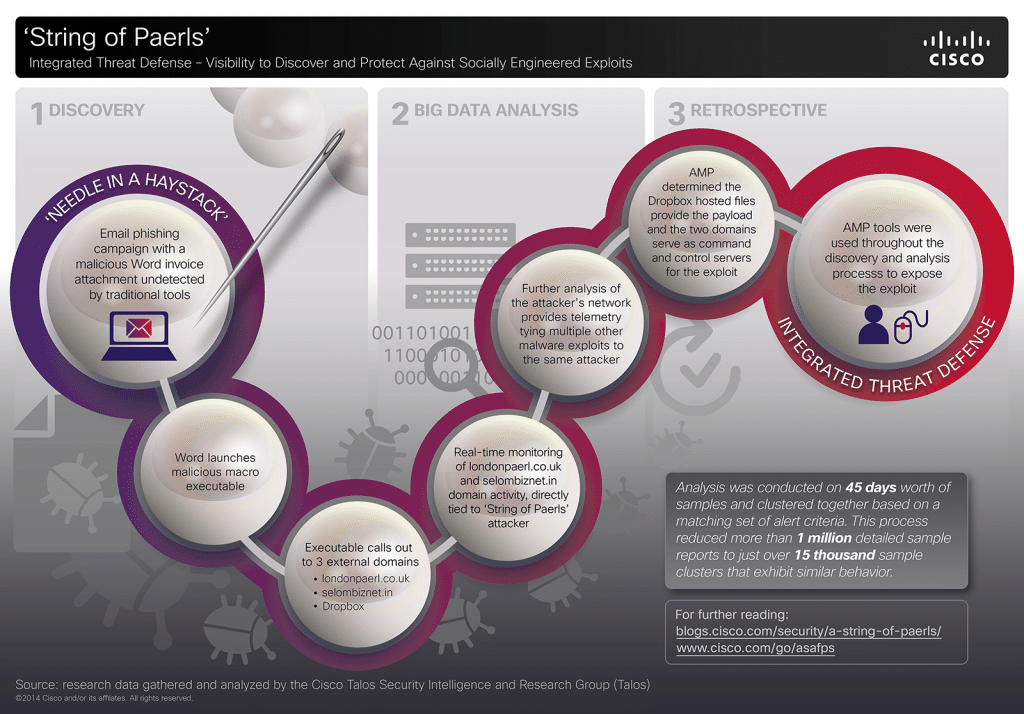
In the last year, the world’s attention has been riveted by a series of high-profile hacks of major corporations in retail, finance and the entertainment industry, among others. Each of these incidents is unique, involving different threat actors and motives. However, each of these attacks is also a sterling example of what we, at Cisco, term “multi-vector attack” that employs a range of technologies, deployed in numerous stages, to penetrate the defenses of the target organization. Here at Cisco, we have studied these attacks in-depth and have identified some commonalities among these multi-vector attack, and useful approaches to combat them. This blog post will discuss some of our findings. About Multi-Vector Attacks Any cyber attack, large or small is born from a weak link in the security chain. These weak links take many forms: poorly configured Web servers, gullible employees or vulnerable-but-common applications like Microsoft Office, Adobe Reader and Java are common examples. Multi-vector attacks […]
correlation
Wanna-Breach: Counterfeit Data Breaches Are A Thing
Headline grabbing data breaches are such a fixture of our modern business environment that they’ve even spawned a knock-off market: phony data breaches designed to harm a company’s image by making it look as if the firm has lost control of critical data. That’s the conclusion of a research note from Deloitte, which warns that malicious actors are increasingly using false claims about massive data breaches to bedevil established firms – inflicting real economic and reputation damage.
Essentials for Visibility-Driven Security
Visibility is surprisingly tricky. The security industry offers many disparate tools to provide customers “visibility” into what is happening on their networks. Among them are tools that track what applications are on the network, tools for enumerating and tracking software vulnerabilities, tools for determining when sensitive data has left a network, tools that indicate when attacks are underway and tools that identify and analyze network data flows – to name just a few. Of course, layered on top of all this “visibility” are further systems that correlate and analyze what the mission-specific tools are seeing. Promises of a “single pane of glass” aside, the result is often a mishmash of data and events that require skilled security practitioners to analyze and interpret. The mishmash, in turn, leads to errors in analysis and prioritization. Albert Einstein famously said “Any fool can know. The point is to understand.” So it is in the information security industry, where a common refrain is “you can’t protect […]
Infographic: Possible Attacks on The Internet of Things
The folks over at Trend Micro have put together a nice infographic that reminds us that all those smart devices connected to the Internet communicate through some well worn channels, namely: standard communications protocols like Wi-Fi, Ethernet and Bluetooth that connect devices to each other and the global Internet, as well as HTTP that are used to transmit data to and from cloud based resources like management interfaces. Of course those standard protocols also leave IoT devices vulnerable to a wide range of commodity attacks: from brute force password cracking on web based management consoles to Man in the Middle attacks that can sniff out authentication credentials and hijack sessions. Trend’s infographic does a good job of depicting the various layers in the IoT stack and some of the likely attack vectors for each layer. It also gives advice on how to protect yourself (use encryption, patch software vulnerabilities, disable unused ports). Nothing ground breaking […]
With $42m Invested, vArmour uncloaks with Software Defined Security
In the old days, startups would pull together funding from a small group of early “angel” investors and rush to get a product – any product- to market as soon as possible. The idea was to prove viability in the hopes of attracting larger investments that would let you actually develop the product you really want to sell. But that doesn’t work well for companies that want to solve really hard problem. Such projects, justifiably, need a longer runway that isn’t suited to vaporware or rapid product iteration. vArmour Networks, a Mountain View-based startup that emerged from “stealth” mode yesterday, is a good example of that latter kind of start-up. The company has already raised $42 million in three rounds, dating back to January, 2013. It is offering technology to tackle a vexing product: how to secure the information flowing within and between the growing ranks of virtual data centers. With […]