The Department of Homeland Security is warning U.S. firms that drones made in China may be spying on them and sending sensitive data to the Chinese government.
UAV
Do Drones Need Digital License Plates?
In-brief: there are more drones registered in the U.S. than aircraft, but there’s no easy way to track the unmanned aerial vehicles using the public airspace. In this podcast we speak with DigiCert CTO Dan Timpson about his firm’s partnership with AirMap to provide strong digital identities for drones.
Pew: IoT Will Take Off By 2025, Despite Security Woes
A survey of technology experts by the Pew Research Center and Elon University predicts that the Internet of Things will take off in the next decade despite serious concerns about the security of IoT devices and the data they hold. The IoT will gain wide adoption in the next decade, with the result that many aspects of day-to-day life will be transformed by a combination of inexpensive sensors, cloud based computing and data analytics. The report cites a number of likely innovations that will become commonplace by 2025 – from “smart” food products that can report when they are exhausted or spoiled, to smart roads and infrastructure to “subcutaneous sensors or chips that provide patients’ real-time vital signs to self-trackers and medical providers.” The Pew Center canvassed more than 1600 technology leaders and analysts about the Internet of Things and published the findings of the survey on Wednesday. The survey population included […]
Traffic Monitoring Tech Vulnerable To Hacking
Connected cars aren’t the only transportation innovation that’s coming down the pike (pun intended). As we’ve noted before: smart roads and smart infrastructure promise even more transformative changes than – say – having Siri read your text messages to you through your stereo system. The applications of smart road and connected infrastructure are almost limitless. But at this early stage (mostly proof of concept), much of the light and heat around smart roads is around applications of remote sensors at the roadside, or embedded in the road surface to identify problems like icy roads, the presence of liquids, traffic density, vehicle and pedestrian detection and more. For a nice overview of some sensor applications, check out this video from Liebelium. But that doesn’t mean that attacks against smart infrastructure are problems for the future. The security researcher Cesar Cerrudo points out in a blog post over at IOActive.com that many […]
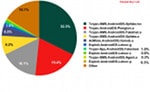
New Malware Exploits Android Glitch To Block Removal
A new malicious program that runs on Android mobile devices exploits vulnerabilities in Google’s mobile operating system to extend the application’s permissions on the infected device, and to block attempts to remove the malicious application. Writing on securelist.com, Kaspersky Lab’s research blog, malware researcher Roman Unuchek called the newly discovered Trojan the “most sophisticated” malicious program yet detected that works with Android phones. He cited the Trojan’s advanced features, including complex obfuscation techniques that complicated analysis of the code, and the use of a previously unknown vulnerability in Android that allowed it to take control of and maintain a foothold on infected Android devices. Kaspersky said it has contacted Google regarding the malware and the alleged vulnerabilities in Android. Google was unable to confirm that prior to publication. The malware, dubbed Backdoor.AndroidOS.Obad.a, is described as a “multi function Trojan.” Like most profit-oriented mobile malware, Obad is primarily an SMS Trojan, […]