The folks over at Heise/c’t Magazin revealed leaked, classified documents to report on HACIENDA, a GCHQ program to deliver country-wide Internet reconnaissance for so-called “five eyes” nations, including the US (NSA), Canada and Australia. And, as Bruce Schneier points out – its not clear that these documents were from Edward Snowden’s trove of classified NSA materials. HACIENDA involves the large-scale use of TCP “port” scans to profile systems connected to the Internet, in addition to profiling of enabled applications. According to Heise, which published a classified slide deck. GCHQ claimed to have canvassed 27 countries through the program. A list of targeted services includes ubiquitous public services such as HTTP and FTP, SSH (Secure Shell protocol) and SNMP (Simple Network Management Protocol). The Heise report, prepared by Julian Kirsch, Christian Grothoff, Monika Ermert, Jacob Appelbaum, Laura Poitras and Henrik Moltke claim that HACIENDA’s goal was to perform active collection and map vulnerable services across […]
drive-by download
Popular Web Sites Still Getting Gamed in SEO Attacks
In this post, Security Ledger contributor Or Katz of Akamai provides details of how malicious actors are abusing redirect vulnerabilities in popular web sites to boost the reputation of malicious sites they control. One recent attack involved the compromise of some 4,000 vulnerable web applications for the purpose of pumping up the search engine ranking of more than 10,000 malicious web sites, Katz reveals.
Researchers Warn Of Flaws In Popular Password Managers
Researchers from the University of California, Berkeley have published a paper describing security holes in five, web-based password managers including LastPass, My1login and Roboform. According to the paper (PDF), four out of the five password managers inadvertently leaked a user’s credentials for stored web sites due to all-too-common web based security flaws like Cross Site Request Forgery (CSRF) and Cross Site Scripting (XSS). The researchers, Zhiwei Li, Warren He, Devdatta Akwawe and Dawn Song, all of the University of California Berkeley, said that they disclosed the holes in August of last year and that all of the affected firms and that all but one – NeedMyPassword – have since patched the vulnerabilities. All the password managers tested were found to contain one of a short list of security problems. Either they were vulnerable to classic web-based holes (like XSS), or they were found to be susceptible to user interface-focused attacks, like […]
