In this week’s episode of the Podcast (#155): Jerome Segura of Malwarebytes joins us to talk about how disinformation campaigns and cyber crime are part of the same toxic cocktail in the world’s trouble spots, like Ukraine. Also: Adam Meyers of CrowdStrike joins us to talk about that company’s first ever report on mobile malware, which is gaining currency with advanced persistent threat (APT) groups.
Tag: Mobile Threats
Israeli Group Exploited WhatsApp to Spy on Users
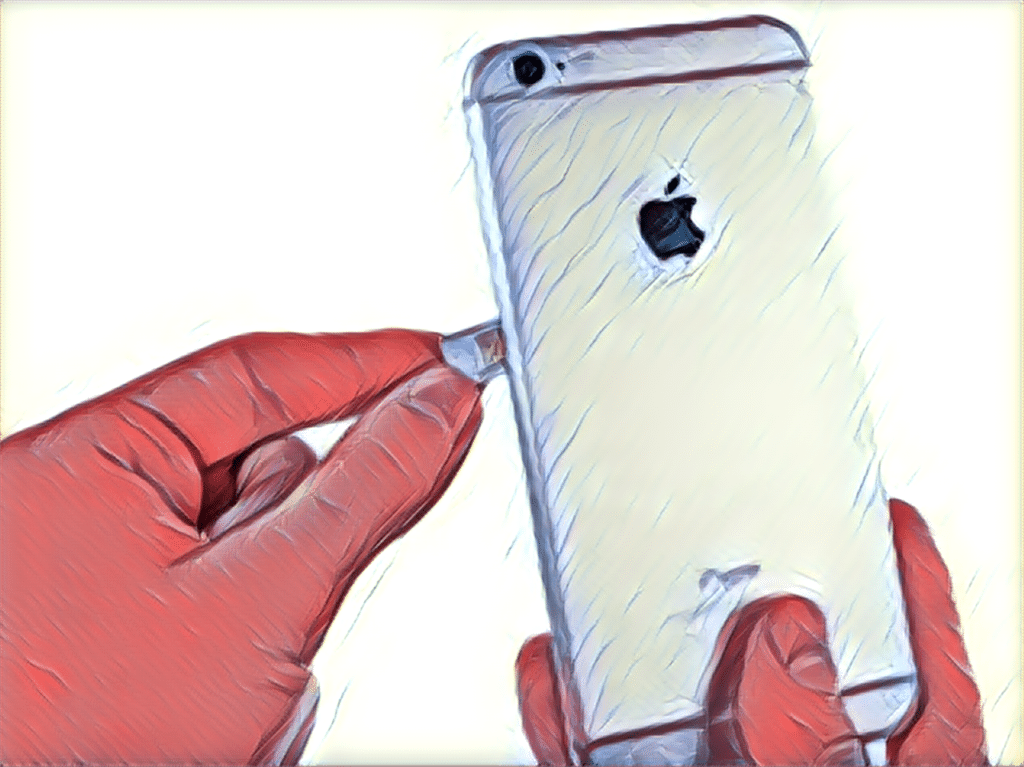
An Israeli firm has exploited a flaw in the popular messaging mobile app WhatsApp to plant spyware on iPhones and Android. One phone call is all it takes for software developed by the Israeli firm NSO Group to install itself on a vulnerable iPhone or Android device, according to a published report in the FT Times. The publication broke the news, saying it potentially affects 1.5 billion users of the Facebook-owned WhatsApp messaging application, on Monday. WhatsApp quickly issued a fix for the exploit, described in an alert on the Facebook website as “a buffer overflow vulnerability in WhatsApp VOIP stack” that allows for “remote code execution via specially crafted series of SRTCP packets sent to a target phone number.” “WhatsApp encourages people to upgrade to the latest version of our app, as well as keep their mobile operating system up to date, to protect against potential targeted exploits designed […]
Spotlight Podcast: Flashpoint’s Allison Nixon on SIM Swapping and the Looming Online Identity Crisis
Your smart phone does double and triple duty: letting you do banking, buy a cup of coffee, board a plane or access a sensitive online account. But that doesn’t mean that your phone number is equally as trustworthy. In this Spotlight Podcast, we speak with Flashpoint* head of research Allison Nixon about how a recent rash of SIM swapping attacks highlights a looming crisis in online identity.
Breaking the Ice on DICE: scaling secure Internet of Things Identities
In this Spotlight Podcast, sponsored by Trusted Computing Group*, Dennis Mattoon of Microsoft Research gives us the low-down on DICE: the Device Identifier Composition Engine Architectures, which provides a means of solving a range of security and identity problems on low cost, low power IoT endpoints. Among them: establishing strong device identity, doing device attestation and safe deployment at scale and verifying software updates.
Fitness apps: Good for your health, not so much for military security
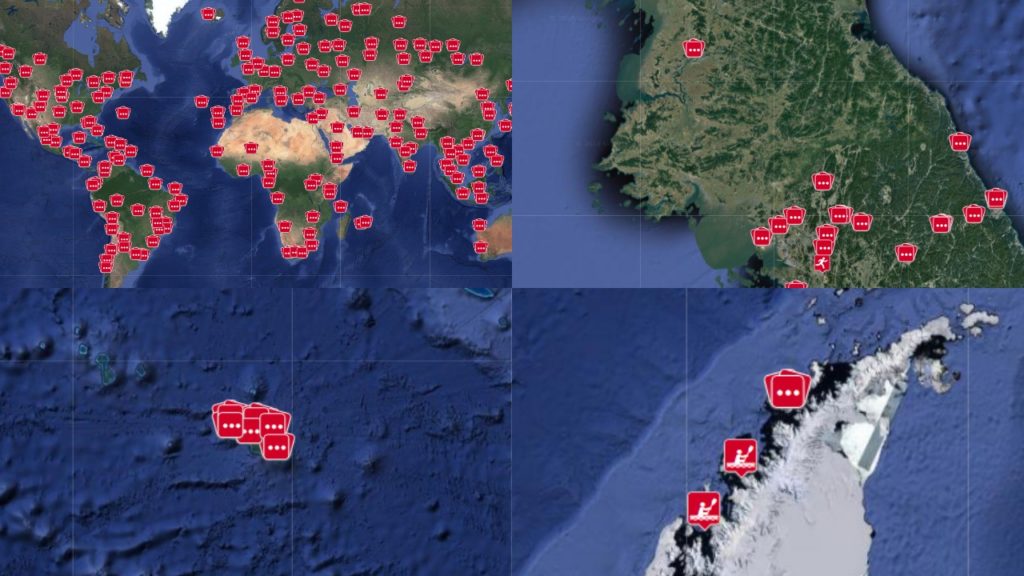
Fitness apps are proving to be a lot less beneficial to military security than they are for military fitness. That after researchers in the Netherlands discovered that data from the Polar fitness app revealed the homes and habits of those exercising in clandestine locations around the world, including intelligence agencies, military bases, nuclear weapons storage sites and embassies.