Home routers and wi-fi access points are the canaries in the coal mine for security on the Internet of Things. Simply put: they’re ubiquitous, Internet-connected and innocuous. Unlike mobile phones, wi-fi routers aren’t in your pocket – buzzing and ringing and demanding your attention. In fact, it’s safe to be that the vast majority of Internet users are concerned wouldn’t know how to connect- and log in to their router if they had to. But appearances can deceive. Broadband routers are, indeed, mini computers that run a fully featured operating system and are perfectly capable of being attacked, compromised and manipulated. We have already seen examples of modern malware spreading between these devices. In March, the security firm Team Cymru published a report (PDF) describing what it claimed was a compromise of 300,000 small office and home office (SOHO) wireless routers that was linked to cyber criminal campaigns targeting online banking customers. In January, […]
source code
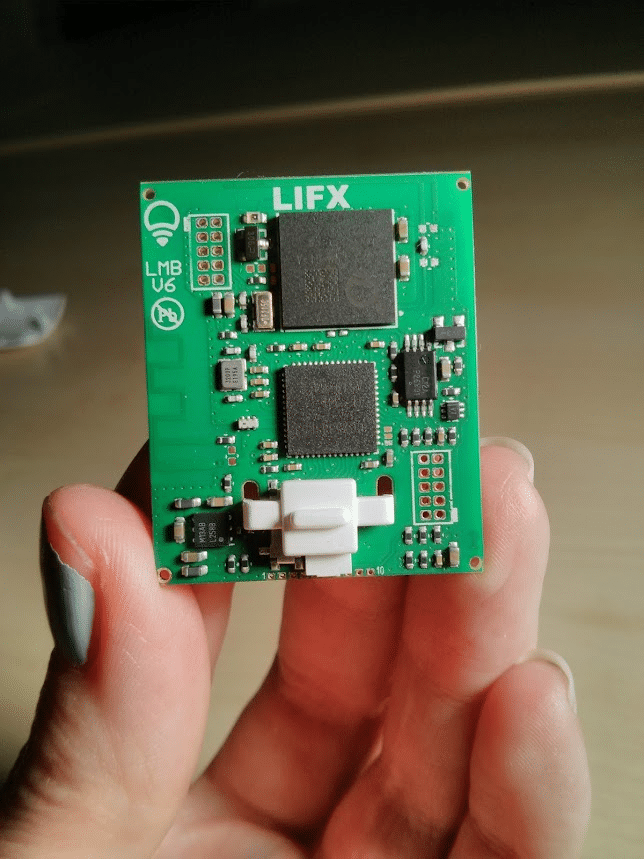
That LIFX Smart Lightbulb Hack Wasn’t Easy
If you’ve been following your Internet of Things security news, you probably read about the latest hack of a consumer-oriented ‘smart home’ device: Context Information Security’s analysis of security holes in LIFX-brand smart light bulbs. The top line on this is scary enough. As The Register reported: researchers at Context discovered that, by gaining access to a “master bulb” in LIFX deployments, they could control all connected lightbulbs and expose user network configurations. That’s scary – and recalls research on hacking Philips HUE light bulbs that was published last year. But read down in the Context research and you’ll realize that, while the LIFX technology wasn’t perfect, the job of hacking the technology wasn’t child’s play, either. LIFX connected its smart bulbs using a 6LoWPAN-based mesh network. The company made the mistake of transmitting most bulb-bulb communications in the clear, which made analyzing traffic sent between master- and slave bulbs easy. Context researchers found […]
Code Spaces Probably A ‘Target of Opportunity’
The spectacular collapse this week of Code Spaces, a cloud-based code repository, may have been the result of a an unspectacular “opportunistic” hack, rather than a targeted operation, according to one cloud security expert. The sudden demise of the online application repository has sent shock waves through the tech industry, laying bare what some say are lax practices among many cloud-based application and infrastructure providers. But the attack itself was almost certainly the result of a larger, indiscriminate cyber criminal campaign, said Jeff Schilling, the Chief Security Officer of Firehost, a Texas-based secure cloud provider. “This is something we pretty frequently: companies get held ransom with a DDoS attack, and if that doesn’t work, (the attackers) will resort to doing other things,” Schilling told The Security Ledger. But Code Spaces almost certainly wasn’t the only company the extortionists worked on, Schilling said. Instead, the company was likely caught up in a wide net […]
Video: The Internet of Things and Enterprise Risk
The Security Ledger recently hosted our inaugural event: The Security of Things Forum (SECOT). This was a high-energy, day long conference in Cambridge, Massachusetts, that brought together subject experts, executives and thought leaders from disparate areas like high tech, finance and industrial systems to talk about the tsunami of change that is the Internet of Things. One of the big questions hovering over the event: how will IoT technologies and services change the security paradigm that we’ve all be operating under- but especially in enterprises. In fact, IoT and enterprise was the topic of our very first discussion of the day: a panel chaired by Chris Rezendes of INEX Advisors, a leading consultancy focusing on IoT. SECoT Forum 2014 – Democratized Data, IOT and Enterprise Risk from Exhibitor Media Group on Vimeo It’s a really big and messy problem. As panelist Ken Pfeil of Pioneer Investments pointed out: the hack of […]
No Silver Bullet For Securing The Internet Of Things
On Wednesday we wrapped up the first-ever Security of Things Forum (SECoT) here in Boston, which was a great success. During a full day of talks and panel discussions, there was a lot of discussion – both on the stage and in the audience. Here are some (high level) take aways from the event: The Internet of Things will be different – really different The combination of technologies that we refer to as the Internet of Things is going to be transformative in ways that are profound. As I said in introductory comments: I see the net effect of this next phase of the Internet as being a leap forward, rather than incremental change – less “invention of the printing press” and more “invention of writing and counting systems.” Like Internet v.1, the exact direction that the Internet of Things will take is unclear. What is clear is that it […]