In-brief: A new report from the firm Websense finds that financial services firms are being hit hard by cyber attacks, including targeted attacks aimed at luring employees into installing malicious software on corporate networks.
Tag: Web
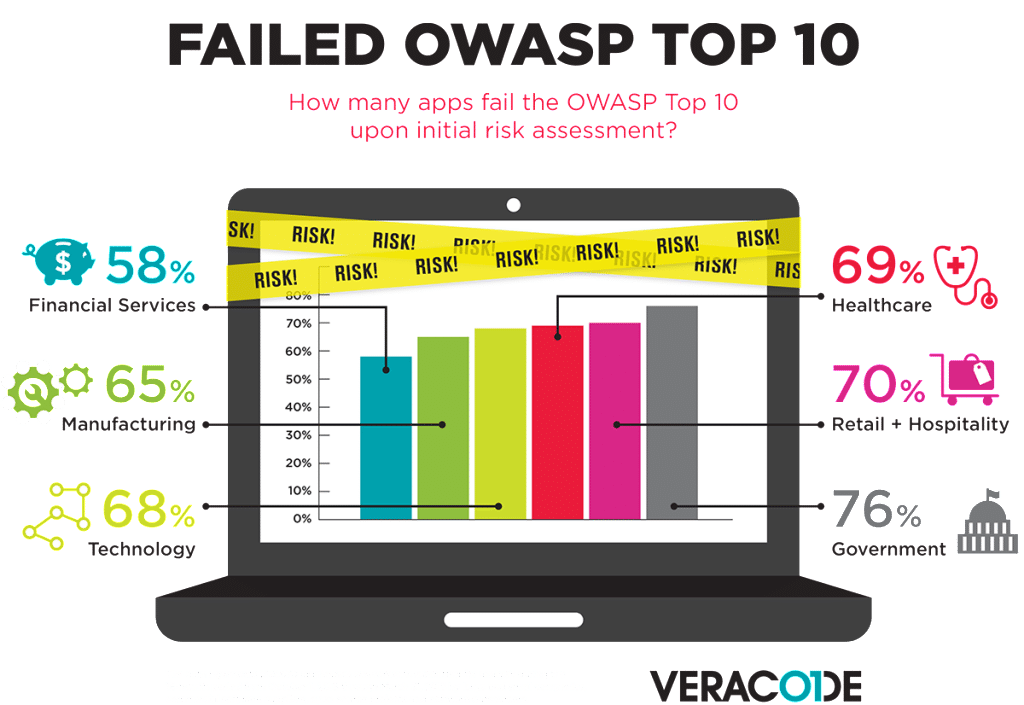
Survey Finds Government Application Security Wanting
In-brief: A survey of web and mobile applications by the firm Veracode finds that governments are the most likely to use insecure software, as measured against the OWASP (Open of Web Application Security Project) Top 10.
Updated: Google warns of unauthorized TLS certificates trusted by almost all OSes | Ars Technica
In-brief: Google warned its users that unauthorized digital certificates have been issued for several of its domains. The certificates are linked to an intermediary certificate authority for CNNIC, which administers China’s domain name registry. Updated with comment from Kevin Bocek of Venafi. Paul 3/27/2015
Update: Superfish is the Real End of SSL
In-brief: Outrage over Lenovo’s promotion of privacy busting adware continued to grow amid lawsuits and more spying revelations. The big question: is this the final – final straw for the beleaguered Secure Sockets Layer (SSL) technology? (Updated to add comment from Kevin Bocek of Venafi.)
Cat and Mouse: Web Attacks Increasingly Sidestep WAF Protections
Recently, the Akamai Threat Research Team unveiled a unique distributed brute force attack campaign targeting nearly five hundred WordPress applications. What’s interesting about this campaign? It clearly demonstrates how Web attackers are becoming more sophisticated, attempting to evade security controls – specifically Web Application Firewalls (WAFs) and rate control protections. A Short Primer to Brute-Force Attacks Brute force Web attackers attempt to gain privileged access to a Web application by sending a very large set of login attempts, within a short period of time. Using volumetric single source of attack is easily mitigated by blacklisting. Today’s brute force attacks are typically characterized by volumetric attacks coming from distributed IPs. In this way, if the attacker’s source IP is detected, they can still continue with the attack campaign by switching a source IP. As part of this cat-and-mouse evolution, WAFs are enhanced with several rate control measures that detect and block […]