The Department of Homeland Security warned firms in the energy sector about new, targeted malware infecting industrial control systems and stealing data. DHS’s ICS CERT, the Industrial Control Systems Computer Emergency Response Team, said it is analyzing malware associated with an ICS-focused malware campaign. The malicious software, dubbed “Havex” that was being spread by way of phishing emails and so-called “watering hole” attacks that involved compromises of ICS vendor web sites. DHS was alerted to the attacks by researchers at the security firms Symantec (which dubbed the malware campaign “Dragonfly”) and F-Secure (“Havex”) -a remote access trojan (or RAT) that also acts as an installer (or “downloader”) – fetching other malicious applications to perform specific tasks on compromised networks. One of those additional payloads is a Trojan Horse program dubbed Karagany (by Symantec) that has been liked to prior attacks on energy firms. According to Symantec, the malware targeted energy grid operators, major electricity generation firms, […]
Tag: keylogger
Cisco: MS Word Macro Attacks Still Work Just Fine
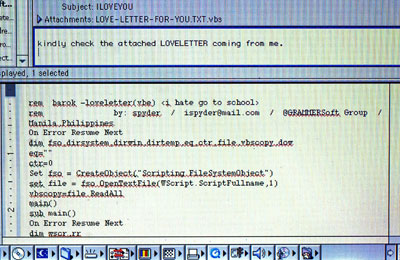
We like to throw around the term ‘Advanced Persistent Threat’ casually these days to refer to a whole range of sophisticated and persistent attacks – usually on high value targets. But a blog post today by Cisco Systems makes clear that many otherwise sophisticated attackers do just fine with some pretty low tech and old school methods. Case in point: an attack Cisco is dubbing “String of Paerls-” a series of attacks on companies involved in research and what Cisco calls the ‘industrial manufacturing vertical.’ According to the report, the attacks start with a decidedly old school attack: a Microsoft Word document that includes a malicious Office Macro.”When the victim opens the Word document, an On-Open macro fires, which results in downloadin and executable and launching it on the victim’s machine.” Now, macro-based attacks are truly vintage. They first came to light in the late 1990s, with the Melissa virus – an early and successful […]
China Hacking Indictments Day 2: Now For The Blowback
The big news yesterday was about the U.S. Justice Department announcing the first-ever criminal charges against a foreign country for cyberspying. The news today may well be about China (and other countries) taking retaliatory actions, including similar legal steps against individuals in this country, working on behalf of the NSA, CIA or other government agencies. The Justice Department on Monday announced that a grand jury in the Western District of Pennsylvania indicted five Chinese citizens (PDF) for charges that include computer hacking and economic espionage directed at six American companies in the nuclear power, metals and solar products industries. The indictment alleges that the five defendants conspired to hack into American companies on behalf of competitors in China, including state-owned enterprises. The stolen information included intellectual property that would allow the Chinese firms to better compete with their American competitors. The hackers also stole confidential information regarding business negotiations and other deals that would aid the Chinese […]
FireEye Report: Iranian Hacker Group Becoming More Sophisticated
A report from the security firm FireEye claims that hacking crews based in Iran have become more sophisticated in recent years. They are now linked to malicious software campaigns targeting western corporations and domestic actors who attempt to circumvent Internet filters put in place by the ruling regime. The report, dubbed “Operation Saffron Rose,”(PDF) was released on Tuesday. In a blog post accompanying the research, FireEye researchers say that it has identified a group of hackers it is calling the “Ajax Security Team” that appears to have emerged out of Iranian hacker forums such as Ashiyane and Shabgard. Once limited to website defacements, the Ajax team has graduated to malware-based espionage and other techniques associated with “advanced persistent threat” (APT) style actors, FireEye said. The researchers claim that the group has been observed using social engineering techniques to implant custom malware on victims’ computers. The group’s objectives seem to align with those […]
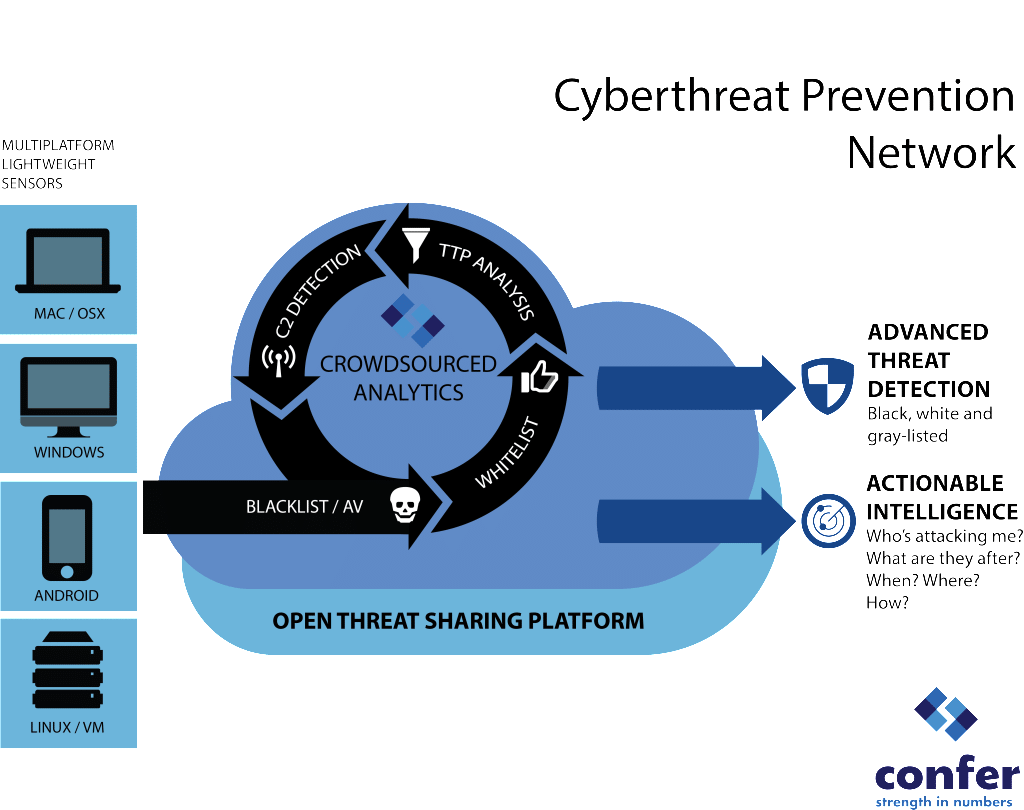
With $8m In Funding, Confer Taps Cloud, Crowd To Secure Endpoints
A new endpoint security startup, Confer, pulled the covers off its technology on Wednesday, announcing a new services-based endpoint protection product that it claims will provide better protection against malicious software and advanced attacks. Based in Waltham, Massachusetts, Confer has been in existence for just over a year and has received $8 million in venture funding from North Bridge Capital and Matrix Partners. The company’s cloud- and endpoint-based software enables organizations to collaborate to stop sophisticated attacks by sharing attack and malware anonymously with other Confer customers. The company said its technology will appeal to enterprise customers who have grown weary of malware infections that manage to bypass or elude traditional anti virus software. Confer is just the latest company to see dollar signs in corporations’ waning enthusiasm for anti malware software. Modern anti malware products are still focused on securing Windows endpoints. They are geared for use in the […]