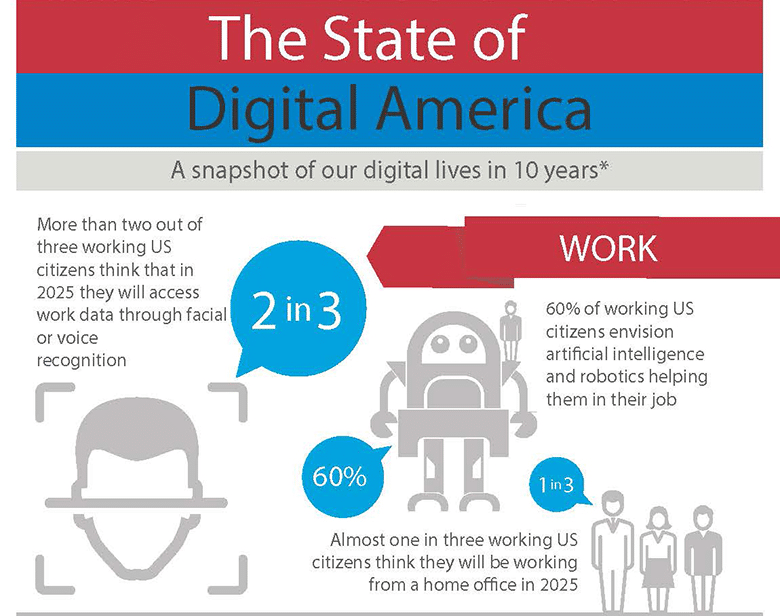
A new survey of consumer attitudes and expectations about technology finds that a strong majority of Americans expect wearable technology and biometric security to be common within the next decade. The survey, sponsored by the security company McAfee, asked 1,500 U.S. consumers about lifestyle and technology trends in the home and workplace. The results suggest that consumers are already adjusting their expectations about the future to include pervasive connectivity, a wealth of intelligent devices – and some of the problems that come with both. More than 60% of those surveyed by McAfee said they anticipate having connected appliances like refrigerators that will “automatically add food to a running grocery list if the product is running low.” A strong majority of those polled – 84% – said they were convinced their home security systems will be connected to their mobile device. “As technology, especially the Internet of Things, continues to rapidly advance and […]
two-factor authentication
Ahead of Apple’s Announcement: The Security Implications of Wearables | Trend Micro
The world’s attention will be focused on Apple this week and on the topic of wearables. In an event on Tuesday, the Cupertino company is planning to unveil the latest additions to its popular iPhone line along with a wearable device that most folks are just calling the ‘iWatch.’ But as Apple wrestles with the security of its growing stable of mobile devices and the cloud infrastructure that supports them, what will the impact of wearables be? Well, the folks over at Trend Micro are putting together a series of blog posts that look at that very question. Namely: the (information) security implications of wearables. It makes for some interesting reading. Among other things, Trend There are three very broad categories that we can use to describe what we are talking about. The posts, by Senior Threat Researcher David Sancho, break down the wearables space into three categories: ‘IN’ devices like sensors, ‘OUT’ […]
What Hollywood Can Teach Us: Passwords Matter More Than Ever
Andrey Belenko had what you might call a ‘brush with infamy’ earlier this week after a presentation he took part in on the security of Apple’s iCloud became a set piece in the news media scramble to identify the source of a huge trove of leaked celebrity photos – many depicting Hollywood A-List stars in various states of undress. “It’s not the kind of attention you want to receive,” said Belenko, a security researcher