In-brief: Is there cause for hope? A new analysis of a connected power drill by a researcher at DUO Security finds that it’s actually pretty secure. But challenges remain for connected device makers.
Web
Code Tutorials Spread Application Flaws Far and Wide
In-brief: Researchers at universities in Germany, working with the security firm Trend Micro, discovered more than 100 vulnerabilities in GitHub code repositories simply by looking for re-used code from tutorials and other free code samples. The same method could be harnessed by cyber criminals or other sophisticated attackers to find and exploit vulnerabilities in software applications, the researchers warned.
Hack of Dallas Sirens Not the First or Last on Emergency Systems, Experts Warn
In-brief: The weekend hack of civil defense sirens in Dallas, Texas is similar to two incidents in Illinois in 2012. The underlying problem? Woeful security for emergency alerting and other civil defense systems in the U.S., according to security experts.
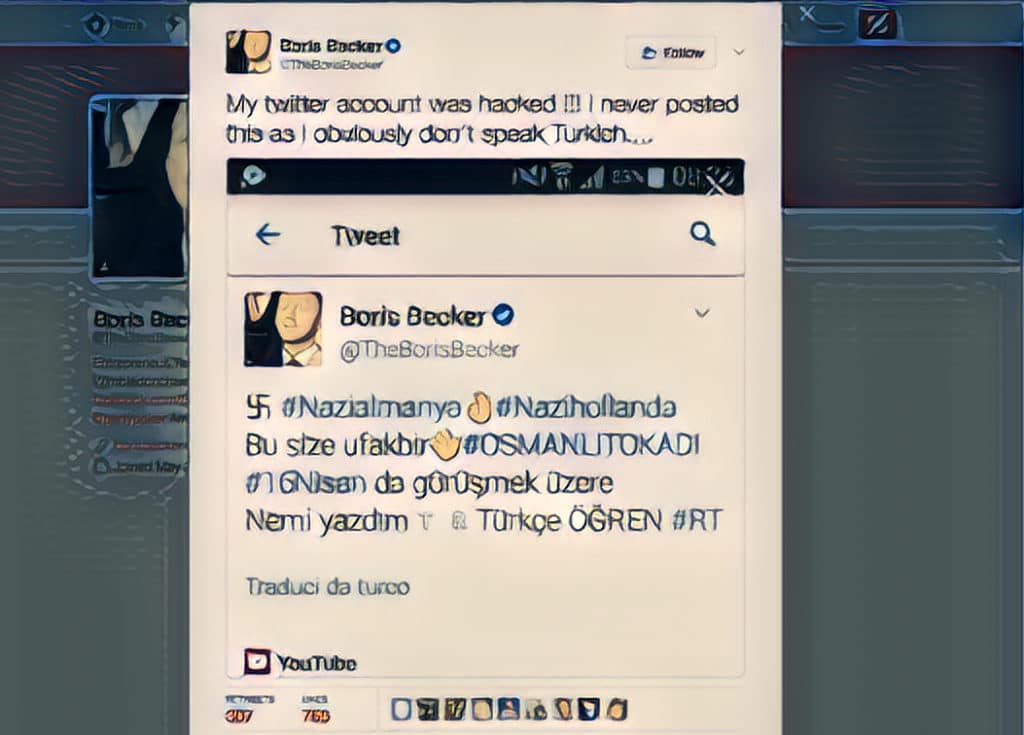
Twitter Hack is latest to underscore Third Party App Risk
In-brief: security experts are warning about the threat posed by third-party applications that tap into prominent social media platforms like Twitter after accounts belonging to media organizations and prominent personalities were hacked and hijacked to display messages accusing Dutch and German officials of Nazi sympathies.
Don’t Be The DNC: An Introduction to Enterprise Threat Hunting
In-brief: The New York Times expose on the hack of the Democratic National Committee is a case study in how not to respond to a cyber attack. In this video interview with Tim Bandos of Digital Guardian, we talk about how to do it right. His new ebook on hunting digital threats in the enterprise explains that incident response doesn’t have to cost a fortune.