Hackers have put up for sale on the dark web sensitive military documents, some associated with the U.S. military’s MQ-9 Reaper drone aircraft, one of its most lethal and technologically advanced drones, security research firm Recorded Future recently discovered.
The firms’ Insikt Group on June 1 observed a bad actor trying to sell what are believed to be highly sensitive U.S. Air Force documents pertaining to the General Atomics unmanned aerial vehicle (UAV) while researchers were monitoring criminal activities on the dark web, according to a blog post published Tuesday.
“The data was offered for sale for $150-$200 and the seller was expecting payment in Bitcoin only,” Andrei Barysevich, director of advanced collection at Recorded Future and the post’s author, told us.
While it’s not uncommon to uncover sensitive data like personally identifiable information, login credentials, financial information and medical records being offered for sale on the dark web, he said it’s “incredibly rare for criminal hackers to steal and then attempt to sell military documents on an open market.”
See also: Cisco Talos: VPNFilter malware capable of stealing data, infecting IoT endpoints
Insikt communicated with the hacker and confirmed the legitimacy of his claim and the validity of the documents, which were obtained by exploiting a previously disclosed FTP vulnerability in Netgear routers to gain access to a computer in Nevada, according to the bad actor.

That computer happened to belong to a captain at 432d Aircraft Maintenance Squadron Reaper AMU OIC and stationed at the Creech Air Force Base. Insikt Group identified the name and country of residence of an actor associated with a group it believes to be responsible and is currently working with law-enforcement authorities. The documents are no longer up for sale, Barysevich told us.
“The seller was blocked from the captain’s computer after Recorded Future reported the issue to the relevant authorities, although we cannot confirm that the documents were not copied or downloaded in the period that the individual had access,” he said.
Data on drones and beyond
Through its contact with the bad actor, the Insikt team determined that he used Shodan’s popular search engine “to scan large segments of the Internet for high-profile misconfigured routers that use a standard port 21 to hijack all valuable documents from compromised machines,” according to the post.
Listen to: Podcast Episode 87: Vulnerability Reports Down the Memory Hole in China and the Groups Hacking ICS
The hacker stole a cache of sensitive documents, including Reaper maintenance course books and a list of airmen assigned to Reaper AMU, from the captain’s computer. The captain had recently completed the Cyber Awareness Challenge and, basically, should have known better than to allow his computer to be vulnerable the way it was, researchers noted. Specifically, he failed to set an FTP password for the router, allowing unauthorized access.
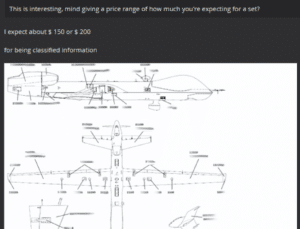
The course books themselves are not classified materials on their own; however, in the wrong hands, they could provide an adversary with information to assess technical capabilities and weaknesses in one of the military’s most technically sophisticated and deadly aircraft, Barysevich said.
The MQ-9 Reaper–with a name that describes it aptly–has been in use since 2001. When it went into service, it represented a shift in military drone use from surveillance, intelligence and reconnaissance to “a true hunter-killer role,” former Chief of Staff of the United States Air Force General T. Michael Moseley said in 2006. The U.S. Air Force, the U.S. Navy, the CIA, U.S. Customs and Border Protection, NASA and the militaries of several other countries are currently use the Reaper in various capacities.

The firm gleaned, however, judging from their content–a dozen various training manuals describing improvised explosive device-defeat tactics, an M1 ABRAMS tank operation manual, a crewman training and survival manual, and tank platoon tactics–that they must have been pilfered from the Pentagon or from a U.S. Army official. Again, while the documents don’t represent classified materials, they aren’t exactly something the military would want floating around for sale online, either, as most are distributed to U.S. government agencies and their contractors only.
2-year-old flaw exploited with success
The flaw the actors exploited to obtain the documents first appeared in 2016, when several security researchers revealed that Netgear routers with remote data-access capabilities were susceptible to malicious attacks if users didn’t update the default FTP authentication credentials.
Even today, despite knowledge of the flaw, the problem persists. Recorded Future identified more than 4,000 routers susceptible to the attack in recent research, Barysevich said. He describes Netgear’s steps for protecting devices in his blog post.
Military response teams are currently working to determine the exact ramifications of both data breaches. Nevertheless, the fact that a single hacker with moderate technical skills was able to identify several vulnerable military targets and exfiltrate highly sensitive information in a week’s time is worrying, given what a more determined and organized group with superior technical and financial resources could achieve, Barysevich said.
He said to mitigate such a breach from happening in the future, the necessary should first evaluate whether a personal or work computer was affected, and go on to take further steps from there.
“If a captain indeed was using his personal computer, an investigation of a potential violation of established protocols for handling sensitive documents might be granted,” Barysevich said.






