The federal government charged two Iranian men for orchestrating a nearly three-year-long international hacking and extortion scheme that deployed ransomware which to date has caused more than $30 million in losses to its victims, which include hospitals, municipalities and public institutions.
Tag: Iran
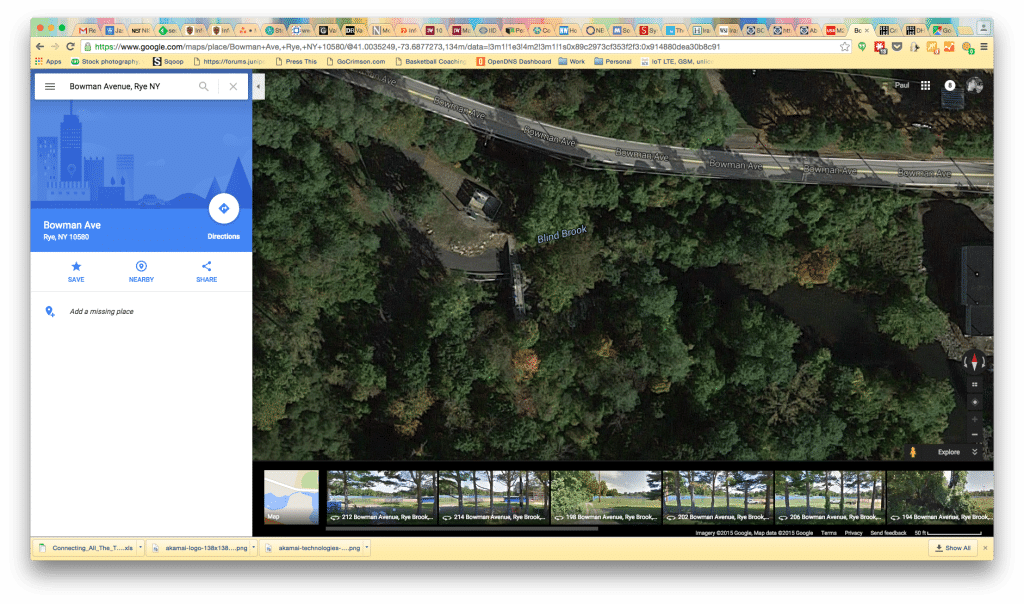
WSJ: Iranian Hackers Bust Into New York Dam
In-brief: The Wall Street Journal alleges that hackers with links to Iran may have compromised a small dam in Rye, New York. If true, the incident is just the latest evidence of information security vulnerabilities in U.S. critical infrastructure.
FireEye Report: Iranian Hacker Group Becoming More Sophisticated
A report from the security firm FireEye claims that hacking crews based in Iran have become more sophisticated in recent years. They are now linked to malicious software campaigns targeting western corporations and domestic actors who attempt to circumvent Internet filters put in place by the ruling regime. The report, dubbed “Operation Saffron Rose,”(PDF) was released on Tuesday. In a blog post accompanying the research, FireEye researchers say that it has identified a group of hackers it is calling the “Ajax Security Team” that appears to have emerged out of Iranian hacker forums such as Ashiyane and Shabgard. Once limited to website defacements, the Ajax team has graduated to malware-based espionage and other techniques associated with “advanced persistent threat” (APT) style actors, FireEye said. The researchers claim that the group has been observed using social engineering techniques to implant custom malware on victims’ computers. The group’s objectives seem to align with those […]
In Iran, New Data Wiping Malware on the Loose
Iran’s Computer Emergency Response Team (IR-CERT) issued a warning on Sunday about a newly discovered malicious program that is erasing hard drives on infected systems in that country – just the latest data-destroying malware to appear there. IR-CERT said that an investigation by its Maher center found that the malware “wipes files on different drives in various predefined times,” including disk partitions and user profiles. However, the malware isn’t widespread and doesn’t appear linked to “other sophisticated targeted attacks,” the alert said – in a possible reference to the Stuxnet and Flame malware, both of which targeted Iranian critical infrastructure. Subsequent analysis by independent security firms confirmed most of the details of the IR-CERT warning. Writing on Monday, Jamie Blasco of the firm Alien Vault said the malware was “just another wiping malware” and “very simple,” and could have been delivered in a variety of ways – from USB drive […]