with the firm ViaForensics. “It’s all really creepy stuff.” Belenko’s link to the celebrity hacking scandal was a matter of happenstance. He was scheduled to give a presentation at a small, St. Petersburg multi-media conference, Chaos Constructions, over the weekend. Belenko was presenting research he had conducted a year earlier on the security of Apple’s KeyChain technology and iCloud – a talk he had given twice before in the last year. Prior to his talk, Belenko […]
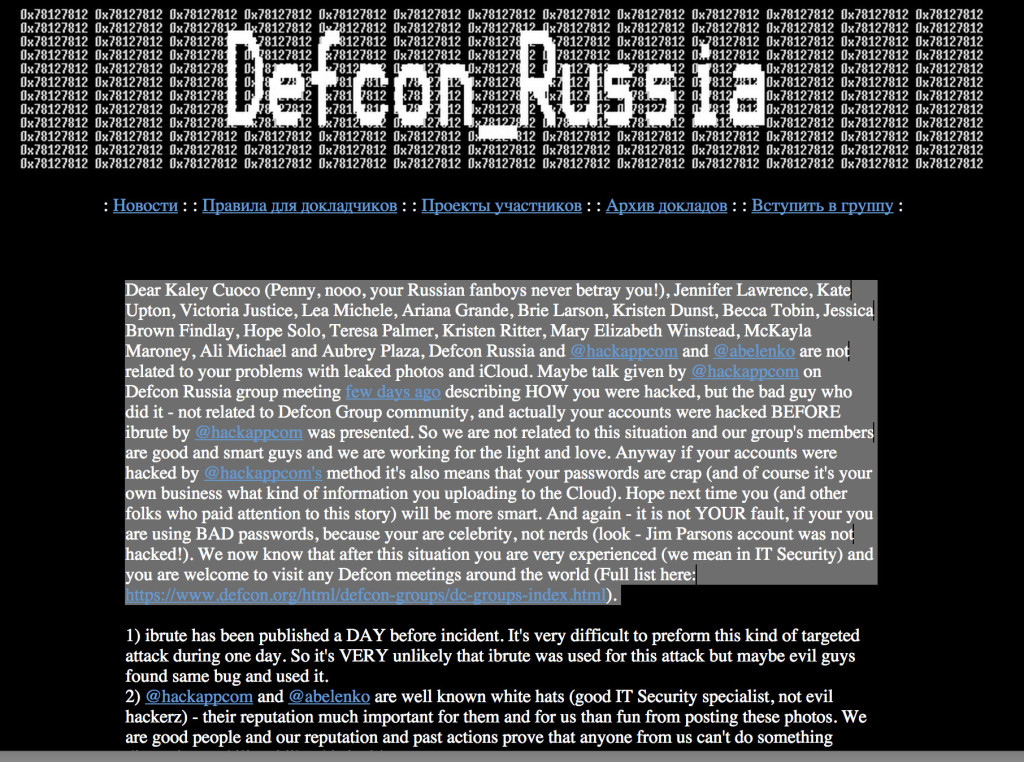
Hack Tool Authors Deny Link To Celeb Photo Leaks
With some of Hollywood’s biggest stars issuing statements on Monday condemning the leak of personal photographs online, attention has turned to identifying the source of the leaks. But more than 24 hours after the photos appeared, there are more questions than answers about its source. Early attention has focused on an automated tool that exploited an apparent vulnerability in Apple’s FindMyiPhone feature. But by Monday, there were denials from the makers of that tool that it played any role in the massive privacy breach that saw photos of A-list celebrities like Jennifer Lawrence, Kate Upton and others leaked online. Within hours of the photos’ appearance on the image sharing site 4chan, attention shifted to the cause of the leak and the coincidence of the leaked photos with the publication of iBrute, a simple tool available on GitHub in recent days. According to this published report by Owen Williams over at TheNextWeb, the […]
Researchers Warn Of Flaws In Popular Password Managers
Researchers from the University of California, Berkeley have published a paper describing security holes in five, web-based password managers including LastPass, My1login and Roboform. According to the paper (PDF), four out of the five password managers inadvertently leaked a user’s credentials for stored web sites due to all-too-common web based security flaws like Cross Site Request Forgery (CSRF) and Cross Site Scripting (XSS). The researchers, Zhiwei Li, Warren He, Devdatta Akwawe and Dawn Song, all of the University of California Berkeley, said that they disclosed the holes in August of last year and that all of the affected firms and that all but one – NeedMyPassword – have since patched the vulnerabilities. All the password managers tested were found to contain one of a short list of security problems. Either they were vulnerable to classic web-based holes (like XSS), or they were found to be susceptible to user interface-focused attacks, like […]