Researchers at CyberX say they have found a way to sneak sensitive data off of industrial control system networks using radio frequency communications. The attack could be used to compromise so-called “air gapped” networks that are not connected to the Internet.
Siemens
Seven Years After Stuxnet, Industrial Firms Still Lag on Security
In-brief: Seven years after the Stuxnet worm proved that attacks on industrial environments was possible, many industrial and manufacturing firms still lack basic elements of an effective information security strategy, a new report finds.
Start-Up Claroty Has Eye On Industrial Control System Threats
In-brief: Claroty, an Israel-based start-up emerged from stealth mode on Tuesday, unveiling a new platform that it claims will help owners of industrial control systems detect threats and attacks by sophisticated adversaries.
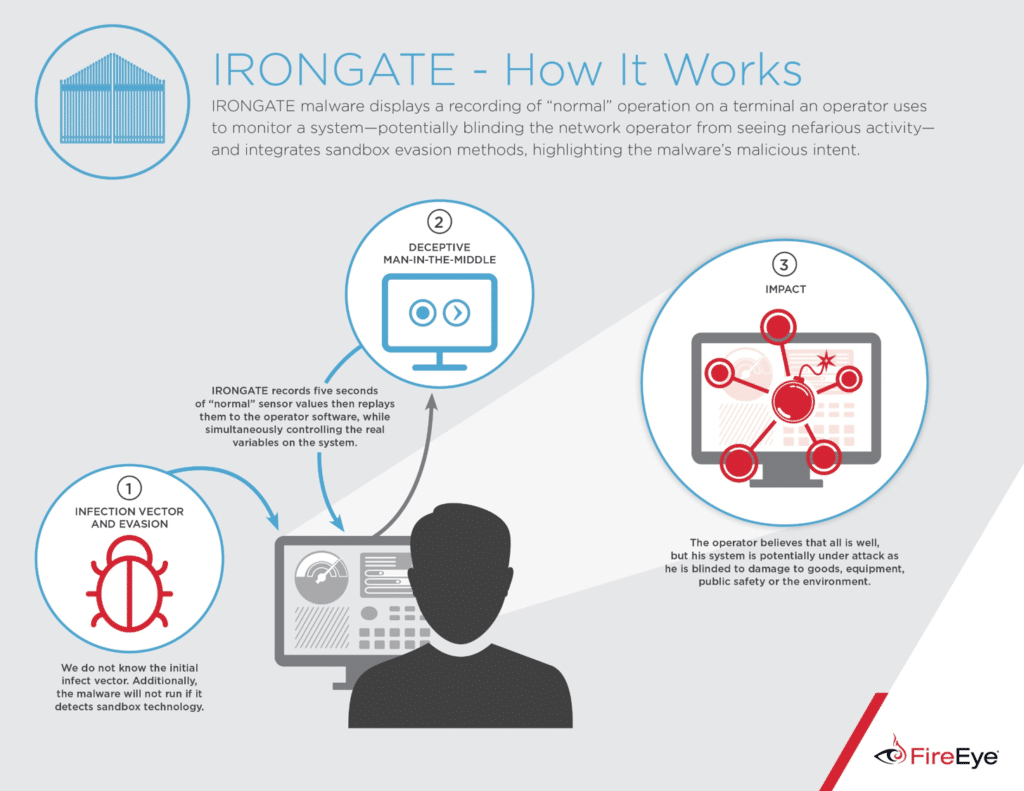
New Stuxnet-Like Industrial Control System Malware Ups The Ante
In-brief: Security firm FireEye is claiming to have discovered proof-of-concept malicious software that targets industrial control systems software that is used to operate critical infrastructure worldwide.
Banking Trojans Pose as SCADA Software to Infect Manufacturers
Dark Reading’s Kelly Higgins has a report about a discovery by a security researcher who has identified a worrying new trend: banking malware that is posing as legitimate ICS software updates and files in order to compromise systems that run manufacturing plants and other facilities. Higgins writes about research by Kyle Wilhoit, senior threat researcher with Trend Micro. Wilhoit claims to have found 13 different crimeware variants disguised as SCADA and industrial control system (ICS) software. The malware posed as human machine interface (HMI) products, including Siemens’ Simatic WinCC, GE’s Cimplicity, and as device drivers by Advantech. [Read more Security Ledger coverage of threats to SCADA and industrial control systems here.]The attacks appear to be coming from traditional cybercriminals rather than nation-state attackers. The motive, Wilhoit theorizes, is to make money, possibly by harvesting banking credentials or other financial information. Malicious software that can operate in industrial environments and critical infrastructure settings is an […]