In-brief: Open redirects and forwards may be at the bottom of OWASP’s Top 10 list of web application security vulnerabilities, but they are still a potent and widespread problem, says Akamai’s Or Katz, who offers some suggestions for fixing it.
OWASP
Survey Finds Government Application Security Wanting
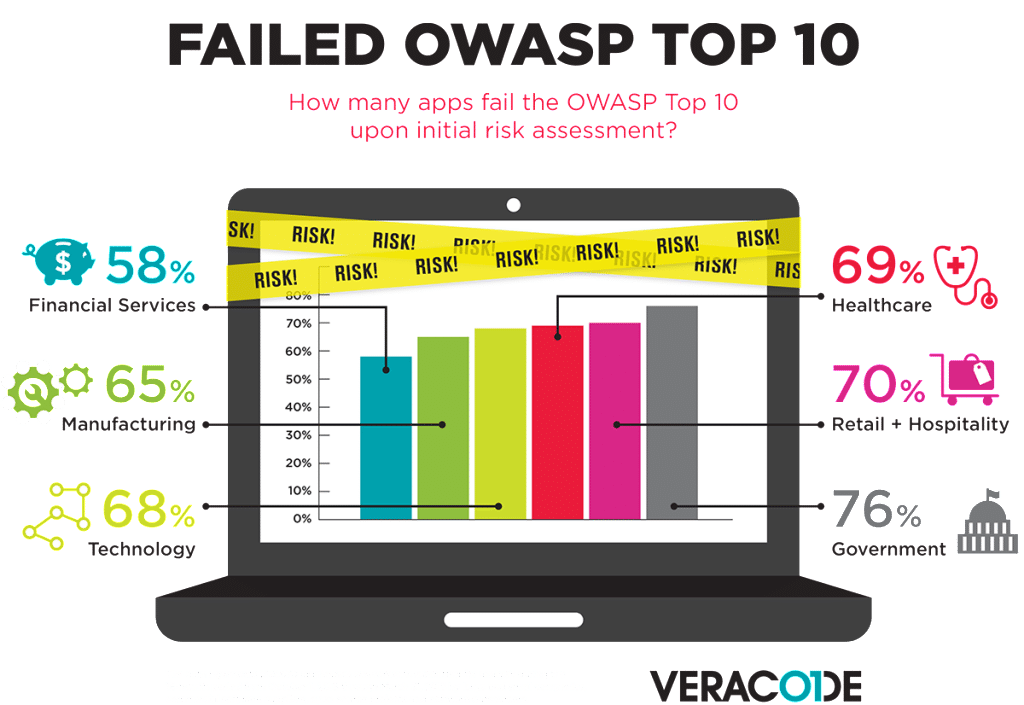
In-brief: A survey of web and mobile applications by the firm Veracode finds that governments are the most likely to use insecure software, as measured against the OWASP (Open of Web Application Security Project) Top 10.
Cyber Security and IoT: Fundamentals Matter
I really struggled to come up with a clever analogy to start this post. In doing so I realized that this exercise was itself, the exact problem I was trying to describe. So much conversation about cyber security, especially cyber security for the Internet of Things (IoT), focuses on the sexy, the complicated, the one-in-a-million. In doing so, we ignore the most common threats and basic attacks. I would like to argue that if we are to effectively defend ourselves in this new IoT world, we cannot ignore the fundamentals of security. But let’s be honest: the basics are boring. I know that. Many of the practices that are most important are also the ones we’ve heard about before. As we look at them: there isn’t anything new there. That’s true – but I take that as proof that they are sound practices, worthy of keeping top-of-mind, rather than old knowledge that can be discarded. Here’s […]