Three men have pleaded guilty in U.S. federal court for their role creating and renting out the Mirai botnet, which launched damaging denial of service attacks against the U.S. firm Dyn and other online properties, the website Krebs on Security reports.
Mirai
Research Finds Home Routers fill ranks of Fast Flux Botnets
Research from the firm Akamai finds cyber criminals are marrying vulnerable home routers to sophisticated “fast flux” command and control tools to create long-lived, cyber criminal infrastructure.
Kaspersky’s Cold War(e), Unpacking DOJ’s Encryption Talk and regulating IoT
In our latest Security Ledger Podcast we talk about Kaspersky Lab’s Cold War tinged smack down with for NSA analyst Dave Aitel of Immunity Inc. Also: Bruce Schneier weighs in on what has and hasn’t changed in the Trump DOJ’s take on strong encryption, while Josh Corman of PTC tells us that federal rules governing IoT security may be closer than we think.
A Year After Mirai: Insecure Devices are still a Huge Problem
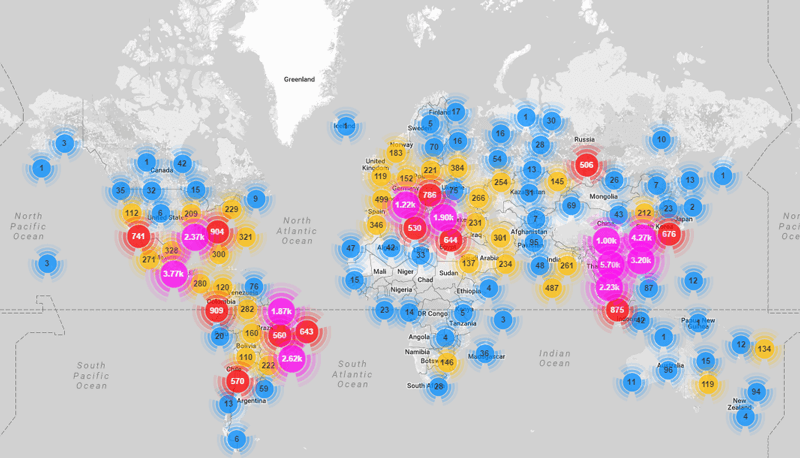
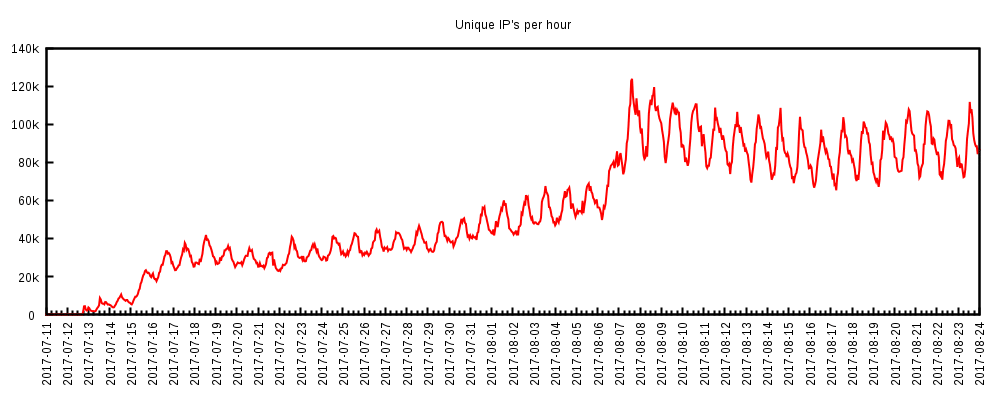
In-brief: A year after Mirai, as many as 100,000 devices, globally, may be running some version of the Mirai malware, while countless others are vulnerable to being enlisted in a Mirai-like attack. Worse: these systems may not be patched for “years,” according to the SANS Internet Storm Center.
Mirai Victim Dyn Joins Team to Take Down Android Botnet WireX
In-brief: Managed DNS firm Dyn, a victim of the Mirai botnet, got its revenge: taking part in a coordinated takedown of WireX, a botnet of compromised Android devices, according to an announcement Monday.