President and Chairman of Trusted Computing Group (TCG), Dr. Joerg Borchert, shares the news regarding TCG’s first ever CodeGen Developer Challenge.
Trusted Computing Group
Episode 224: Engineering Trust In The Cyber Executive Order
In this spotlight edition of the podcast, sponsored by Trusted Computing Group* Thomas Hardjono and Henk Birkholz join us to talk about President Biden’s Cyber Executive Order and how the EO’s call for increasing trust in federal IT systems is creating demand for TCG technologies
Episode 220: Unpacking The Kaseya Attack And Securing Device Identities on the IoT
In this episode of the podcast, sponsored by Trusted Computing Group we dig deep on this week’s ransomware attack on the Kaseya IT management software with Adam Meyers of CrowdStrike and Frank Breedijk of the Dutch Institute of Vulnerability Disclosure. Also: Tom Laffey, a product security strategist at Aruba, a Hewlett Packard Enterprise firm, and co-chair of the Network Equipment working group at TCG about how that group is adapting its technology to make it easier for new generations of connected devices to attest to their integrity.
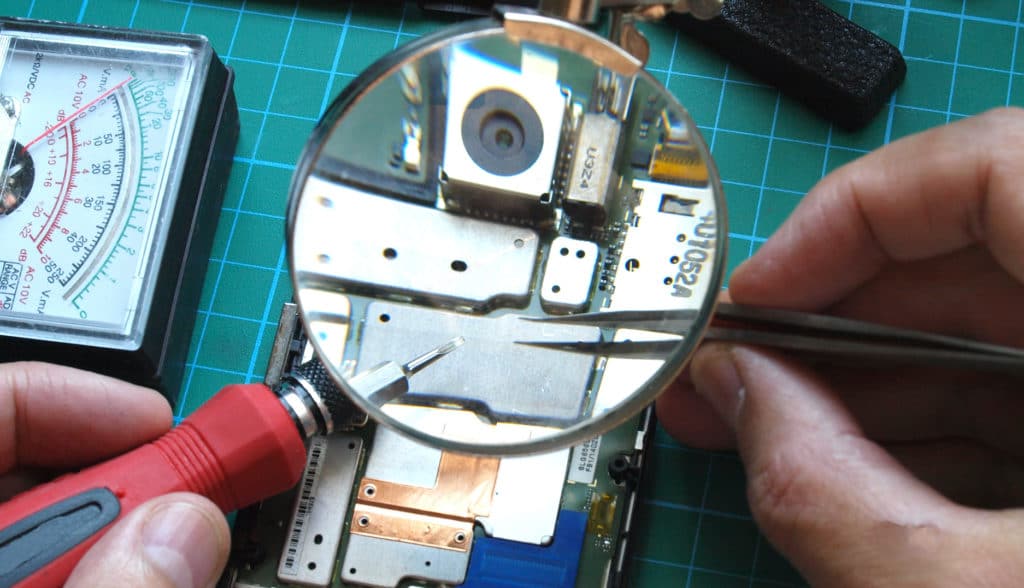
Episode 208: Getting Serious about Hardware Supply Chains with Goldman Sachs’ Michael Mattioli
In this week’s Security Ledger Podcast, sponsored by Trusted Computing Group, we’re talking about securing the hardware supply chain. We’re joined by Michael Mattioli, a Vice President at Goldman Sachs who heads up that organization’s hardware supply chain security program.
Spotlight Podcast: Intel’s Matt Areno – Supply Chain is the New Security Battlefield
In this Spotlight Podcast, sponsored by The Trusted Computing Group, we speak with Matthew Areno, a Principal Engineer in the Intel Product Assurance and Security (IPAS) group about the fast-changing landscape of cyber threats including attacks on hardware and software supply chains.