Industrial Control Vendors Identified In Dragonfly Attack
Two of the three vendors who were victims of a targeted malware attack dubbed ‘Dragonfly’ by the security firm Symantec have been identified by industrial control system security experts. Writing on Tuesday, Dale Peterson of the firm Digitalbond identified the vendors as MB Connect Line, a German maker of industrial routers and remote access appliances and eWon, a Belgian firm that makes virtual private network (VPN) software that is used to access industrial control devices like programmable logic controllers. Peterson has also identified the third vendor, identified by F-Secure as a Swiss company, but told The Security Ledger that he cannot share the name of that firm. The three firms, which serve customers in industry, including owners of critical infrastructure, were the subject of a warning from the Department of Homeland Security. DHS’s ICS CERT, the Industrial Control Systems Computer Emergency Response Team, said it was alerted to compromises of the vendors’ by researchers […]
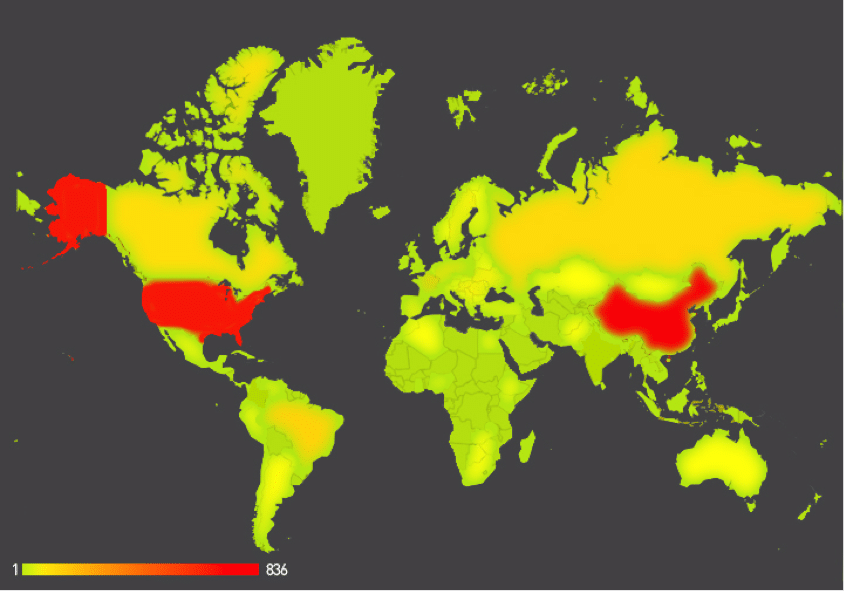
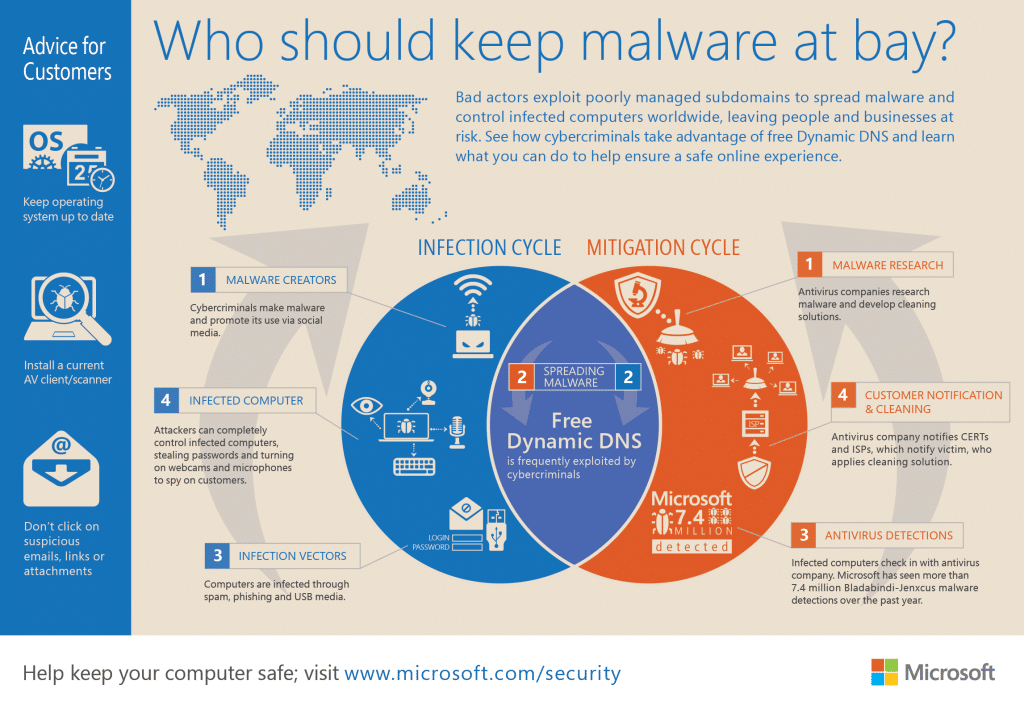
Microsoft Uses Courts To Take Down Malicious, Managed DNS Services
Microsoft Corp. has taken action against yet another cyber crime network, taking control of- and shutting down a managed DNS (domain name system) operated by the firm No-IP that were being abused by cyber criminals, the company said on Monday. The domains were associated with malware families named Jenxcus and Bladabindi that are believed to have infected on some 7.5 million systems, globally. The malicious programs – which are used to spy on the operators of infected systems – use Dynamic DNS services like NO-IP to communicate with command and control systems used to manage infected systems. Dynamic DNS makes the malicious systems more difficult to trace. In a post on Microsoft’s Digital Crimes Unit blog, Richard Domingues Boscovich, the company’s Assistant General Counsel said that the company had filed a civil case on June 19 naming two foreign nationals: Mohamed Benabdellah and Naser Al Mutairi along with a U.S. company, Vitalwerks Internet Solutions, LLC (doing […]