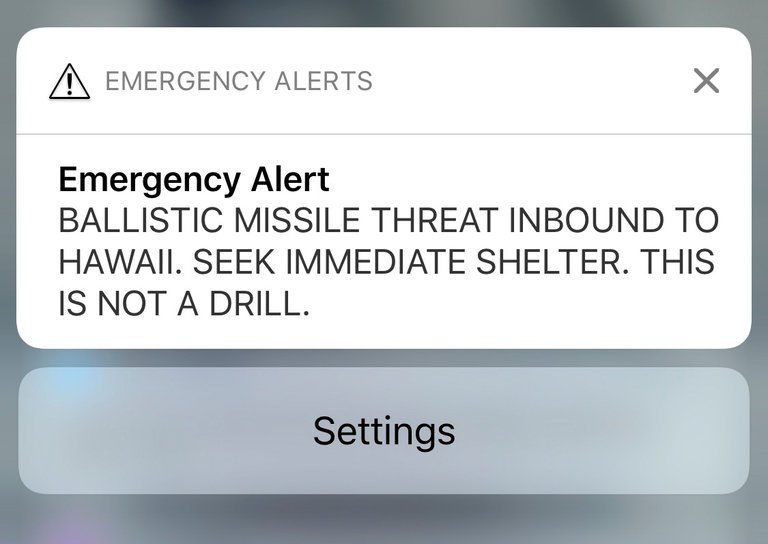
Two years after a false EAS alert about an incoming ICBM sowed terror in Hawaii, and seven years after security researchers warned about insecure, Internet connected Emergency Alert System (EAS) hardware, scores of the devices across the U.S. remain un-patched and vulnerable to cyber attack, according to security experts.
Shodan
Was the Devil’s Ivy Vulnerability a Dud? Don’t Count on It.
In-brief: The Devil’s Ivy vulnerability in the open source gSOAP library is widespread and supposedly trivial to exploit. So why, one month later, haven’t we seen any attacks? Is Devil’s Ivy a dud? ‘Don’t count on it,’ security experts tell us.
Heartbleed’s Heartburn: Why a 5 Year Old Vulnerability Continues to Bite
In-brief: more than three years after it was first discovered, the Heartbleed vulnerability in OpenSSL continues to plague organizations worldwide. Why has it been so hard to fix? In this Industry Perspective, Patrick Carey of the firm Black Duck talks about some of the complicating factors that make vulnerabilities like Heartbleed so hard to eradicate.
New Shodan Module hunts RATs
In-brief: a new service built into Internet of Things search engine Shodan promises to find the computers that control remote access trojans (RATs) – a common form of information stealing malware.
Brickerbot: and You will know It by the Trail of Linux Devices
In-brief: new botnets, dubbed “Brickerbot” were first spotted in recent weeks conducting what Radware termed “permanent denial of service” attacks: compromising and then destroying data on vulnerable connected endpoints.