In-brief: Pharmacy chain CVS and discount chain Costco acknowledged this week that a July security incident involving a third party firm that provides online photo processing and printing services resulted in the theft of some customer data. (Updated to add comment from Staples and CVS. PFR Sept. 16, 2015)
Tag: phishing
The Cost of Phishing? More than you think!
In-brief: A report from the Ponemon Institute puts the annual cost of phishing attacks at $300,000, much of it due to lost productivity. Can that number be believed? It’s hard to know.
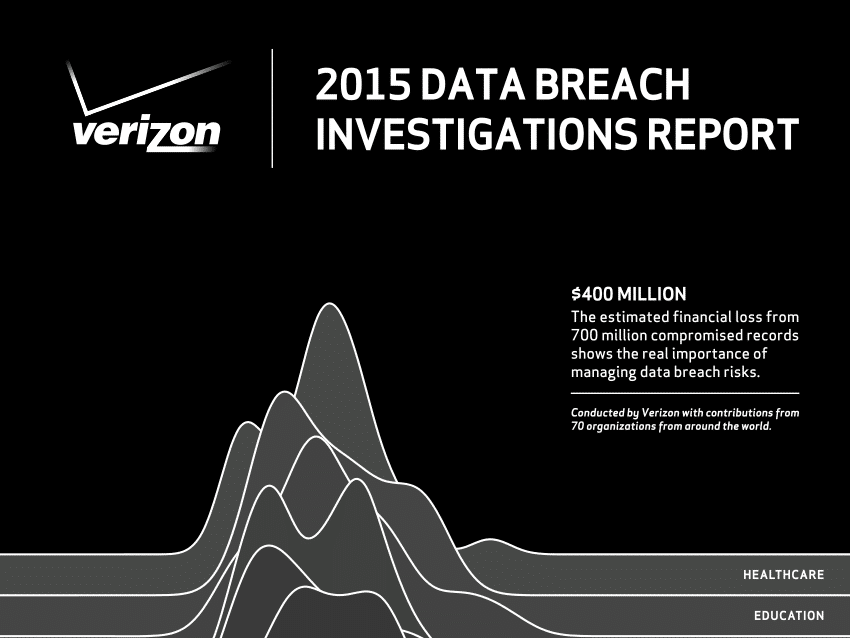
Verizon: Internet of Things Hacks Pose Little Risk – For Now
In-brief: Verizon said in its latest Data Breach Investigations Report that threats from Internet of Things technologies were more theory than practice in 2014, but that 2015 could see IoT devices play a role in breaches.
Wire Transfer Scam Shows Assertiveness Works with Phishing, Too
In-brief: Websense has uncovered a phishing scam that uses “urgent” e-mails from executives to fool employees into wiring money overseas.
Medical Information on Millions Stolen from Premera Blue Cross
In-brief: Premera Blue Cross said on Tuesday that it was the victim of a sophisticated attack. The hackers had access to Premera’s network for more than six months, stealing information on as many as 11 million members and employees.