In-brief: The security firm Trend Micro announced that it was joining the AllSeen Alliance, an open source platform for connecting Internet of Things devices.
Trend Micro
The Deadly Game of Cyber Mis-Attribution | Digital Guardian
In-brief: Tools to attribute cyber attacks are still primitive – leading to potentially damaging mis-identification. (This post first appeared on the Digital Guardian blog.)
Research Warns of Cyber-Physical Attacks Against Vessel Tracking System
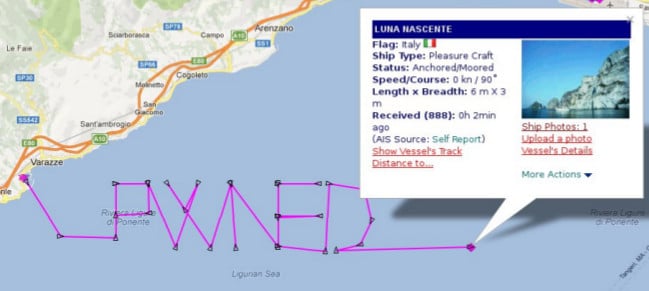
Researchers at Trend Micro report that an analysis of a vessel tracking system that is mandated on most large sea vessels has found that it is vulnerable to a range of possible software- and radio-based attacks. The vulnerabilities could be exploited in ‘cyber-physical’ attacks against the Automated Identification System (AIS) that directed ships off course or confused officials by mis-reporting the actual location of vessels, the researchers found. Trend Micro researchers Marco Balduzzi and Kyle Wilhoit presented their research at the Annual Computer Security Applications Conference (ACSAC) in New Orleans this month. AIS is a global system for tracking the movement of vessels. It is intended to supplement marine radar and relies on ship, land and satellite-based systems to exchange data on ships’ position, course and speed and is used for everything from collision avoidance to security, ship-to-ship communications and weather forecasting. AIS is required to be deployed on all passenger vessels and on international-voyaging ships […]
Infographic: Possible Attacks on The Internet of Things
The folks over at Trend Micro have put together a nice infographic that reminds us that all those smart devices connected to the Internet communicate through some well worn channels, namely: standard communications protocols like Wi-Fi, Ethernet and Bluetooth that connect devices to each other and the global Internet, as well as HTTP that are used to transmit data to and from cloud based resources like management interfaces. Of course those standard protocols also leave IoT devices vulnerable to a wide range of commodity attacks: from brute force password cracking on web based management consoles to Man in the Middle attacks that can sniff out authentication credentials and hijack sessions. Trend’s infographic does a good job of depicting the various layers in the IoT stack and some of the likely attack vectors for each layer. It also gives advice on how to protect yourself (use encryption, patch software vulnerabilities, disable unused ports). Nothing ground breaking […]
Ahead of Apple’s Announcement: The Security Implications of Wearables | Trend Micro
The world’s attention will be focused on Apple this week and on the topic of wearables. In an event on Tuesday, the Cupertino company is planning to unveil the latest additions to its popular iPhone line along with a wearable device that most folks are just calling the ‘iWatch.’ But as Apple wrestles with the security of its growing stable of mobile devices and the cloud infrastructure that supports them, what will the impact of wearables be? Well, the folks over at Trend Micro are putting together a series of blog posts that look at that very question. Namely: the (information) security implications of wearables. It makes for some interesting reading. Among other things, Trend There are three very broad categories that we can use to describe what we are talking about. The posts, by Senior Threat Researcher David Sancho, break down the wearables space into three categories: ‘IN’ devices like sensors, ‘OUT’ […]