Dark Reading’s Kelly Higgins has a report about a discovery by a security researcher who has identified a worrying new trend: banking malware that is posing as legitimate ICS software updates and files in order to compromise systems that run manufacturing plants and other facilities. Higgins writes about research by Kyle Wilhoit, senior threat researcher with Trend Micro. Wilhoit claims to have found 13 different crimeware variants disguised as SCADA and industrial control system (ICS) software. The malware posed as human machine interface (HMI) products, including Siemens’ Simatic WinCC, GE’s Cimplicity, and as device drivers by Advantech. [Read more Security Ledger coverage of threats to SCADA and industrial control systems here.]The attacks appear to be coming from traditional cybercriminals rather than nation-state attackers. The motive, Wilhoit theorizes, is to make money, possibly by harvesting banking credentials or other financial information. Malicious software that can operate in industrial environments and critical infrastructure settings is an […]
CERT
Surprise: Branding a Bug is just as Hard as Branding Anything Else!
ZDNet’s @violetblue has a nice piece on the new fad for naming vulnerabilities – seen most recently with the OpenSSL Heartbleed vulnerability and the “Shellshock” vulnerability in Linux’s common BASH utility. As Blue notes, the desire to “brand” bugs “changes the way we talk about security” – in part by giving complex, technical flaws down a common referent. But does giving a bug a logo make it frivolous? As she notes: the penchant for naming vulnerabilities may stem not from a desire to trivialize them – but a very practical response to the need to keep track of so many security holes in software. Regardless, Heartbleed – and the marketing by the firm Codenomicon that surrounde it – was the bug that launched a thousand ships, including Shellshock, Sandworm, and more. Read more coverage of Heartbleed here. But, as with . As security research and incident response are becoming more lucrative, expect the masonry […]
Malware Campaign Against Industrial Systems Almost 3 Years Old
The U.S. Government’s Industrial Control System CERT (ICS-CERT) said on Thursday that a campaign targeting industrial control system (ICS) software began in January, 2012 and targeted industrial systems that were directly connected to the public Internet. ICS-CERT said in an alert published on Wednesday that “HMI” (or Human-Machine Interfaces) products from vendors including GE, Advantech/Broadwin and Siemens may have been infected with variants of the BlackEnergy malware since January, 2012. Infected firms were running versions of the GE’s Cimplicity, Advantech/Broadwin’s WebAccess or Siemens’ WinCC with what ICS-CERT called a “direct Internet connection.” In some cases, as with the GE Cimplicity attacks, hackers exploited a known vulnerability in the Cimplicity software to gain access. In others (as with WebAccess and WinCC) the method by which the software was compromised isn’t known, ICS-CERT said. CERT said it hasn’t documented any cases of control processes being modified by the malware. However, BlackEnergy is typically used […]
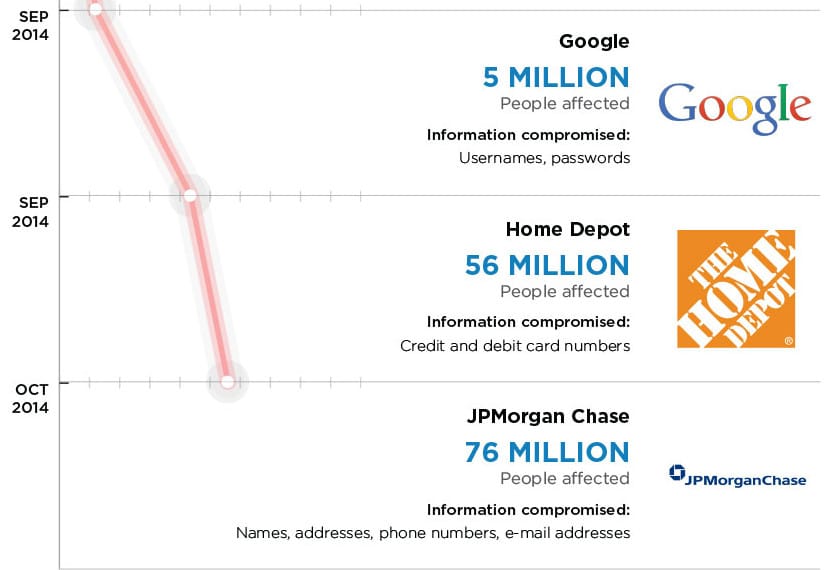
White House Cyber Chief: JP Morgan Underscores Critical Infrastructure Risk
The White House’s cyber security czar, Michael Daniel, said the Obama Administration is deeply concerned about the reported hack of systems belonging to banking giant JP Morgan Chase & Co. but sees the incident as part of a larger trend of attacks against U.S. critical infrastructure. Asked about the targeted attack against JP Morgan and other banks and financial institutions, Daniel said that the White House was concerned, but not surprised by the incident. “We have watched for several years the trend of malicious actors in cyber try to figure out how to target critical infrastructure,” he said. “Financial services is critical infrastructure.” The White House was concerned that a major U.S. bank would fall victim to hackers, but sees it in the context of a “broad trend,” rather than an isolated incident, he said. Speaking with Michael Farrell, the Cybersecurity Editor at Christian Science Monitor, Daniel hit on many of the now-common talking […]
Report: Home Depot A Common Thread Linking Trove Of Stolen Credit Cards
Home Depot said it is investigating “some unusual activity” on its networks and working with “banking partners and law enforcement,” after security blogger Brian Krebs named the company as a common thread connecting a trove of stolen credit card accounts that have appeared in underground forums. Krebs reported on Tuesday that “multiple banks” see evidence that Home Depot stores are the source of a “massive new batch” of stolen credit and debit cards that went on sale this morning in underground “carding” forums. The breach is believed to have affected Home Depot stores throughout North America – around 2,500 stores in total. The company has held off from confirming a breach, so far. And as of early Wednesday, Home Depot’s home page made no mention of the incident. In a statement to Reuters, spokesperson Paula Drake said that the company is holding off pending an internal investigation, and is working with law enforcement. […]