says. Check out our exclusive conversation with Zully about IoT, blockchain and the state of the information security industry.
Where to find Security Ledger at The RSA Conference
The RSA Conference kicks off in San Francisco on Monday. Security Ledger will be there checking out the conference and meeting and talking with some of the top minds in the information security industry. Check out our schedule of appearances for the week.
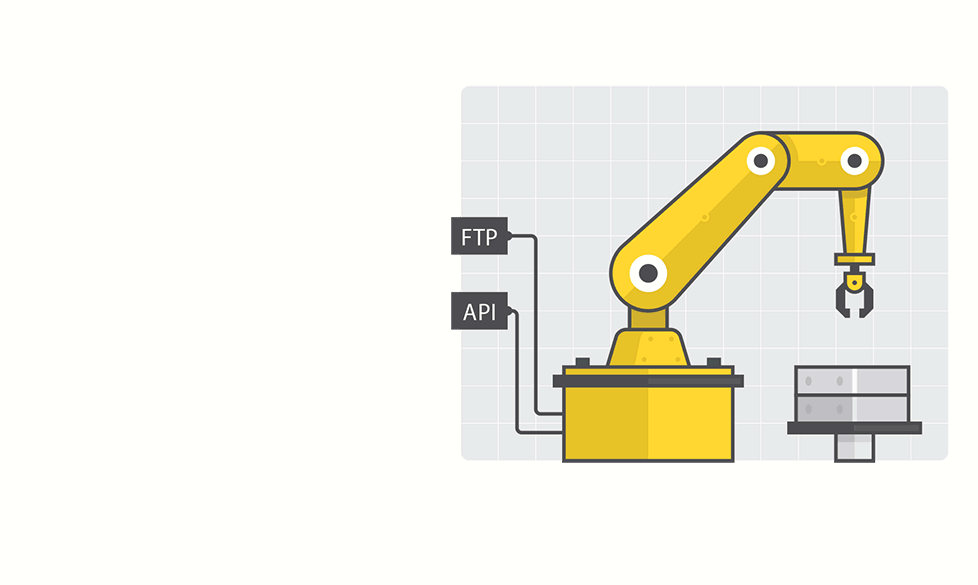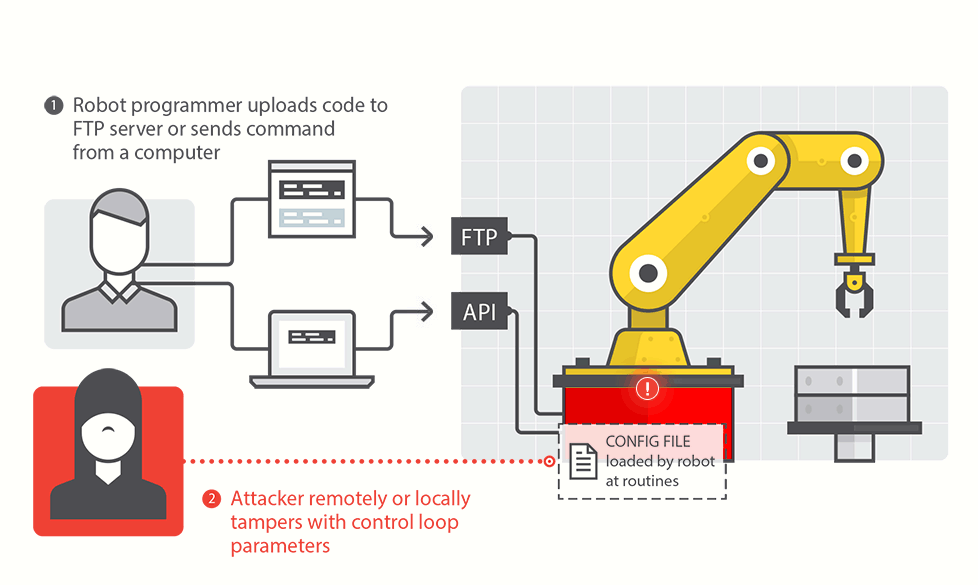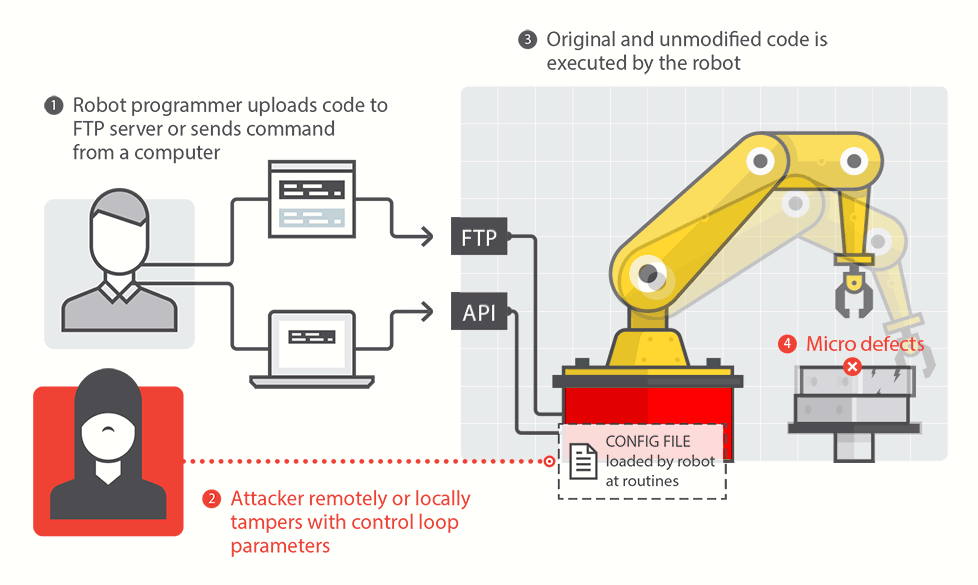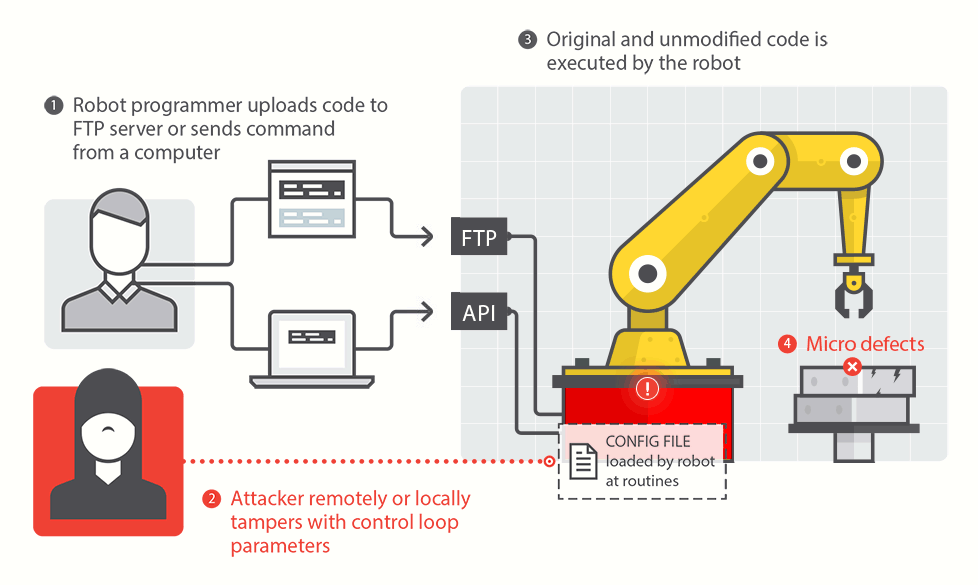
Report warns of Robot Hacks, Tampering
In-brief: Common industrial robots are susceptible to hacks and other forms of electronic hacking that could cause physical harm to workers or result in flawed and dangerous products.