In-brief: three quarters of embedded systems that sport web interfaces tested by researchers at universities in Germany and France contained serious security vulnerabilities, according to a new study. The results raise more questions about the security of embedded devices including home routers and home surveillance cameras.
buffer overflow
IEEE Proposes Standards For Safe, Connected Health Products
In-brief: a new publication by IEEE lays out a “building code” for medical device makers to help address security and privacy issues in products.
NetUSB, IoT and Supply Chain Risk
If you want an object lesson in the dangers that await us on the Internet of Things, check out SEC Consult’s write up on NetUSB, a widely used technology developed by an obscure Taiwanese company that just happens to contain a nasty, remotely exploitable vulnerability. According to this alert, published on Tuesday, NetUSB “suffers from a remotely exploitable kernel stack buffer overflow” that could be used to run malicious code on affected devices. Even worse: the NetUSB component is ubiquitous – found in a long list of devices, from low-end wireless access points and broadband routers for small office and home office deployments to what SEC Consult called “high end devices…released very recently.” Networking devices from 26 vendors, including TP-Link, NetGear and others were found to use the NetUSB technology in their products. The vulnerability discovered by SEC Consult is straight-forward enough. According to their advisory, the NetUSB code does an inadequate […]
Ghost Vulnerability Replays Third Party Code Woes
In-brief: The security firm Qualys is warning of a serious and remotely exploitable vulnerability in a function of the GNU C Library (glibc) known as gethostbyname. The security hole raises more questions about dangers lurking in legacy, open source software.
Research Warns of Cyber-Physical Attacks Against Vessel Tracking System
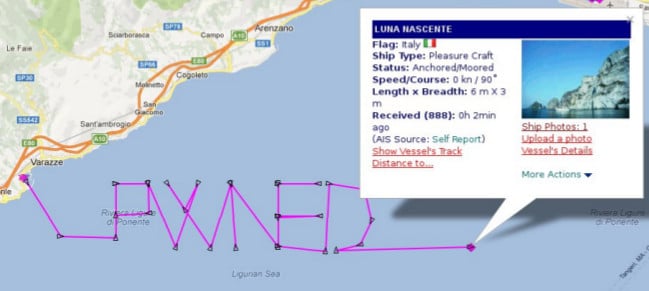
Researchers at Trend Micro report that an analysis of a vessel tracking system that is mandated on most large sea vessels has found that it is vulnerable to a range of possible software- and radio-based attacks. The vulnerabilities could be exploited in ‘cyber-physical’ attacks against the Automated Identification System (AIS) that directed ships off course or confused officials by mis-reporting the actual location of vessels, the researchers found. Trend Micro researchers Marco Balduzzi and Kyle Wilhoit presented their research at the Annual Computer Security Applications Conference (ACSAC) in New Orleans this month. AIS is a global system for tracking the movement of vessels. It is intended to supplement marine radar and relies on ship, land and satellite-based systems to exchange data on ships’ position, course and speed and is used for everything from collision avoidance to security, ship-to-ship communications and weather forecasting. AIS is required to be deployed on all passenger vessels and on international-voyaging ships […]