It’s the end of another week and, as has become a pattern, we’re weighing the impact of another massive data breach: this one at Cupid Media, the owner of a network of dating web sites. According to a report on Krebsonsecurity.com, data on some 40 million Cupid Media customers turned up on the same servers that were found holding data stolen from Adobe Inc., PR Newswire and other victims. To get a handle on the impact of this breach and others like it, I invited Ted Julian, the Chief Marketing Officer of CO3 Systems, to talk about the recent string of embarrassing breaches and how companies go wrong (and sometimes right) in responding to them. Co3 sells a service that helps companies structure their response to data breaches and other adverse incidents. We also took the time to talk about the recent FTC Workshop on security and privacy on The […]
Video
Identity Management’s Next Frontier: The Interstate
Factory-installed and even aftermarket identity management applications may soon be standard components on automobiles, as the federal government looks for ways to leverage automation and collision avoidance technology to make the country’s highways and roadways safer. That’s the conclusion of a new report from the Government Accountability Office (GAO), which finds that vehicle to vehicle communications are poised to take off, but that significant security and privacy challenges must first be met, identity management top among them. The report, GAO 14-13 (PDF available here) takes the measure of what the GAO calls “Intelligent Transportation Systems,” including vehicle-to-vehicle (or V2V) technology. The GAO found that V2V technology that allows automobiles to communicate with each other in ways that can prevent accidents has advanced considerably in recent years. Automakers, working with the Department of Transportation, are testing the technology in real-world scenarios. However, the deployment of V2V technologies faces a number […]
Week In Security: NSA Spies on Yahoo & Google, Adobe Hack and Healthcare.gov
There’s nothing like a Sunday morning for looking back over the week’s events and trying to make sense of at all – or at least what sense there is to be had. This Sunday was no different – especially after a week that saw continued revelations stemming from Edward Snowden’s leak of classified intelligence on NSA spying, the massive hack of software maker Adobe. Then there was the botched rollout of the federal Healthcare.gov marketplace – which morphed into an even bigger, uglier problem as the week progressed. To help me sort it all out, I called on Nick Selby, the CEO of StreetCred Software and an authority on cyber security, law enforcement, government procurement, Russia, Germany, aviation, travel journalism and all manner of other topics. I love talking to Nick because his wealth of life and professional experience make him predictably unpredictable when it comes to interpreting current events. […]
BlueTooth on Your Defibrillator? The Case Against Wi-Fi
As more and more devices become networked, the use cases for wireless communications protocols like Bluetooth and NFC (Near Field Communications) multiply. Hardly a week goes by where some company figures out a way to pair wireless communications with some inanimate object or another. (Bluetooth bike locks, anyone?) But what happens when those wireless devices run critical infrastructure or life-saving technology like implanted medical devices? We learned earlier this week that no less than Dick Cheney was concerned enough about wireless attacks on his implanted defibrillator that he had the wireless management features of the device disabled, for fear they could be used in an assassination attempt. Security experts, like Dr. Kevin Fu at The University of Michigan, doubtful that such an attack was realistic, also refused to rule it out entirely. Given the many, proven tools and strategies for hacking wireless communications like Bluetooth, you might think that foregoing well […]
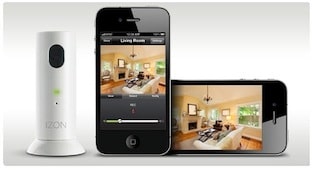
Exclusive: Apple Store Favorite IZON Cameras Riddled With Security Holes
It’s another day, another face-palm moment for the home surveillance camera industry. Just one month after the Federal Trade Commission (FTC) settled a complaint with the maker of SecurView, a line of poorly secured home surveillance cameras, a researcher at the firm Duo Security has found a slew of even more serious security holes in the IZON Camera – a popular product that is sold in Apple Stores and Best Buy, among others. A review by The Security Ledger found dozens of such systems accessible via the public Internet, in some cases allowing anyone to peer into the interiors of private residences and businesses. Mark Stanislav, the Security Evangelist at the firm Duo Security, presented the details of a security audit of the IZON camera at a security conference in New York on Tuesday. Stanislav documented troubling security lapses including a wide-open configuration with exposed ports for accessing the device […]