It’s ironic that government surveillance might push the public to embrace technology pioneered by the Department of Defense. But so it is: new metrics from The Tor Project show that use of the online anonymity service has exploded since early June: up more than 100 percent, from just over 500,000 global users to more than 1.2 million. Why the sudden surge in privacy conscious Internet users? It would be easy to connect the dots between revelations about the U.S. government’s omnibus data gathering program PRISM and the sudden desire of Internet users to sacrifice some speed and performance for the privilege of having their online doings passed through The Onion Router. Still, it’s not clear that this is the case. To be sure: growth is being seen across the board, not just in active users, but in the number of ToR clients running, the data suggests. There are steep increases […]
terrorism
Social Engineering Behind Syrian Hack Of NYT, Twitter?
How do you take some of the world’s largest online brands offline in a matter of minutes? If yesterday’s events are any guide, you do it by finding a gullible employee at vulnerable, downstream partner that those companies didn’t even know they had. That’s the lesson that appears to be emerging in the aftermath of yesterday’s chaotic tug of war between hackers who claim affiliation with The Syrian Electronic Army and some of the world’s leading online brands, including The New York Times, Twitter and Huffingtonpost.com. The attacks on Tuesday saw traffic to sites owned by those firms directed to web servers controlled by the attackers which displayed messages in support of the regime of embattled President Bashar al-Assad. According to a story in The New York Times, the attackers were able to compromise systems operated by Melbourne IT, an Australian domain registrar used by many prominent firms. With access to […]
Privacy: From Right To Fight
As more and more of our public and private spaces are equipped with remote sensing and surveillance technology, personal privacy – at least as it has been understood for the last two or three centuries – is endangered. The solution, of course, is through improved privacy legislation and, perhaps, a more expansive reading of the U.S. Constitution’s 4th Amendment protecting against search and seizure. But, with policymakers in Washington D.C. stuck in a rut, and many EU nations as hooked on surveillance as the U.S., the onus falls to individuals to do what they can. That’s the subject of my latest column for ITWorld, where I talk about what is likely to be the next stage in our society’s rapid evolution on matters of privacy and security, what I’ve termed “The Jamming Wars.” Like other social movements, this will be fueled by a growing rift between the law and a […]
U.S. Cyber Chief Says “Trust Us” On NSA Spying
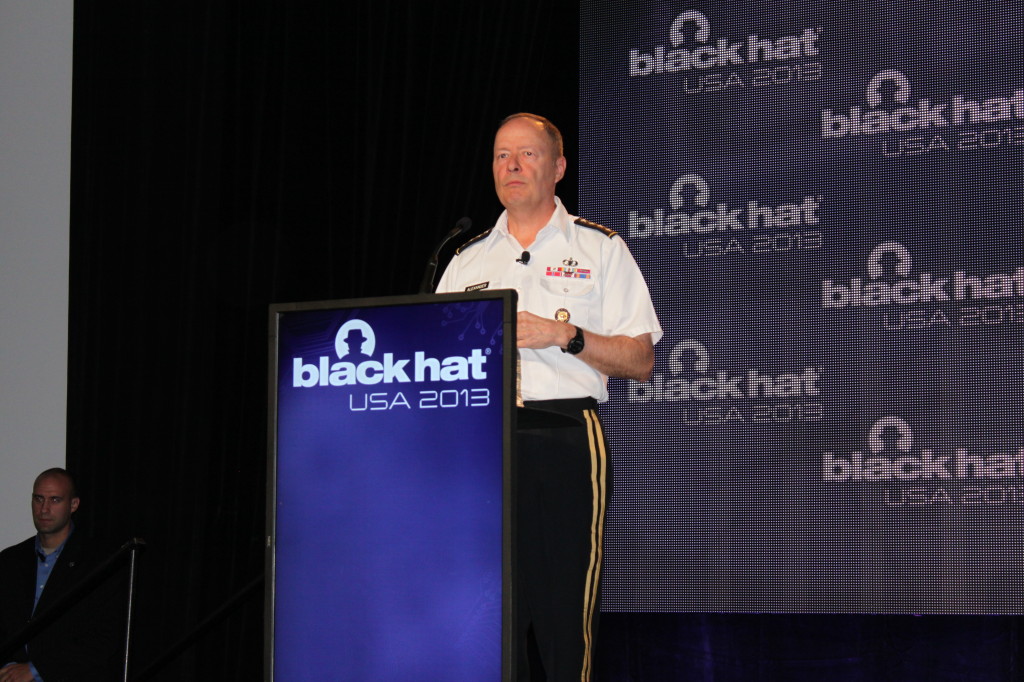
The head of the U.S. Cyber Command, Four-Star General Keith Alexander, told an audience of skeptical and sometimes hostile security experts and hackers that they should have faith that the U.S. National Security Agency (NSA) isn’t abusing its access to cell phone meta data and other online communications in its pursuit of terrorists who “live among us.” Speaking before a packed audience that included some of the country’s top computer security and privacy experts, Alexander spoke in measured tones about PRISM, the omnibus data collection program that was exposed in documents leaked by a former Booz Allen Hamilton contractor, Edward Snowden, saying that it had directly led to the disruption of 53 of 54 discrete “terrorist related activities” in the U.S., Europe, Asia and Africa since the September 11, 2001 terrorist attacks on New York and Washington, D.C. Adopting images and a tone common in the years immediately following 9/11, […]
Emergency Alert System: Vulnerable Systems Double, Despite Zombie Hoax
You’d think that the prospect of a zombie invasion would prompt our nation’s broadcasters and others who participate in the Emergency Alert System (EAS). Just the opposite is true. Months after a bogus EAS message warning about a zombie uprising startled residents in Michigan, Montana and New Mexico, the number of vulnerable EAS devices accessible from the Internet has increased, rather than decreased, according to data from the security firm IOActive. In a blog post Thursday, Mike Davis, principal research scientist at IOActive said that a scan of the public Internet for systems running versions of the Monroe Electronics software found almost double the number of vulnerable systems in July – 412 – as were found in April, when an IOActive scan of the public Internet using the Shodan search engine found only 222 vulnerable systems. IOActive first notified Monroe Electronics about vulnerabilities in its DASDECS product in January of […]